1、防刷限流实现1
1、本章诉求
限流的需求出现在许多常见的场景中:
- 秒杀活动,有人使用软件恶意刷单抢货,需要限流防止机器参与活动
- 某api被各式各样系统广泛调用,严重消耗网络、内存等资源,需要合理限流
2、流程设计
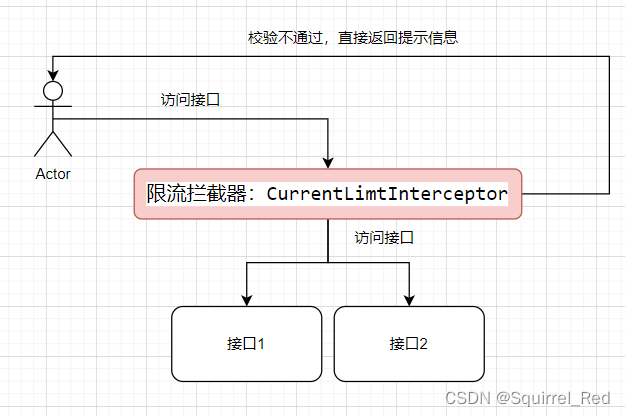
3、方案实现
3.1、实现思路:
- 通过ip:api路径的作为key,访问次数为value的方式对某一用户的某一请求进行唯一标识
- 每次访问的时候判断
key是否存在,是否count超过了限制的访问次数 - 若访问超出限制,则应
response返回msg:请求过于频繁给前端予以展示
3.2、编码实现
技术要点:redis、自定义注解、拦截器
application.yml
server:port: 8080spring:redis:database: 0host: 127.0.0.1port: 6379timeout: 30000mslettuce:pool:max-active: 8max-idle: 8max-wait: 500msmin-idle: 0
pom.xml
<project xmlns="http://maven.apache.org/POM/4.0.0"xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd"><parent><groupId>org.springframework.bootgroupId><artifactId>spring-boot-starter-parentartifactId><version>2.1.6.RELEASEversion><relativePath/> parent><modelVersion>4.0.0modelVersion><artifactId>coderhome-access-limitartifactId><dependencies><dependency><groupId>org.springframework.bootgroupId><artifactId>spring-boot-starter-webartifactId>dependency><dependency><groupId>org.springframework.bootgroupId><artifactId>spring-boot-starter-data-redisartifactId>dependency><dependency><groupId>org.apache.commonsgroupId><artifactId>commons-pool2artifactId><version>2.6.0version>dependency>dependencies>project>
启动类WebApplication
package club.coderhome;import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;@SpringBootApplication
public class WebApplication {public static void main(String[] args) {SpringApplication.run(WebApplication.class, args);}}RedisConfig
package club.coderhome.config;import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.data.redis.connection.RedisConnectionFactory;
import org.springframework.data.redis.core.RedisTemplate;
import org.springframework.data.redis.core.StringRedisTemplate;
import org.springframework.data.redis.serializer.Jackson2JsonRedisSerializer;
import org.springframework.data.redis.serializer.StringRedisSerializer;/*** @Author 北冥有鱼* @Description redis配置类* @Date 2023/5/5 20:15*/
@Configuration
public class RedisConfig {@Beanpublic RedisTemplate<String, Object> redisTemplate(RedisConnectionFactory connectionFactory) {RedisTemplate<String, Object> redisTemplate = new RedisTemplate<>();redisTemplate.setConnectionFactory(connectionFactory);redisTemplate.setKeySerializer(new StringRedisSerializer());redisTemplate.setValueSerializer(new Jackson2JsonRedisSerializer(Object.class));return redisTemplate;}@Beanpublic StringRedisTemplate stringRedisTemplate(RedisConnectionFactory connectionFactory) {StringRedisTemplate redisTemplate = new StringRedisTemplate();redisTemplate.setConnectionFactory(connectionFactory);redisTemplate.setKeySerializer(new StringRedisSerializer());redisTemplate.setValueSerializer(new StringRedisSerializer());return redisTemplate;}
}编写自定义注解类CurrentLimit
/*** @Author 北冥有鱼* @Description 限流注解:三个参数分别代表有效时间、最大访问次数、是否需要登录,可以理解为 expirationTime 内最多访问 maxCount 次。* @Date 2023/5/5 20:42*/
@Retention(RetentionPolicy.RUNTIME)
@Target(ElementType.METHOD)
public @interface CurrentLimit {//有效时间,单位ms,默认10000msint expirationTime() default 10000;//最大访问次数int maxCount();//是否需要登录boolean needLogin() default true;
}
拦截器CurrentLimtInterceptor
/*** @Author 北冥有鱼* @Description 自定义限流拦截器* @Date 2023/5/5 20:47*/
@Component
public class CurrentLimtInterceptor implements HandlerInterceptor {@Resourceprivate RedisTemplate redisTemplate;@Overridepublic boolean preHandle(HttpServletRequest request, HttpServletResponse response, Object handler) throws Exception {if (handler instanceof HandlerMethod) {HandlerMethod hm = (HandlerMethod) handler;//获取注解信息CurrentLimit accessLimit = hm.getMethodAnnotation(CurrentLimit.class);if (null == accessLimit) {return true;}int expirationTime = accessLimit.expirationTime();int maxCount = accessLimit.maxCount();boolean needLogin = accessLimit.needLogin();if (needLogin) {//判断是否登录}//客户端ip地址String ip = request.getRemoteAddr();String key = ip + ":" + request.getServletPath();Integer count = (Integer) redisTemplate.opsForValue().get(key);//第一次访问if (null == count || -1 == count) {//设置值,并设置过期时间redisTemplate.opsForValue().set(key, 1, expirationTime, TimeUnit.MILLISECONDS);return true;}//如果访问次数<最大次数,则加1操作if (count < maxCount) {redisTemplate.opsForValue().increment(key, 1);return true;}//超过最大值返回操作频繁if (count >= maxCount) {System.out.println("count==" + count);//解决乱码问题response.setContentType("text/html;charset=utf-8");response.getWriter().write("请求过于频繁,请稍后再试");return false;}}return true;}
}
注册拦截器并配置拦截规则
@Configuration
public class InterceptorConfig implements WebMvcConfigurer {@Autowiredprivate CurrentLimtInterceptor currentLimtInterceptor;@Overridepublic void addInterceptors(InterceptorRegistry registry) {registry.addInterceptor(currentLimtInterceptor).addPathPatterns("/draw/**")//拦截器拦截的请求路径.excludePathPatterns("/access/login");}
}
在Controller层的方法上直接可以使用注解@AccessLimit
@RestController
@RequestMapping("/draw")
public class DrawController {@ResponseBody@GetMapping("/doDraw")@CurrentLimit(expirationTime = 30000, maxCount = 3)public String accessLimit() {return "恭喜你,抽中iphone25一台";}
}
4、总结
这里只是提供一个实现防刷策略思路,还可以用nginx条件限流、token机制防刷、布隆过滤器校验,黑名单机制等。
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!