ssl安全配置关于扫描出某个端口的漏洞的解决方式
在自己的产品在适配不同的用户场景时,经常遇到,用户扫描出安全漏洞的问题,以下只是记录一下,自己解决某个用户场景,扫描出某个端口的安全漏洞的解决方式
问题背景:自己的某款产品由不同的组件组成,由kamailio,nginx,srs,rtpproxy组成的一套媒体服务系统,用户在扫描这个产品时,扫描出了,某个端口的漏洞,比如有一套nginx,用户扫描出了5061/tcp的端口的安全漏洞,从漏洞报告里可以看出
'Anonymous' cipher suites accepted by this service via the TLSv1.0 pr otocol‘ 是启用某些ssl的加密套件的漏洞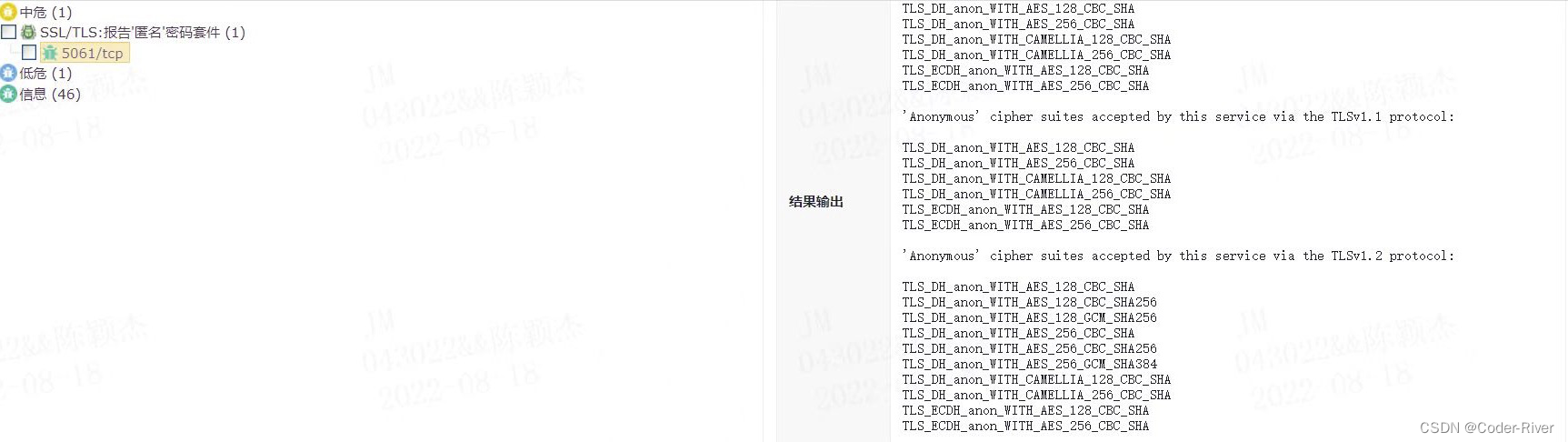
在自己的环境里,用nmap扫描该5061端口
nmap -sV -p 5061 --script ssl-enum-ciphers 172.24.0.104扫描出的结果
Starting Nmap 6.40 ( http://nmap.org ) at 2021-10-21 14:52 CST
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 0.49 seconds
[root@4a04eab572fc /]# ip a
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00inet 127.0.0.1/8 scope host lovalid_lft forever preferred_lft forever
20: eth0@if2: mtu 1500 qdisc noqueue state UNKNOWN group default link/ether 02:42:ac:18:00:68 brd ff:ff:ff:ff:ff:ff link-netnsid 0inet 172.24.0.104/24 brd 172.24.0.255 scope global eth0valid_lft forever preferred_lft forever
[root@4a04eab572fc /]# nmap -sV -p 5061 --script ssl-enum-ciphers 172.24.0.104Starting Nmap 6.40 ( http://nmap.org ) at 2021-10-21 14:53 CST
Nmap scan report for 4a04eab572fc (172.24.0.104)
Host is up (1600s latency).
PORT STATE SERVICE VERSION
5061/tcp open ssl/sip-tls?
| ssl-enum-ciphers:
| SSLv3: No supported ciphers found
| TLSv1.0:
| ciphers:
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| TLS_DH_anon_WITH_AES_128_CBC_SHA - broken
| TLS_DH_anon_WITH_AES_256_CBC_SHA - broken
| TLS_DH_anon_WITH_CAMELLIA_128_CBC_SHA - broken
| TLS_DH_anon_WITH_CAMELLIA_256_CBC_SHA - broken
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDH_anon_WITH_AES_128_CBC_SHA - broken
| TLS_ECDH_anon_WITH_AES_256_CBC_SHA - broken
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| compressors:
| NULL
| TLSv1.1:
| ciphers:
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| TLS_DH_anon_WITH_AES_128_CBC_SHA - broken
| TLS_DH_anon_WITH_AES_256_CBC_SHA - broken
| TLS_DH_anon_WITH_CAMELLIA_128_CBC_SHA - broken
| TLS_DH_anon_WITH_CAMELLIA_256_CBC_SHA - broken
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDH_anon_WITH_AES_128_CBC_SHA - broken
| TLS_ECDH_anon_WITH_AES_256_CBC_SHA - broken
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| compressors:
| NULL
| TLSv1.2:
| ciphers:
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 - strong
| TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 - strong
| TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 - strong
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| TLS_DH_anon_WITH_AES_128_CBC_SHA - broken
| TLS_DH_anon_WITH_AES_128_CBC_SHA256 - broken
| TLS_DH_anon_WITH_AES_128_GCM_SHA256 - broken
| TLS_DH_anon_WITH_AES_256_CBC_SHA - broken
| TLS_DH_anon_WITH_AES_256_CBC_SHA256 - broken
| TLS_DH_anon_WITH_AES_256_GCM_SHA384 - broken
| TLS_DH_anon_WITH_CAMELLIA_128_CBC_SHA - broken
| TLS_DH_anon_WITH_CAMELLIA_256_CBC_SHA - broken
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 - strong
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 - strong
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 - strong
| TLS_ECDH_anon_WITH_AES_128_CBC_SHA - broken
| TLS_ECDH_anon_WITH_AES_256_CBC_SHA - broken
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA256 - strong
| TLS_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA256 - strong
| TLS_RSA_WITH_AES_256_GCM_SHA384 - strong
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| compressors:
| NULL
|_ least strength: broken
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :
SF-Port5061-TCP:V=6.40%T=SSL%I=7%D=10/21%Time=61710E79%P=x86_64-redhat-lin
SF:ux-gnu%r(SIPOptions,20A,"SIP/2\.0\x20478\x20Unresolvable\x20destination
SF:\x20\(478/SL\)\r\nVia:\x20SIP/2\.0/TCP\x20nm;branch=foo;rport=45004;rec
SF:eived=172\.24\.0\.104\r\nFrom:\x20;tag=root\r\nTo:\x20;tag=6c98e1cb71aad21e8ecfc5e73ec5c3a2\.1e840000\r\nCall-ID:\x205
SF:0000\r\nCSeq:\x2042\x20OPTIONS\r\nContent-Length:\x200\r\n\r\nSIP/2\.0\
SF:x20478\x20Unresolvable\x20destination\x20\(478/TM\)\r\nVia:\x20SIP/2\.0
SF:/TCP\x20nm;branch=foo;rport=45004;received=172\.24\.0\.104\r\nFrom:\x20
SF:;tag=root\r\nTo:\x20;tag=bfd39b48636a9af5c63b59
SF:9e1a756d31-1e840000\r\nCall-ID:\x2050000\r\nCSeq:\x2042\x20OPTIONS\r\nC
SF:ontent-Length:\x200\r\n\r\n")%r(GenericLines,2,"\r\n");Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 130.72 seconds 查看nmap扫描的出来的broken和用户的扫描出来的漏洞,基本上是一致的
然后查看5061端口是那个组件的服务监听端口
netstat -tunlp查看输出结果:
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 262/nginx: master p
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 262/nginx: master p
tcp 0 0 0.0.0.0:8081 0.0.0.0:* LISTEN 262/nginx: master p
tcp 0 0 0.0.0.0:8082 0.0.0.0:* LISTEN 262/nginx: master p
tcp 0 0 0.0.0.0:9080 0.0.0.0:* LISTEN 262/nginx: master p
tcp 0 0 0.0.0.0:3001 0.0.0.0:* LISTEN 262/nginx: master p
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 262/nginx: master p
tcp 0 0 172.24.0.104:5060 0.0.0.0:* LISTEN 15344/kamailio
tcp 0 0 172.24.0.104:5061 0.0.0.0:* LISTEN 15344/kamailio
tcp 0 0 127.0.0.11:45001 0.0.0.0:* LISTEN -
tcp6 0 0 :::80 :::* LISTEN 262/nginx: master p
tcp6 0 0 :::8080 :::* LISTEN 262/nginx: master p
tcp6 0 0 :::8081 :::* LISTEN 262/nginx: master p
tcp6 0 0 :::9080 :::* LISTEN 262/nginx: master p
tcp6 0 0 :::3001 :::* LISTEN 262/nginx: master p
tcp6 0 0 :::443 :::* LISTEN 262/nginx: master p
tcp6 0 0 :::8003 :::* LISTEN 180/server
udp 0 0 127.0.0.11:53623 0.0.0.0:* -
udp 0 0 172.24.0.104:22222 0.0.0.0:* 388/rtpproxy
udp 0 0 0.0.0.0:56044 0.0.0.0:* 296/python
udp 0 0 127.0.0.1:7722 0.0.0.0:* 296/python 可以看到5061/tcp是kamailio的服务监听端口
则定位出是由于kamailio的安全配置问题
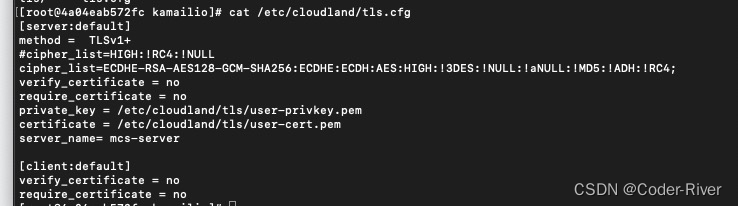
然后跟踪自己kamailio的相关配置发现,我们的kamailio的安全配置是在tls.cfg文件里配置的
kamctl kamcmd cfg.set_now_string tls config "/etc/cloudland/tls.cfg"
[root@4a04eab572fc kamailio]# grep -nri "tls.cfg"
kamailio.cfg:375:modparam("tls", "config", "/etc/cloudland/tls.cfg")从上面也能看出,我们关于kamilio的安全配置是在/etc/cloudland/tls.cfg下配置的
[root@ccad4d1db13c conf]# cat /etc/cloudland/tls.cfg
[server:default]
method = TLSv1+
cipher_list=HIGH:!RC4:!NULL
verify_certificate = no
require_certificate = no
private_key = /etc/cloudland/tls/server-privkey.pem
certificate = /etc/cloudland/tls/server-cert.pem
server_name= mcs-server[client:default]
verify_certificate = no
require_certificate = no从上面可以看出,cipher_list=HIGH:!RC4:!NULL
由于扫描nginx的的端口的时候没有报错上面的漏洞,我们把nginx的ssl_ciphers的相关配置拷贝了一份,给kamilio的cipher_list,(这样可能会引起呼叫连通性相关的问题)
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE:ECDH:AES:HIGH:!3DES:!NULL:!aNULL:!MD5:!ADH:!RC4;更改后的tls.cfg
更改后,重启kamailio的服务 ,然后从新用nmap扫描
nmap -sV -p 5061 --script ssl-enum-ciphers 172.24.0.104
查看扫描结果,都是strong了
Starting Nmap 6.40 ( http://nmap.org ) at 2021-10-21 15:15 CST
Nmap scan report for 4a04eab572fc (172.24.0.104)
Host is up (-2100s latency).
PORT STATE SERVICE VERSION
5061/tcp open ssl/sip-tls?
| ssl-enum-ciphers:
| SSLv3: No supported ciphers found
| TLSv1.0:
| ciphers:
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| compressors:
| NULL
| TLSv1.1:
| ciphers:
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| compressors:
| NULL
| TLSv1.2:
| ciphers:
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 - strong
| TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 - strong
| TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 - strong
| TLS_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 - strong
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 - strong
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 - strong
| TLS_RSA_WITH_AES_128_CBC_SHA - strong
| TLS_RSA_WITH_AES_128_CBC_SHA256 - strong
| TLS_RSA_WITH_AES_128_GCM_SHA256 - strong
| TLS_RSA_WITH_AES_256_CBC_SHA - strong
| TLS_RSA_WITH_AES_256_CBC_SHA256 - strong
| TLS_RSA_WITH_AES_256_GCM_SHA384 - strong
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA - strong
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA - strong
| compressors:
| NULL
|_ least strength: strong
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :
SF-Port5061-TCP:V=6.40%T=SSL%I=7%D=10/21%Time=617113B7%P=x86_64-redhat-lin
SF:ux-gnu%r(SIPOptions,20A,"SIP/2\.0\x20478\x20Unresolvable\x20destination
SF:\x20\(478/SL\)\r\nVia:\x20SIP/2\.0/TCP\x20nm;branch=foo;rport=47120;rec
SF:eived=172\.24\.0\.104\r\nFrom:\x20;tag=root\r\nTo:\x20;tag=6c98e1cb71aad21e8ecfc5e73ec5c3a2\.1e840000\r\nCall-ID:\x205
SF:0000\r\nCSeq:\x2042\x20OPTIONS\r\nContent-Length:\x200\r\n\r\nSIP/2\.0\
SF:x20478\x20Unresolvable\x20destination\x20\(478/TM\)\r\nVia:\x20SIP/2\.0
SF:/TCP\x20nm;branch=foo;rport=47120;received=172\.24\.0\.104\r\nFrom:\x20
SF:;tag=root\r\nTo:\x20;tag=bfd39b48636a9af5c63b59
SF:9e1a756d31-1e840000\r\nCall-ID:\x2050000\r\nCSeq:\x2042\x20OPTIONS\r\nC
SF:ontent-Length:\x200\r\n\r\n")%r(GenericLines,2,"\r\n");Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 130.60 seconds 综上漏洞解决
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!