K8S应用笔记 —— 部署Nginx服务发布前端项目(PV、PVC、Deployment、Service、Ingress )
一、需求描述
在K8S集群上通过部署Nginx服务发布前端项目,其中:
- 前端项目发布文件通过
PV和PVC存储在NFS上实现多Pod持久化和共享 - 将
Nginx服务配置文件存储至K8S的configmap中 - 将阿里云证书文件存储至
K8S的secret中 - 通过
Ingress设置证书,并将Nginx服务暴露到集群外部
二、创建NFS存储
创建NFS存储主要是为了给Nginx服务提供稳定的后端存储,当Nginx的Pod重启或迁移、扩容后,依然能获得原先的数据。这里,我们先要先创建NFS,然后通过使用PV为Nginx挂载一个远程的NFS路径。
2.1 安装配置NFS服务端
由于硬件资源有限,我在k8s-master上搭建。执行如下命令安装NFS和rpcbind:
yum -y install nfs-utils rpcbind
其中,NFS依靠远程过程调用(RPC)在客户端和服务器端路由请求,因此需要安装rpcbind服务。
执行命令 vim /etc/exports,创建 exports 文件,文件内容如下:
/root/nfs_root/ *(insecure,rw,sync,no_root_squash)
执行以下命令,启动 nfs 服务
# 创建共享目录,如果要使用自己的目录,请替换本文档中所有的 /root/nfs_root/
mkdir /root/nfs_rootsystemctl enable rpcbind
systemctl enable nfs-serversystemctl start rpcbind
systemctl start nfs-server
检查配置是否生效
exportfs
# 输出结果如下所示
/root/nfs_root /root/nfs_root
2.2 安装配置NFS客户端
注意事项:
- 如:服务器端防火墙开启,需开放
111、662、875、892、2049的tcp / udp访问,否则远端客户无法连接。
我在k8s-work1上执行以下命令安装 NFS客户端所需的软件包
yum install -y nfs-utils
执行以下命令检查 NFS服务器端是否有设置共享目录
# showmount -e $(nfs服务器的IP)
showmount -e 192.168.0.50
# 输出结果如下所示
Export list for 192.168.0.50
/root/nfs_root *
执行以下命令挂载 NFS服务器上的共享目录到本机路径 /root/nfsmount
mkdir /root/nfsmount
# mount -t nfs $(nfs服务器的IP):/root/nfs_root /root/nfsmount
mount -t nfs 192.168.0.50:/root/nfs_root /root/nfsmount
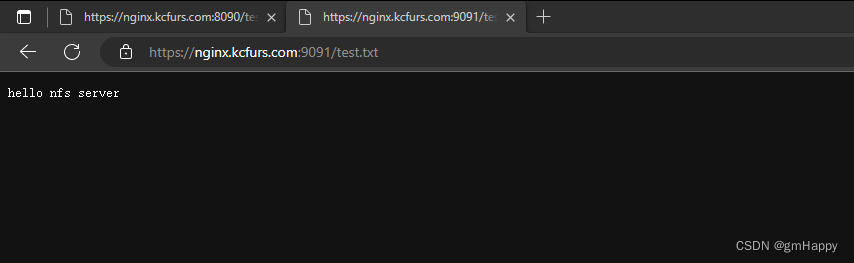
# 写入一个测试文件
echo "hello nfs server" > /root/nfsmount/test.txt
在 NFS 服务器上执行以下命令,验证文件写入成功
cat /root/nfs_root/test.txt
通过以下方式进行开机自动挂载
vi /etc/rc.local
mount -t nfs 192.168.0.50:/root/nfs_root /root/nfsmount
三、Nginx配置写入configmap
Nginx配置文件default.conf:
server {listen 80 default_server;listen [::]:80 default_server ipv6only=on;listen 443 ssl;root /usr/share/nginx/html;index index.html;server_name localhost;ssl_certificate /etc/nginx/ssl/10900597_nginx.kcfurs.com_nginx/nginx.kcfurs.com.pem;ssl_certificate_key /etc/nginx/ssl/10900597_nginx.kcfurs.com_nginx/nginx.kcfurs.com.key;location / {try_files $uri $uri/ =404;}
}
注意事项:
- 此处我的证书所在的
Pod文件路径是/etc/nginx/ssl/10900597_nginx.kcfurs.com_nginx/,需在创建Deployment时与secret进行挂载,详见下文5.1章节。
kubectl create configmap nginxconfigmap --from-file=default.conf

四、阿里云证书写入secret
证书来自阿里云,此处就不进行过多介绍。
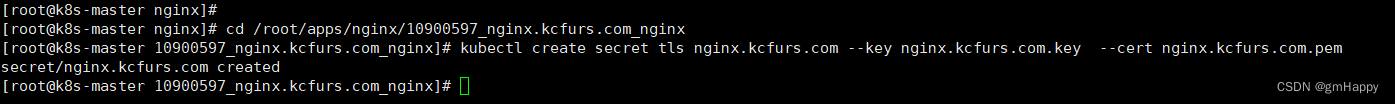
cd /root/apps/nginx/10900597_nginx.kcfurs.com_nginx
kubectl create secret tls nginx.kcfurs.com --key nginx.kcfurs.com.key --cert nginx.kcfurs.com.pem
五、Deployment具体配置
5.1 完整配置文件
nginx-deployment.yaml:
---
kind: Deployment
apiVersion: apps/v1
metadata:name: nginxnamespace: defaultlabels:app: nginxk8s.kuboard.cn/name: nginxannotations: {}
spec:replicas: 1selector:matchLabels:app: nginxtemplate:metadata:creationTimestamp: nulllabels:app: nginxannotations:kubectl.kubernetes.io/restartedAt: '2023-08-17T16:50:05+08:00'spec:volumes:- name: config-dataconfigMap:name: nginxconfigmapitems:- key: default.confpath: default.confdefaultMode: 420- name: html-datanfs:server: 192.168.0.50path: /root/nfs_root/nginx/html- name: secret-datasecret:secretName: nginx.kcfurs.comitems:- key: tls.crtpath: nginx.kcfurs.com.pem- key: tls.keypath: nginx.kcfurs.com.keydefaultMode: 420containers:- name: nginximage: nginxports:- name: httpcontainerPort: 80protocol: TCP- name: httpscontainerPort: 443protocol: TCPresources: {}volumeMounts:- name: config-datamountPath: /etc/nginx/conf.d/- name: html-datamountPath: /usr/share/nginx/html- name: secret-datamountPath: /etc/nginx/ssl/10900597_nginx.kcfurs.com_nginxterminationMessagePath: /dev/termination-logterminationMessagePolicy: FileimagePullPolicy: IfNotPresentrestartPolicy: AlwaysterminationGracePeriodSeconds: 30dnsPolicy: ClusterFirstsecurityContext: {}schedulerName: default-schedulerstrategy:type: RollingUpdaterollingUpdate:maxUnavailable: 25%maxSurge: 25%revisionHistoryLimit: 10progressDeadlineSeconds: 600---
kind: Service
apiVersion: v1
metadata:name: nginxnamespace: defaultlabels:app: nginxk8s.kuboard.cn/name: nginx
spec:ports:- name: httpprotocol: TCPport: 80targetPort: 80nodePort: 31290- name: httpsprotocol: TCPport: 443targetPort: 443nodePort: 32623selector:app: nginxtype: NodePortsessionAffinity: ClientIPexternalTrafficPolicy: ClustersessionAffinityConfig:clientIP:timeoutSeconds: 10800ipFamilies:- IPv4ipFamilyPolicy: SingleStackinternalTrafficPolicy: Cluster---
kind: Ingress
apiVersion: networking.k8s.io/v1
metadata:name: nginxnamespace: defaultlabels:app: nginxk8s.kuboard.cn/name: nginxannotations:nginx.ingress.kubernetes.io/backend-protocol: HTTPSnginx.ingress.kubernetes.io/rewrite-target: /
spec:ingressClassName: nginx-ingresstls:- hosts:- nginx.kcfurs.comsecretName: nginx.kcfurs.comrules:- host: nginx.kcfurs.comhttp:paths:- path: /pathType: Prefixbackend:service:name: nginxport:number: 443---
kind: ConfigMap
apiVersion: v1
metadata:name: nginxconfigmapnamespace: default
data:default.conf: "server {\r\n listen 80 default_server;\r\n listen [::]:80 default_server ipv6only=on;\r\n\r\n listen 443 ssl;\r\n\r\n root /usr/share/nginx/html;\r\n index index.html;\r\n\r\n server_name localhost;\r\n ssl_certificate /etc/nginx/ssl/10900597_nginx.kcfurs.com_nginx/nginx.kcfurs.com.pem;\r\n ssl_certificate_key /etc/nginx/ssl/10900597_nginx.kcfurs.com_nginx/nginx.kcfurs.com.key;\r\n\r\n location / {\r\n try_files $uri $uri/ =404;\r\n }\r\n}"---
kind: Secret
apiVersion: v1
metadata:name: nginx.kcfurs.comnamespace: default
data:tls.crt: >-LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUY5akNDQk42Z0F3SUJBZ0lRQ2VCY004N3E1VVNWY056RFFOTG1oekFOQmdrcWhraUc5dzBCQVFzRkFEQnUKTVFzd0NRWURWUVFHRXdKVlV6RVZNQk1HQTFVRUNoTU1SR2xuYVVObGNuUWdTVzVqTVJrd0Z3WURWUVFMRXhCMwpkM2N1WkdsbmFXTmxjblF1WTI5dE1TMHdLd1lEVlFRREV5UkZibU55ZVhCMGFXOXVJRVYyWlhKNWQyaGxjbVVnClJGWWdWRXhUSUVOQklDMGdSekl3SGhjTk1qTXdPREUzTURBd01EQXdXaGNOTWpRd09ERTJNak0xT1RVNVdqQWIKTVJrd0Z3WURWUVFERXhCdVoybHVlQzVyWTJaMWNuTXVZMjl0TUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQwpBUThBTUlJQkNnS0NBUUVBd3paT1J4eGdMUFVrOS9NYnpFdXI3anBjc0pFUlJEMU0yeVo4SEtVV25oWVFwbHNDCi9XankzdEhaelExTnpOeHNiMnJ0WWh6UldlbHVEUmZidnliQjFMV3hQQXlIM1hyLzQ4ZEJHdkM4bGYwV25sTkQKVnZHc0VSelNnb2lmRTlKeEZ5NFJUbUltOVdDT0hSdTFKVVFreEp1QTZGSENHVTBlL1orZGp3aXdXSXlSdEpOVwo2NTRZVVBUaVFSa3NvQTlvMVlScVdVd1pFVTFUV2V3YjJELzN3TVJMUkEzZjEvdHdkZGsxREtJbUc5aVJyWEdWCm5WTVFBdERrYXZHbU4xTW5LZ3FoaFlBNzVGT1Y1ZVdGSHVGMlFReDA1RVhRYlFjam8wS2wrcG1oR3d3MFo5Z1YKTTB3NXZTMVRIMDR0RGEvNDJONmdKSG91M3EzM1VabFoyTEZWRlFJREFRQUJvNElDNFRDQ0F0MHdId1lEVlIwagpCQmd3Rm9BVWVOK1JrRi91M3F6MnhYWHIxVXhWVSs4a1NyWXdIUVlEVlIwT0JCWUVGRnh4Nm5qTitnTUNKRmlWCjBEMGRvMGhBY0RlSk1Cc0dBMVVkRVFRVU1CS0NFRzVuYVc1NExtdGpablZ5Y3k1amIyMHdEZ1lEVlIwUEFRSC8KQkFRREFnV2dNQjBHQTFVZEpRUVdNQlFHQ0NzR0FRVUZCd01CQmdnckJnRUZCUWNEQWpBK0JnTlZIU0FFTnpBMQpNRE1HQm1lQkRBRUNBVEFwTUNjR0NDc0dBUVVGQndJQkZodG9kSFJ3T2k4dmQzZDNMbVJwWjJsalpYSjBMbU52CmJTOURVRk13Z1lBR0NDc0dBUVVGQndFQkJIUXdjakFrQmdnckJnRUZCUWN3QVlZWWFIUjBjRG92TDI5amMzQXUKWkdsbmFXTmxjblF1WTI5dE1Fb0dDQ3NHQVFVRkJ6QUNoajVvZEhSd09pOHZZMkZqWlhKMGN5NWthV2RwWTJWeQpkQzVqYjIwdlJXNWpjbmx3ZEdsdmJrVjJaWEo1ZDJobGNtVkVWbFJNVTBOQkxVY3lMbU55ZERBSkJnTlZIUk1FCkFqQUFNSUlCZndZS0t3WUJCQUhXZVFJRUFnU0NBVzhFZ2dGckFXa0Fkd0R1emRCazFkc2F6c1ZjdDUyMHpST2kKTW9kR2ZMenMzc05SU0ZsR2NSKzFtd0FBQVlvQ3BRWWJBQUFFQXdCSU1FWUNJUURJUlBxUmhOM3AwanJNVlV6Rgp1OTJwMTVZOVFtaVhYbmIrcHZZMjVUWmxvQUloQUtOMHFSemxYV1Fjam5XRCtDbGREc2FTUlpobitXY2g4TlRPCnNSVDJ0MUlHQUhZQVNMRGphOXFtUnpRUDVXb0MrcDB3Nnh4U0FjdFczU3lCMmJ1L3F6blloSE1BQUFHS0FxVUcKT1FBQUJBTUFSekJGQWlFQXV2bzUyekNPeEdnUlNxY0NXK0RDYTgxRjdEN0UyZklFWjVqSC9tZHMxT2tDSUZBSgpjaW5JNkNpZk8wVnc1OUk2M2lENW5wTjRPYXZVWnR2TlNVS0YzcWhSQUhZQTJyYS9heisxdGlLZm04SzdYR3ZvCmNKRnhiTHRSaElVMHZhUTlNRWpYKzZzQUFBR0tBcVVHRGdBQUJBTUFSekJGQWlBYVJyMk1xN0dGNGJqRlE4bzQKeEpuQkg2VWdJTWJSVnZwMTZDaVRxQVQ5ZmdJaEFLOXpxZG5ySTZJc0VOcWZpczRIOGtyMk4zYk40YXowTzdONAplZTk3NGx5ak1BMEdDU3FHU0liM0RRRUJDd1VBQTRJQkFRQ1RRM3YxY3dPMUVjUGJhRmxUcy9uNWo4eGtNSkhLCjJ3OWNEZ05QSWZROVNDYzdQVkJaUlV1azgvcldjbWlFeGMremdvc3lBM1IzNjh1cWVSQTVPU3V6MkpvREx1c0YKS1hlMUVyVmlxY1E0S1BzRXJsdUVwQjVKSXhXV2plM0Fpc0E3SGxKMEU1YkYrUXNnNEJmQnhzYXFYVllvM1R5UQpnTEo4Q2QvZWFIa0dqU09LUFZEQ2VvRmY1Z0ZRdjNTbndlQmZSMzFaN2FkcmVHVWtGSzNwa1pZNElSZFJ5V2hqCjlpU0RyZWIrc0NFZnhXM0FKaDdMaS83d00zZFRMRGRHTWRqTWo3bFEvbXRiY1hUNHNjTWR1S3JJS0QyamhyL3cKVDRTTUtHeHZWa0x3VGU2ZGJPUzV3K0V6R1JVMGJ6cFVEUnZyL2s5YU81WmVDcC9IUGl1S3ZCcEwKLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQotLS0tLUJFR0lOIENFUlRJRklDQVRFLS0tLS0KTUlJRXFqQ0NBNUtnQXdJQkFnSVFEZUQvdGU1aXkyRVFuMkNNbk8xZTB6QU5CZ2txaGtpRzl3MEJBUXNGQURCaApNUXN3Q1FZRFZRUUdFd0pWVXpFVk1CTUdBMVVFQ2hNTVJHbG5hVU5sY25RZ1NXNWpNUmt3RndZRFZRUUxFeEIzCmQzY3VaR2xuYVdObGNuUXVZMjl0TVNBd0hnWURWUVFERXhkRWFXZHBRMlZ5ZENCSGJHOWlZV3dnVW05dmRDQkgKTWpBZUZ3MHhOekV4TWpjeE1qUTJOREJhRncweU56RXhNamN4TWpRMk5EQmFNRzR4Q3pBSkJnTlZCQVlUQWxWVApNUlV3RXdZRFZRUUtFd3hFYVdkcFEyVnlkQ0JKYm1NeEdUQVhCZ05WQkFzVEVIZDNkeTVrYVdkcFkyVnlkQzVqCmIyMHhMVEFyQmdOVkJBTVRKRVZ1WTNKNWNIUnBiMjRnUlhabGNubDNhR1Z5WlNCRVZpQlVURk1nUTBFZ0xTQkgKTWpDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTzhVZjQ2aS9ucjdwa2dURHFuRQplU0lmQ0ZxdlBuVXEzYUYxdE1KNWhoOU1uTzZMbXQ1VWRIZkJHd0M5U2krWGpLMTJjalpneE9ic0w2Umcxbmp2Ck5oQU1KNEp1bk4wSkdHUkpHU2V2YkpzQTNzYzY4bmJQUXp1S3A1SmM4dnByeXAybXRzMzhwU0NYb3JQUitzY2gKUWlzS0E3T1NRMU1qY0ZOMGQ3dGJyY2VXRk5iemdMMmNzSlZRZW9nT0JHU2UvS1pFSVp3NmdYTEtlRmU3bXVwbgpOWUpST2kyaUMxMStIdUY3OWlBdHRNYzMyQ3Y2VU94aXhZLzNaVitMenBMbmtsRnE5OFhPUmd3a0lKTDFIdXZQCmhhOHl2YitXNkppc2xaSkwrSExGdGlkb3htSTdRbTNaeUlWNjZXNTMzRHNHRmltRkprejN5MEdlSFd1U1ZNYkkKbGZzQ0F3RUFBYU9DQVU4d2dnRkxNQjBHQTFVZERnUVdCQlI0MzVHUVgrN2VyUGJGZGV2VlRGVlQ3eVJLdGpBZgpCZ05WSFNNRUdEQVdnQlJPSWxRZ0dKWG00MjdtRC9yNnVSTHRCaGVQT1RBT0JnTlZIUThCQWY4RUJBTUNBWVl3CkhRWURWUjBsQkJZd0ZBWUlLd1lCQlFVSEF3RUdDQ3NHQVFVRkJ3TUNNQklHQTFVZEV3RUIvd1FJTUFZQkFmOEMKQVFBd05BWUlLd1lCQlFVSEFRRUVLREFtTUNRR0NDc0dBUVVGQnpBQmhoaG9kSFJ3T2k4dmIyTnpjQzVrYVdkcApZMlZ5ZEM1amIyMHdRZ1lEVlIwZkJEc3dPVEEzb0RXZ000WXhhSFIwY0RvdkwyTnliRE11WkdsbmFXTmxjblF1ClkyOXRMMFJwWjJsRFpYSjBSMnh2WW1Gc1VtOXZkRWN5TG1OeWJEQk1CZ05WSFNBRVJUQkRNRGNHQ1dDR1NBR0cKL1d3QkFqQXFNQ2dHQ0NzR0FRVUZCd0lCRmh4b2RIUndjem92TDNkM2R5NWthV2RwWTJWeWRDNWpiMjB2UTFCVApNQWdHQm1lQkRBRUNBVEFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBb0JzMWVDTEtha0x0VlJQRlJqQklKOUxKCkwwczhaV3VtOFU4LzFUTVZrUU1CbitDUGI1eG5DRDBHU0E2TC9WMFpGck1OcUJpcnJyNUIyNDFPZXNFQ3Z4SWkKOThiWjkwaDkrcS9YNWVNeU9EMzVmOFlUYUVNcGRuUUNuYXdJd2lIeDA2LzBCZmlUaitiL1hRaWgrbXF0M1pYZQp4TkNKcUtleGRpQjJJV0dTS2NnYWhQYWNXa2svQkFRRmlzS0lGWUVxSHpWOTc0UzNGQXovOExJZkQ1OHhuc0VOCkdmenlJRGtIM0pyd1laOGNhUFRmNlpYOU0xR3JJU044SG5XVHRkTkNIMnhFYWpSYS9oOVpCWGpVeUZLUXJHazIKbjJoY0xyZlpTYnluRUMvcFN3L0VUN0g1bld3Y2tqbUFKMWw5ZmNuYnFrVS9wZjZ1TVFtbmZsMEpRakpOU2c9PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==tls.key: >-LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBd3paT1J4eGdMUFVrOS9NYnpFdXI3anBjc0pFUlJEMU0yeVo4SEtVV25oWVFwbHNDCi9XankzdEhaelExTnpOeHNiMnJ0WWh6UldlbHVEUmZidnliQjFMV3hQQXlIM1hyLzQ4ZEJHdkM4bGYwV25sTkQKVnZHc0VSelNnb2lmRTlKeEZ5NFJUbUltOVdDT0hSdTFKVVFreEp1QTZGSENHVTBlL1orZGp3aXdXSXlSdEpOVwo2NTRZVVBUaVFSa3NvQTlvMVlScVdVd1pFVTFUV2V3YjJELzN3TVJMUkEzZjEvdHdkZGsxREtJbUc5aVJyWEdWCm5WTVFBdERrYXZHbU4xTW5LZ3FoaFlBNzVGT1Y1ZVdGSHVGMlFReDA1RVhRYlFjam8wS2wrcG1oR3d3MFo5Z1YKTTB3NXZTMVRIMDR0RGEvNDJONmdKSG91M3EzM1VabFoyTEZWRlFJREFRQUJBb0lCQUI4TVNwdnR5L0FxbDFRbQpZdlAxenlVblBDbkxFT041R25tNm43L1FsQTNWdFpVMzRYeGJqbEZaTUJwNGRMalNFQjhTY3lvSktsVHlGeEpYCkNwalcrYm95b2J0S3hPczVqbXgwZXdybFlpRTY3VGVHUjY0UzV3cWJ1bkdQZURtblhWeFI4K2V6SGI0bU9zUXYKYlhxOVlWbXgzK2xUWTVzeGxHM0RUc1I2bmMyZldzSUtGZWtKTy9mbzJPczZ4UjFaelZoaTNQK1NoZ2grZGhDRgpRZHI5Vm1LQ3JpT3F0TktWeDMzV1A2NUMzcGpUTzdNZUt4TkFPa2R2NVNDcVFGTWlORFk5a3ZiYitzd0NSd1BkCksydk5rR0FsZnBkNWZ1SkNvN1FNancvUDFTaDFiQjRXNm14TGZueEk3WmxGekFRa3FlVkxVaHl5K0x1NWJHcG0Kb2NLWUZsc0NnWUVBNXArNW95RHpEZG9WYkV0Z0FTb0VrcDdHVkcxQVVjeFdGbXNhdDB0TmUza3hOallzeXhOegoycUozUUdjQ3ppWlp6NUdFbkVlUTU4WWxucXU5VmppSWgrK3pob1VEM3RQUlNSbndtekJkNFNEM3hSU2NaWjNNCnpLRis4QU5LOHVIVUp4RlFNR0txYUtaTkk1TnA4dFlYZFlvNEpxYmFLaStzbDBJYSthdzdxS2NDZ1lFQTJMRVgKaTV2VU1OdzJKaXpYNWVScW9MZkFJSDhsbk9EcjFCbDFVaC9saFZ1ekpEbEVuMk9LUmM2R3NtSlc0aFE1UnhlZQpZS2tTQm5Ob284OU9hMzR1MUlNT0dKOElsWm9FbWhWTTNqZWhEL0d6NE12d1ZsNlBEMks0Y29jYnE2QVM1Q0JRClpvSzBvcERxZXF1VGlvUm5Bdkl0VDRlWUpnVFRlQ2g0U3d2dkQrTUNnWUFGU3VVWHVVbmFwNGFXVmFSK1lsaDQKaE94SVE3bVdKdnBTeVdKemttYlV6cE15aTB1NzNWWnJUZzh1aXk2bFRId0RKM1BEb21EUThOc3NLUVRQVmJ6TQpZZFBjNG5DVVRJZ2hCVmRnT0Z2dkxyS0E4MWdqZk51V1ZwNXpJNkEwc3JvTHEzb0xvamdHN3NvV1p1dW5od0pDCjBFazVtZHFuM1RBNHlHdVdEejNQUVFLQmdIL1lhL1hZYUdhelpkYzhHZHp1Mk9JZHgyTGs0VUlmaWNQSGlXcDgKbXlRRktEbzA5NEc2YnJnazAxK25tVzhsVTIzWVIzN3NBVkNCQXJteTg2ZUQrUWswa1RxQmljVUo2N0VrNUFjdgpkdjA3TTA5cncwNlIxNEhTVXRSdlZpbjU5V3RXalZrTndKa3hPc1pKT0hFL0VLK3lSbjFubUtMRnNpWndhaGlNCjMrelZBb0dCQUw3cXdIbVdyTnpOY2lTVVlDb1ZualhxSVhlN0luZkw5TFVjRit1UnI3bm80WGlPT2VhcG9TenEKbEQ0cVNMQXplV2ZrcjFMOW8wS3hDQnhMSFlydWtQK0I2bkF4T1VsUER2NVNsd0ZZSVZPLzVPZ2VpMmRGV3RnMwptQ1ZBU0tzaDVmTkNPWXNEZGV2MmYwRUJsaGtCeE42ankxemFMWTVUSFN0bFJwWUZ2emtLCi0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
type: kubernetes.io/tls
注意事项:
- 本示例
Ingress使用到ingressClassName: nginx-ingress,基于Kuboard提供的一种快速安装ingress-nginx的方法。
5.2 知识点 Ingress SSL 终止
默认情况下,SSL在ingress controller中被终止,所以从controller到pod的所有流量都是没有TLS(解密的流量)。
如果想要全程SSL,你可以通过正在使用的ingress controller添加支持的annotation。例如,在本章(应用已配置好SSL)示例Nginx ingress controller里面,为了让SSL流量到达应用,你可以使用nginx.ingress.kubernetes.io/backend-protocol: "HTTPS"的annotation。
重要知识:
- 更多关于
Ingress-Nginx Controller配置示例,请见:https://kubernetes.github.io/ingress-nginx/examples/rewrite/
六、效果
6.1 通过ingress访问
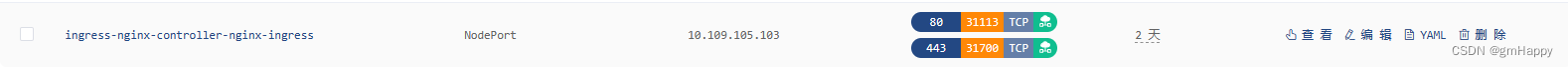
- 本示例K8S集群安装在内网环境,通过部署在外网的
nps服务和内网的npc服务穿透至内网集群的nginx-ingress端口。- 外网的
nps服务外网端口9091,对应ingress-nginx-controller容器443的外部访问端口31700。- 注意外网部署
nps服务的 安全策略 ,保证网络可达。

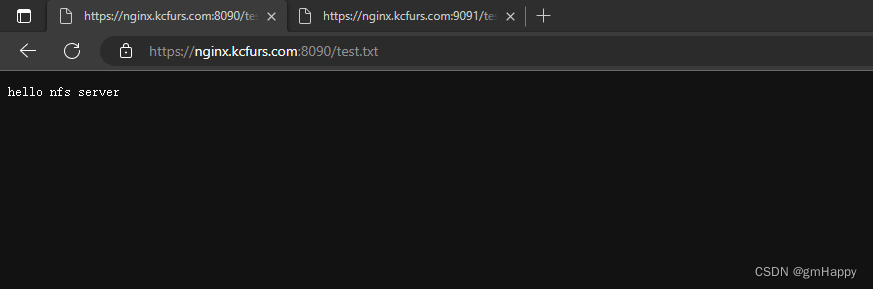
6.2 通过服务的nodePort访问
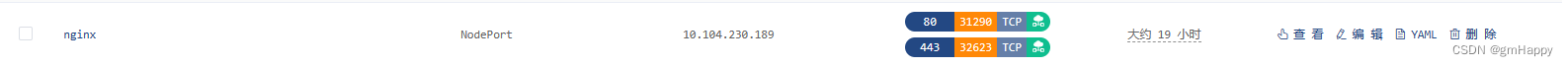
- 本示例K8S集群安装在内网环境,通过部署在外网的
nps服务和内网的npc服务穿透至内网集群的nodePort端口。- 外网的
nps服务外网端口8090,对应nginx服务443的外部访问端口32623。

本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!