2020JTWLB-个人CTF-MISC-memory
2020JTWLB-个人CTF-MISC-memory
- memory
- 题目分析
- 开始
- 1.题目
- 2.分析内存
- (1)查看镜像信息
- (2)查看进程
- (3)查找文件
- (4)把可疑文件dump出来
- (5)整理下文件
- (6)分析文件
- (7)查看剪贴板
- 3.base64替换表解密
- 4.解压zip,get flag
- 结论
每天一题,只能多不能少
memory
题目分析
1.volatility取证
2.base64换表解密
开始
1.题目
下载下来是一个vmem内存文件。
链接:百度网盘分享地址
提取码:rsmz
2.分析内存
(1)查看镜像信息
root@kali2019:~/CTF/JTWLB# volatility -f base9.vmem imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)AS Layer2 : FileAddressSpace (/root/CTF/JTWLB/base9.vmem)PAE type : No PAEDTB : 0x187000LKDBG : 0xf8000403d0a0LNumber of Processors : 1Image Type (Service Pack) : 1KPCR for CPU 0 : 0xfffff8000403ed00LKUSER_SHARED_DATA : 0xfffff78000000000LImage date and time : 2020-10-13 08:46:11 UTC+0000Image local date and time : 2020-10-13 16:46:11 +0800(2)查看进程
oot@kali2019:~/CTF/JTWLB# volatility -f base9.vmem --profile=Win7SP1x64 psscan
Volatility Foundation Volatility Framework 2.6
Offset(P) Name PID PPID PDB Time created Time exited
------------------ ---------------- ------ ------ ------------------ ------------------------------ ------------------------------
0x0000000002151b30 SearchProtocol 2084 940 0x000000002612e000 2020-10-13 08:25:04 UTC+0000
0x000000000237ab30 SearchFilterHo 2152 940 0x000000002d165000 2020-10-13 08:25:05 UTC+0000
0x00000000027739e0 dllhost.exe 1420 508 0x0000000019539000 2020-10-13 08:25:02 UTC+0000
0x0000000002ae24f0 mspaint.exe 2968 1184 0x000000001cbe0000 2020-10-13 08:45:57 UTC+0000
0x0000000002b62060 WmiPrvSE.exe 2488 628 0x0000000008165000 2020-10-13 08:25:20 UTC+0000
0x0000000005451b30 msdtc.exe 2064 508 0x0000000017144000 2020-10-13 08:25:04 UTC+0000
0x000000000be39850 mscorsvw.exe 884 508 0x000000002cb22000 2020-10-13 08:45:45 UTC+0000
0x000000000efe6b30 notepad.exe 2436 1184 0x00000000205ad000 2020-10-13 08:45:53 UTC+0000
0x00000000108e6920 cmd.exe 2760 1604 0x000000000380c000 2020-10-13 08:46:11 UTC+0000 2020-10-13 08:46:11 UTC+0000
0x0000000024e33b30 dllhost.exe 1468 508 0x00000000248a5000 2020-10-13 08:25:00 UTC+0000
0x0000000024eff480 WmiApSrv.exe 2600 508 0x0000000003c7f000 2020-10-13 08:25:21 UTC+0000
0x00000000282b5920 VSSVC.exe 2248 508 0x00000000177ca000 2020-10-13 08:25:06 UTC+0000
0x000000002d6aab30 VGAuthService. 1528 508 0x000000000a0e2000 2020-10-13 08:24:52 UTC+0000
0x000000002d73c6b0 vmtoolsd.exe 1604 508 0x0000000009a69000 2020-10-13 08:24:53 UTC+0000
0x000000002d793890 vmtoolsd.exe 1636 1184 0x0000000008e6a000 2020-10-13 08:24:54 UTC+0000
0x000000002d7a5650 ManagementAgen 1732 508 0x000000002b8f0000 2020-10-13 08:24:54 UTC+0000
0x000000002d825920 audiodg.exe 976 772 0x000000000848f000 2020-10-13 08:24:48 UTC+0000
0x000000002d8c4600 svchost.exe 752 508 0x000000000b7aa000 2020-10-13 08:24:49 UTC+0000
0x000000002d947700 dwm.exe 1172 864 0x000000000ab37000 2020-10-13 08:24:50 UTC+0000
0x000000002d94bb30 explorer.exe 1184 1164 0x0000000009428000 2020-10-13 08:24:50 UTC+0000
0x000000002d981b30 spoolsv.exe 1244 508 0x000000000c7f0000 2020-10-13 08:24:50 UTC+0000
0x000000002d9b1060 taskhost.exe 1236 508 0x000000000b042000 2020-10-13 08:24:50 UTC+0000
0x000000002d9bc380 svchost.exe 1308 508 0x0000000024886000 2020-10-13 08:24:50 UTC+0000
0x000000002db21330 svchost.exe 628 508 0x00000000131a7000 2020-10-13 08:24:47 UTC+0000
0x000000002db51b30 vmacthlp.exe 692 508 0x0000000015667000 2020-10-13 08:24:47 UTC+0000
0x000000002db5cb30 svchost.exe 724 508 0x000000001546e000 2020-10-13 08:24:48 UTC+0000
0x000000002db91740 svchost.exe 772 508 0x0000000015679000 2020-10-13 08:24:48 UTC+0000
0x000000002dbd5b30 svchost.exe 372 508 0x000000002b496000 2020-10-13 08:24:49 UTC+0000
0x000000002dbdab30 svchost.exe 908 508 0x0000000009c0b000 2020-10-13 08:24:48 UTC+0000
0x000000002dbee570 svchost.exe 864 508 0x0000000009b85000 2020-10-13 08:24:48 UTC+0000
0x000000002df1eb30 winlogon.exe 448 396 0x00000000164a7000 2020-10-13 08:24:29 UTC+0000
0x000000002df66b30 services.exe 508 412 0x0000000016ef9000 2020-10-13 08:24:32 UTC+0000
0x000000002df6db30 lsm.exe 528 412 0x00000000148a4000 2020-10-13 08:24:33 UTC+0000
0x000000002df77910 lsass.exe 516 412 0x000000001081c000 2020-10-13 08:24:33 UTC+0000
0x000000002e003810 csrss.exe 352 344 0x0000000018cc9000 2020-10-13 08:24:25 UTC+0000
0x000000002e0aa610 WmiPrvSE.exe 1520 628 0x000000001df53000 2020-10-13 08:25:00 UTC+0000
0x000000002e0db060 SearchIndexer. 940 508 0x00000000034aa000 2020-10-13 08:25:01 UTC+0000
0x000000002e84d670 smss.exe 268 4 0x000000001ff53000 2020-10-13 08:24:06 UTC+0000
0x000000002eaa2330 svchost.exe 2656 508 0x0000000028c15000 2020-10-13 08:45:45 UTC+0000
0x000000002ec6b9e0 wininit.exe 412 344 0x0000000017fcf000 2020-10-13 08:24:28 UTC+0000
0x000000002f388060 csrss.exe 404 396 0x0000000017ca1000 2020-10-13 08:24:28 UTC+0000
0x000000002f890630 svchost.exe 2940 508 0x000000001264f000 2020-10-13 08:45:57 UTC+0000
0x000000002f893060 mscorsvw.exe 1964 2292 0x000000001d7a1000 2020-10-13 08:46:11 UTC+0000 2020-10-13 08:46:11 UTC+0000
0x000000002f89d060 svchost.exe 2544 508 0x000000002f747000 2020-10-13 08:45:49 UTC+0000
0x000000002f8a7b30 mscorsvw.exe 2704 2292 0x0000000007aa9000 2020-10-13 08:46:11 UTC+0000
0x000000002f8f9630 7zFM.exe 1048 1184 0x000000002c465000 2020-10-13 08:46:06 UTC+0000
0x000000002f98d900 ipconfig.exe 1028 2760 0x0000000011ecb000 2020-10-13 08:46:11 UTC+0000 2020-10-13 08:46:11 UTC+0000
0x000000002fce8b30 mscorsvw.exe 2292 508 0x000000002c24c000 2020-10-13 08:45:46 UTC+0000
0x000000002fd3c750 sppsvc.exe 2508 508 0x00000000049d1000 2020-10-13 08:45:48 UTC+0000
0x000000002fd52060 conhost.exe 2400 352 0x0000000008211000 2020-10-13 08:46:11 UTC+0000 2020-10-13 08:46:11 UTC+0000
0x000000002ff2a990 System 4 0 0x0000000000187000 2020-10-13 08:24:06 UTC+0000
(3)查找文件
root@kali2019:~/CTF/JTWLB# volatility -f base9.vmem --profile=Win7SP1x64 filescan | grep -E 'jpg|png|jpeg|bmp|gif|zip|txt'
发现可疑文件
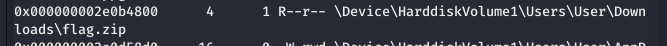
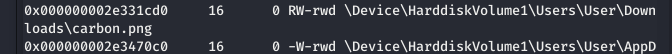

(4)把可疑文件dump出来
password.txt
volatility -f base9.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000002d2d9ea0 --dump-dir=./4
carbon.png
volatility -f base9.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000002d813d50 --dump-dir=./4
flag.zip
volatility -f base9.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000002e0b4800--dump-dir=./4
(5)整理下文件

carbon.png:

password.txt:
flag.zip
(6)分析文件
flag.zip里面肯定就是flag了。问题是加密了。
carbon.png肯定是个码表。看起来像是base。(事后诸葛亮。。。。)
pasword.txt却看不出来是什么。。。
根据我的推测,应该是ntfs流隐写,但是恢复不出来。
(7)查看剪贴板
经过大神的指点,原来密文是要通过剪贴板来查看。
root@kali2019:~/CTF/JTWLB# volatility -f base9.vmem --profile=Win7SP1x64 clipboard
Volatility Foundation Volatility Framework 2.6
Session WindowStation Format Handle Object Data
---------- ------------- ------------------ ------------------ ------------------ --------------------------------------------------1 WinSta0 CF_UNICODETEXT 0x2016d 0xfffff900c06f7e50 1CoiTFbWq0srIFGY 1 WinSta0 CF_TEXT 0x10 ------------------ 1 WinSta0 0x3016bL 0x200000000000 ------------------ 1 WinSta0 CF_TEXT 0x1 ------------------ 1 ------------- ------------------ 0x3016b 0xfffff900c06e8230
找到可疑密文:
1CoiTFbWq0srIFGY
3.base64替换表解密
文件名就是base。所以考虑是base64替换表解密。
上脚本:
#!python3
# -*- coding: utf-8 -*-
# @Time : 2020/10/23 23:02
# @Author : A.James
# @FileName: tt.pyimport base64str1 = "1CoiTFbWq0srIFGY"string1 = "9ElQCwNF7DYVIa5KATUPzi1WqbtphxLyMRkHsjmZ3GucBXefd4S0J8gn2r6Ovo+/"
string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"print (base64.b64decode(str1.translate(str.maketrans(string1,string2))))
得到:
b'XOUDvWc990zJ'
4.解压zip,get flag
flag{8c99bf86-2504-4eed-9df1-c5aa30ce3d51}
结论
巨坑,一直在纠结password.txt。结果密文是在剪贴板。然后就是base64替换表解密。巨坑。
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!