Linux命令:objdump
1 需求
关键参数
- -f, --file-headers Display the contents of the overall file header
- -p, --private-headers Display object format specific file header contents
- -h, --[section-]headers Display the contents of the section headers
- -x, --all-headers Display the contents of all headers
- -s, --full-contents Display the full contents of all sections requested
- -t, --syms Display the contents of the symbol table(s)
- -T, --dynamic-syms Display the contents of the dynamic symbol table
2 语法
D:\JetBrains\CLion 2022.2.3\bin\mingw\bin>objdump.exe --help
Usage: objdump.exe Display information from object .At least one of the following switches must be given:-a, --archive-headers Display archive header information-f, --file-headers Display the contents of the overall file header-p, --private-headers Display object format specific file header contents-P, --private=OPT,OPT... Display object format specific contents-h, --[section-]headers Display the contents of the section headers-x, --all-headers Display the contents of all headers-d, --disassemble Display assembler contents of executable sections-D, --disassemble-all Display assembler contents of all sections--disassemble= Display assembler contents from -S, --source Intermix source code with disassembly--source-comment[=] Prefix lines of source code with -s, --full-contents Display the full contents of all sections requested-g, --debugging Display debug information in object file-e, --debugging-tags Display debug information using ctags style-G, --stabs Display (in raw form) any STABS info in the file-W, --dwarf[a/=abbrev, A/=addr, r/=aranges, c/=cu_index, L/=decodedline,f/=frames, F/=frames-interp, g/=gdb_index, i/=info, o/=loc,m/=macro, p/=pubnames, t/=pubtypes, R/=Ranges, l/=rawline,s/=str, O/=str-offsets, u/=trace_abbrev, T/=trace_aranges,U/=trace_info]Display the contents of DWARF debug sections-Wk,--dwarf=links Display the contents of sections that link toseparate debuginfo files-WK,--dwarf=follow-linksFollow links to separate debug info files (default)-WN,--dwarf=no-follow-linksDo not follow links to separate debug info files-L, --process-links Display the contents of non-debug sections inseparate debuginfo files. (Implies -WK)--ctf=SECTION Display CTF info from SECTION-t, --syms Display the contents of the symbol table(s)-T, --dynamic-syms Display the contents of the dynamic symbol table-r, --reloc Display the relocation entries in the file-R, --dynamic-reloc Display the dynamic relocation entries in the file@ Read options from -v, --version Display this program's version number-i, --info List object formats and architectures supported-H, --help Display this informationThe following switches are optional:-b, --target=BFDNAME Specify the target object format as BFDNAME-m, --architecture=MACHINE Specify the target architecture as MACHINE-j, --section=NAME Only display information for section NAME-M, --disassembler-options=OPT Pass text OPT on to the disassembler-EB --endian=big Assume big endian format when disassembling-EL --endian=little Assume little endian format when disassembling--file-start-context Include context from start of file (with -S)-I, --include=DIR Add DIR to search list for source files-l, --line-numbers Include line numbers and filenames in output-F, --file-offsets Include file offsets when displaying information-C, --demangle[=STYLE] Decode mangled/processed symbol namesThe STYLE, if specified, can be `auto', `gnu',`lucid', `arm', `hp', `edg', `gnu-v3', `java'or `gnat'--recurse-limit Enable a limit on recursion whilst demangling(default)--no-recurse-limit Disable a limit on recursion whilst demangling-w, --wide Format output for more than 80 columns-z, --disassemble-zeroes Do not skip blocks of zeroes when disassembling--start-address=ADDR Only process data whose address is >= ADDR--stop-address=ADDR Only process data whose address is < ADDR--no-addresses Do not print address alongside disassembly--prefix-addresses Print complete address alongside disassembly--[no-]show-raw-insn Display hex alongside symbolic disassembly--insn-width=WIDTH Display WIDTH bytes on a single line for -d--adjust-vma=OFFSET Add OFFSET to all displayed section addresses--special-syms Include special symbols in symbol dumps--inlines Print all inlines for source line (with -l)--prefix=PREFIX Add PREFIX to absolute paths for -S--prefix-strip=LEVEL Strip initial directory names for -S--dwarf-depth=N Do not display DIEs at depth N or greater--dwarf-start=N Display DIEs starting at offset N--dwarf-check Make additional dwarf consistency checks.--ctf-parent=SECTION Use SECTION as the CTF parent--visualize-jumps Visualize jumps by drawing ASCII art lines--visualize-jumps=color Use colors in the ASCII art--visualize-jumps=extended-colorUse extended 8-bit color codes--visualize-jumps=off Disable jump visualizationobjdump.exe: supported targets: pe-x86-64 pei-x86-64 pe-bigobj-x86-64 elf64-x86-64 elf64-l1om elf64-k1om pe-i386 pei-i386 elf32-i386 elf32-iamcu elf64-little elf64-big elf32-little elf32-big srec symbolsrec verilog tekhex binary ihex plugin
objdump.exe: supported architectures: i386 i386:x86-64 i386:x64-32 i8086 i386:intel i386:x86-64:intel i386:x64-32:intel iamcu iamcu:intel l1om l1om:intel k1om k1om:intelThe following i386/x86-64 specific disassembler options are supported for use
with the -M switch (multiple options should be separated by commas):x86-64 Disassemble in 64bit modei386 Disassemble in 32bit modei8086 Disassemble in 16bit modeatt Display instruction in AT&T syntaxintel Display instruction in Intel syntaxatt-mnemonicDisplay instruction in AT&T mnemonicintel-mnemonicDisplay instruction in Intel mnemonicaddr64 Assume 64bit address sizeaddr32 Assume 32bit address sizeaddr16 Assume 16bit address sizedata32 Assume 32bit data sizedata16 Assume 16bit data sizesuffix Always display instruction suffix in AT&T syntaxamd64 Display instruction in AMD64 ISAintel64 Display instruction in Intel64 ISA
Report bugs to 3 示例
objdump -f main
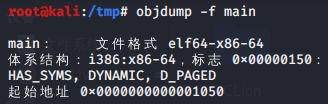
3 示例
objdump -p --wide main
root@kali:/tmp# objdump -p --wide mainmain: 文件格式 elf64-x86-64程序头:PHDR off 0x0000000000000040 vaddr 0x0000000000000040 paddr 0x0000000000000040 align 2**3filesz 0x0000000000000268 memsz 0x0000000000000268 flags r--INTERP off 0x00000000000002a8 vaddr 0x00000000000002a8 paddr 0x00000000000002a8 align 2**0filesz 0x000000000000001c memsz 0x000000000000001c flags r--LOAD off 0x0000000000000000 vaddr 0x0000000000000000 paddr 0x0000000000000000 align 2**12filesz 0x0000000000000568 memsz 0x0000000000000568 flags r--LOAD off 0x0000000000001000 vaddr 0x0000000000001000 paddr 0x0000000000001000 align 2**12filesz 0x00000000000001cd memsz 0x00000000000001cd flags r-xLOAD off 0x0000000000002000 vaddr 0x0000000000002000 paddr 0x0000000000002000 align 2**12filesz 0x0000000000000150 memsz 0x0000000000000150 flags r--LOAD off 0x0000000000002de8 vaddr 0x0000000000003de8 paddr 0x0000000000003de8 align 2**12filesz 0x0000000000000248 memsz 0x0000000000000250 flags rw-DYNAMIC off 0x0000000000002df8 vaddr 0x0000000000003df8 paddr 0x0000000000003df8 align 2**3filesz 0x00000000000001e0 memsz 0x00000000000001e0 flags rw-NOTE off 0x00000000000002c4 vaddr 0x00000000000002c4 paddr 0x00000000000002c4 align 2**2filesz 0x0000000000000044 memsz 0x0000000000000044 flags r--
EH_FRAME off 0x000000000000200c vaddr 0x000000000000200c paddr 0x000000000000200c align 2**2filesz 0x000000000000003c memsz 0x000000000000003c flags r--STACK off 0x0000000000000000 vaddr 0x0000000000000000 paddr 0x0000000000000000 align 2**4filesz 0x0000000000000000 memsz 0x0000000000000000 flags rw-RELRO off 0x0000000000002de8 vaddr 0x0000000000003de8 paddr 0x0000000000003de8 align 2**0filesz 0x0000000000000218 memsz 0x0000000000000218 flags r--动态节:NEEDED libc.so.6INIT 0x0000000000001000FINI 0x00000000000011c4INIT_ARRAY 0x0000000000003de8INIT_ARRAYSZ 0x0000000000000008FINI_ARRAY 0x0000000000003df0FINI_ARRAYSZ 0x0000000000000008GNU_HASH 0x0000000000000308STRTAB 0x00000000000003d8SYMTAB 0x0000000000000330STRSZ 0x0000000000000084SYMENT 0x0000000000000018DEBUG 0x0000000000000000PLTGOT 0x0000000000004000PLTRELSZ 0x0000000000000018PLTREL 0x0000000000000007JMPREL 0x0000000000000550RELA 0x0000000000000490RELASZ 0x00000000000000c0RELAENT 0x0000000000000018FLAGS_1 0x0000000008000000VERNEED 0x0000000000000470VERNEEDNUM 0x0000000000000001VERSYM 0x000000000000045cRELACOUNT 0x0000000000000003版本引用:required from libc.so.6:0x09691a75 0x00 02 GLIBC_2.2.5
3 示例
objdump -h --wide main
root@kali:/tmp# objdump -h --wide mainmain: 文件格式 elf64-x86-64 节:
Idx Name Size VMA LMA File off Algn 标志 0 .interp 0000001c 00000000000002a8 00000000000002a8 000002a8 2**0 CONTENTS, ALLOC, LOAD, READONLY, DATA 1 .note.gnu.build-id 00000024 00000000000002c4 00000000000002c4 000002c4 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 2 .note.ABI-tag 00000020 00000000000002e8 00000000000002e8 000002e8 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 3 .gnu.hash 00000024 0000000000000308 0000000000000308 00000308 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 4 .dynsym 000000a8 0000000000000330 0000000000000330 00000330 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 5 .dynstr 00000084 00000000000003d8 00000000000003d8 000003d8 2**0 CONTENTS, ALLOC, LOAD, READONLY, DATA 6 .gnu.version 0000000e 000000000000045c 000000000000045c 0000045c 2**1 CONTENTS, ALLOC, LOAD, READONLY, DATA 7 .gnu.version_r 00000020 0000000000000470 0000000000000470 00000470 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 8 .rela.dyn 000000c0 0000000000000490 0000000000000490 00000490 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 9 .rela.plt 00000018 0000000000000550 0000000000000550 00000550 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 10 .init 00000017 0000000000001000 0000000000001000 00001000 2**2 CONTENTS, ALLOC, LOAD, READONLY, CODE 11 .plt 00000020 0000000000001020 0000000000001020 00001020 2**4 CONTENTS, ALLOC, LOAD, READONLY, CODE 12 .plt.got 00000008 0000000000001040 0000000000001040 00001040 2**3 CONTENTS, ALLOC, LOAD, READONLY, CODE 13 .text 00000171 0000000000001050 0000000000001050 00001050 2**4 CONTENTS, ALLOC, LOAD, READONLY, CODE 14 .fini 00000009 00000000000011c4 00000000000011c4 000011c4 2**2 CONTENTS, ALLOC, LOAD, READONLY, CODE 15 .rodata 0000000a 0000000000002000 0000000000002000 00002000 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 16 .eh_frame_hdr 0000003c 000000000000200c 000000000000200c 0000200c 2**2 CONTENTS, ALLOC, LOAD, READONLY, DATA 17 .eh_frame 00000108 0000000000002048 0000000000002048 00002048 2**3 CONTENTS, ALLOC, LOAD, READONLY, DATA 18 .init_array 00000008 0000000000003de8 0000000000003de8 00002de8 2**3 CONTENTS, ALLOC, LOAD, DATA 19 .fini_array 00000008 0000000000003df0 0000000000003df0 00002df0 2**3 CONTENTS, ALLOC, LOAD, DATA 20 .dynamic 000001e0 0000000000003df8 0000000000003df8 00002df8 2**3 CONTENTS, ALLOC, LOAD, DATA 21 .got 00000028 0000000000003fd8 0000000000003fd8 00002fd8 2**3 CONTENTS, ALLOC, LOAD, DATA 22 .got.plt 00000020 0000000000004000 0000000000004000 00003000 2**3 CONTENTS, ALLOC, LOAD, DATA 23 .data 00000010 0000000000004020 0000000000004020 00003020 2**3 CONTENTS, ALLOC, LOAD, DATA 24 .bss 00000008 0000000000004030 0000000000004030 00003030 2**0 ALLOC 25 .comment 00000026 0000000000000000 0000000000000000 00003030 2**0 CONTENTS, READONLY
4 参考资料
readelf 和 objdump 例子详解及区别 (ELF文件说明)_readelf工具可以进行代码反汇编_Hani_97的博客-CSDN博客
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!