Goby漏洞更新|铭飞 MCMS shiro 反序列化漏洞(CVE-2022-22928)
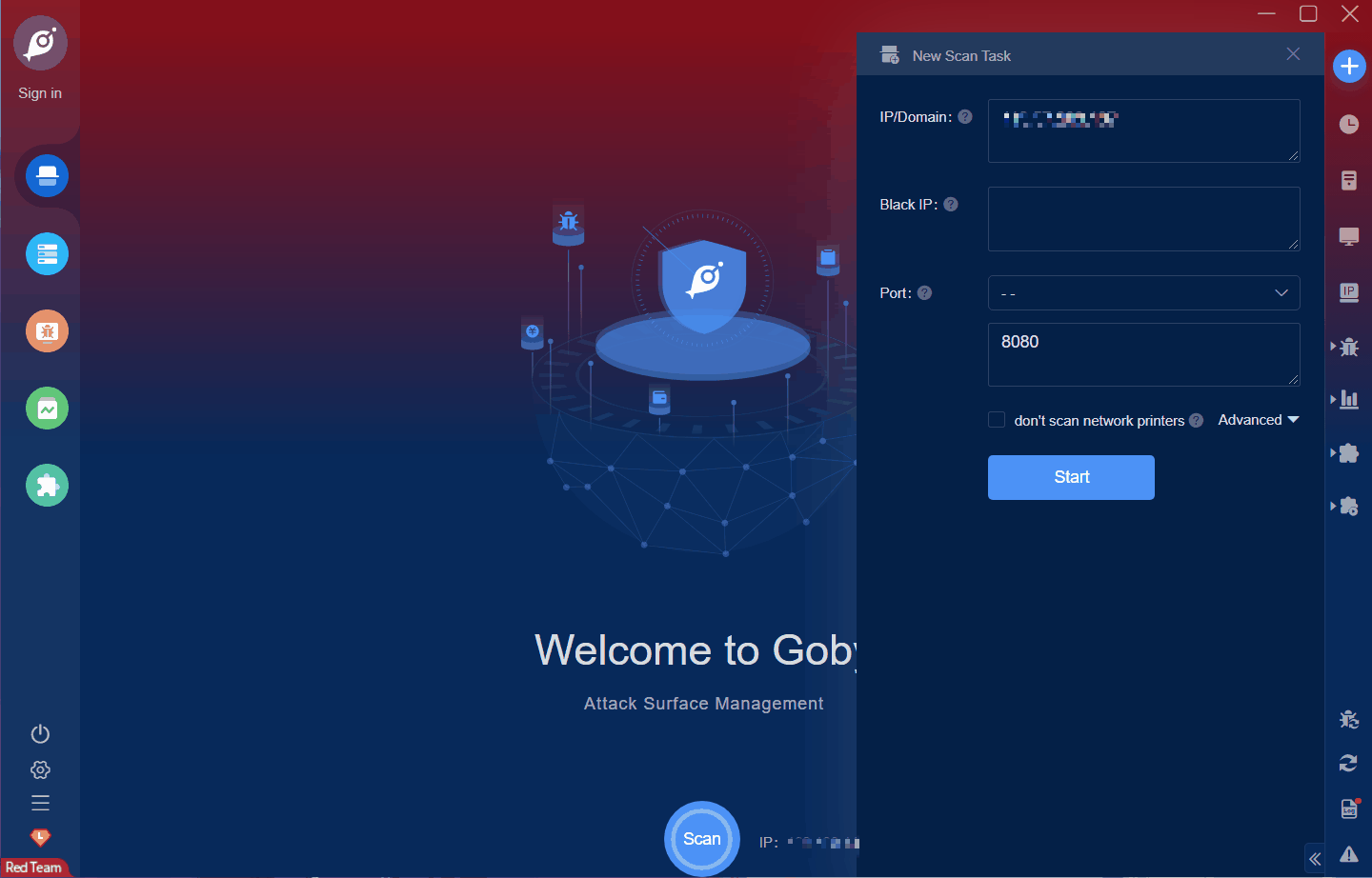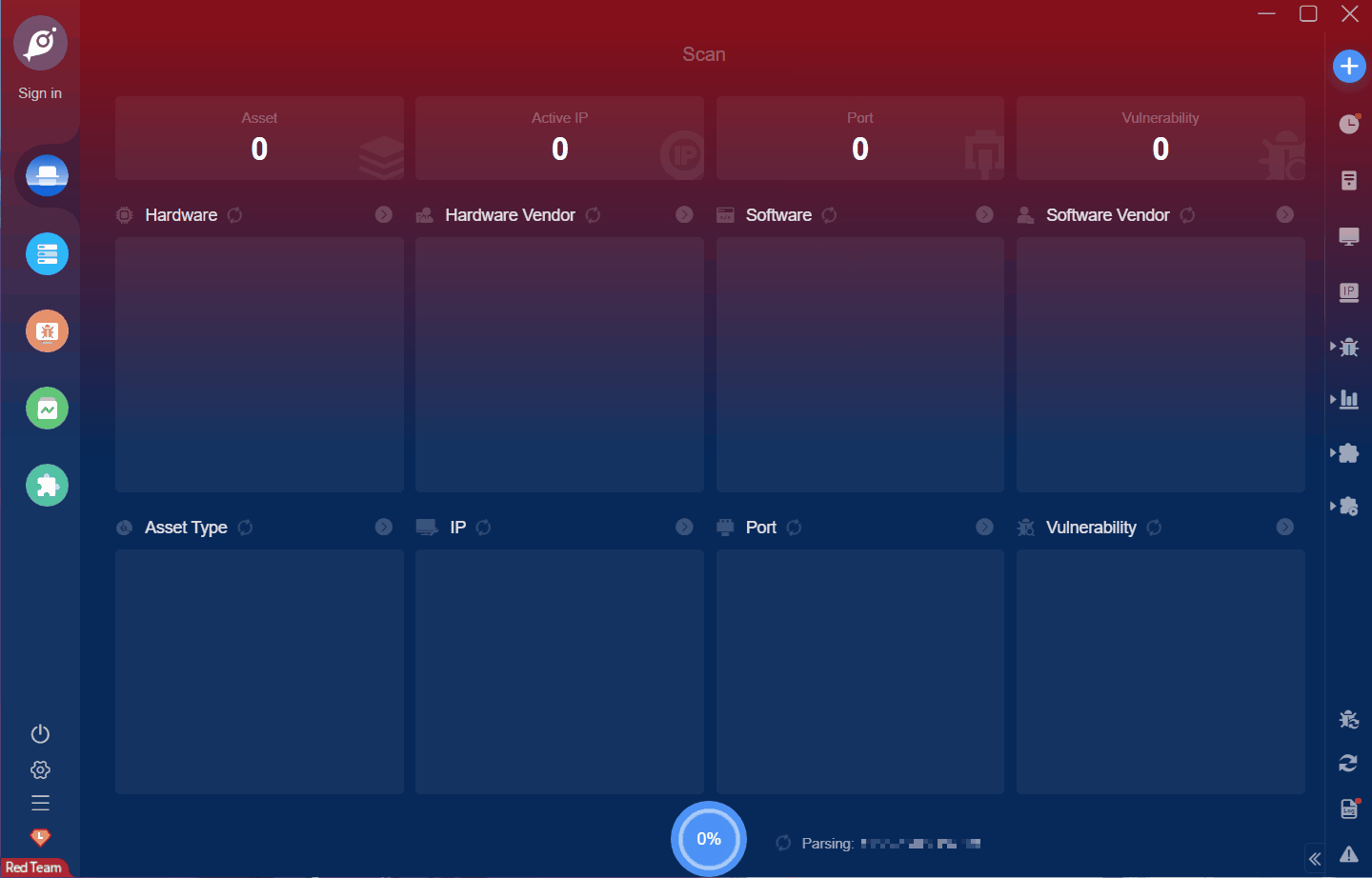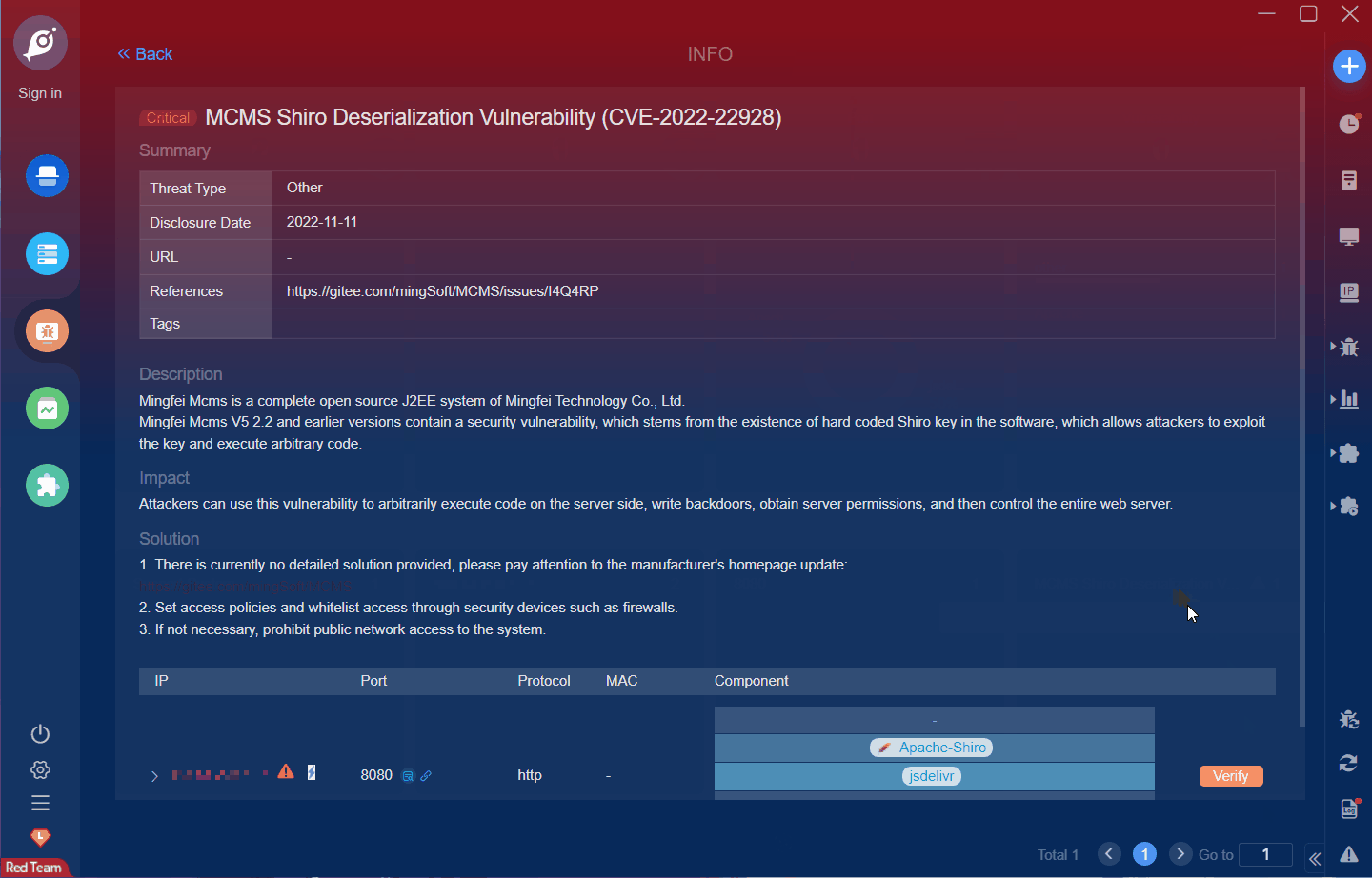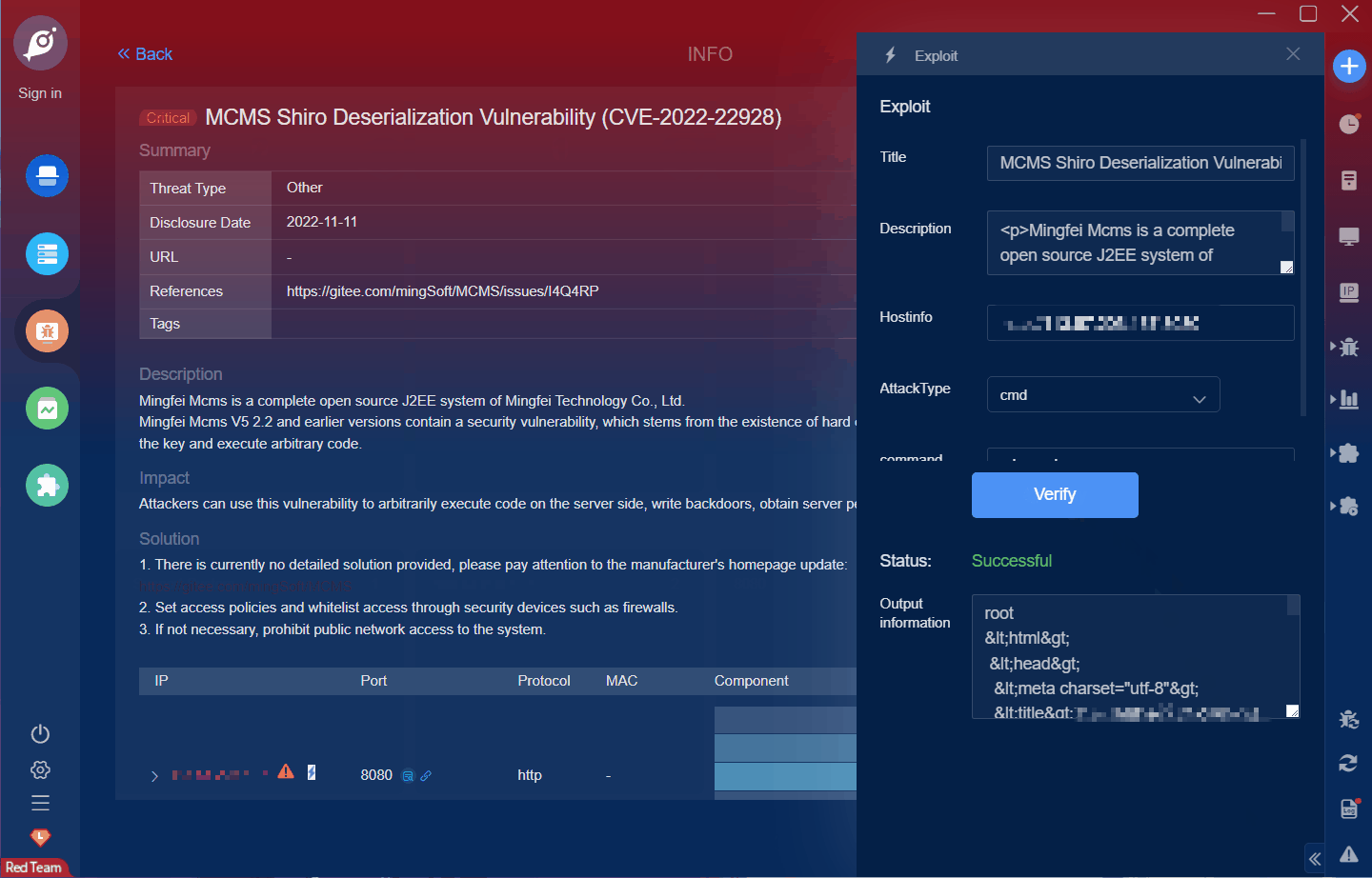
漏洞名称: 铭飞 MCMS shiro 反序列化漏洞(CVE-2022-22928)
English Name:MCMS Shiro Deserialization Vulnerability (CVE-2022-22928)
CVSS core: 9.8
影响资产数:295
漏洞描述:
Mcms is a complete open source J2EE system of Mingfei Technology Co., Ltd. Based on the SpringBoot 2 architecture, the front-end is based on vue and element ui. There is a shiro deserialization vulnerability in Mingfei Mcms v5.2.2 and earlier. The vulnerability originates from the hard coded shiro key in the software. An attacker can use this key to generate malicious serialized data, execute arbitrary code on the server, execute system commands, or hack into the memory horse to obtain server permissions.
漏洞影响:
There is a shiro deserialization vulnerability in Mingfei Mcms v5.2.2 and earlier. The vulnerability originates from the hard coded shiro key in the software. An attacker can use this key to generate malicious serialized data, execute arbitrary code on the server, execute system commands, or hack into the memory horse to obtain server permissions.
FOFA查询语句(点击直接查看结果):
body=“铭飞Mcms” || title=“铭飞Mcms”
此漏洞已可在Goby漏扫/红队版进行扫描验证
免费获取Goby:Goby社区版免费下载
查看Goby更多漏洞:Goby历史漏洞合集
关注Goby公众号获取最新动态:Gobysec
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!